1. Experiment Overview
1.1 Experiment Introduction
Information gathering is one of the most critical phases in penetration testing. This experiment focuses on introducing tools for gathering information, with each tool’s usage steps illustrated with screenshots. At this stage, users need to collect basic information about the target machine. The more information you gather, the higher the success rate of your penetration testing. The Kali system comes pre-installed with several penetration testing tools to help users familiarize themselves with the basic steps of information gathering.
Note: Due to the high cost of configuring cloud hosts for this experiment, usage is limited to a maximum of six attempts per experiment.
1.2 Knowledge Points
Key knowledge points for this experiment:
- Using tools to scan ports open on the target host
- Gathering basic information about the target host’s operating system
- Collecting information about network services provided by the target site
- Comprehensive analysis of information to enable attack strategies
1.3 Experiment Environment
The experiment provides a Kali environment and a target machine called Metasploitable2. First, log in to the provided experimental cloud environment, then start both the Kali and Metasploitable2 systems via the terminal. SSH access to Kali is required for the experiment.
Introduction to Metasploitable2
Metasploitable2 is a specially crafted Ubuntu-based virtual system designed for testing security tools and simulating common vulnerabilities. Version 2 is available for download and includes more exploitable vulnerabilities compared to its predecessor. This version is compatible with VMware, VirtualBox, and other virtual platforms. By default, it is configured with one network adapter set to NAT and Host-only modes.

2. Scanning Ports Open on the Target Host
2.1 Port Scanning on the Target Host
During a penetration test, it’s essential to identify the open ports on the target host. Two commonly used port scanning tools available by default in Kali Linux are: Nmap and Zenmap. Below is an introduction to the usage of these tools.
2.1.1 TCP Port Scanning Tool: Nmap
Nmap is a network exploration and security auditing tool. It enables system administrators and individuals to scan large networks, identify active hosts, and discover the services they provide. Nmap supports numerous scanning techniques, including UDP, TCP Connect(), TCP SYN (half-open), FTP Proxy (Bounce Attack), Reverse Flag, ICMP, FIN, ACK Scans, Xmas Tree, SYN, and Null Scans.
Start by logging into the Kali system via ssh. The password is toor.
ssh root@kaliAfter logging in, you’ll see the following illustration:
To identify the target machine’s IP address, use the ping command:
ping targetFor example, the target machine’s IP address in this demonstration is 192.168.122.102.
2.1.2 Using the Powerful Scanning Tool: Nmap
Nmap provides four core functions:
- Host Discovery
- Port Scanning
- Version Detection
- Operating System
2.2.1 Introduction to the Scanning Tool Zenmap
Zenmap is an official graphical user interface (GUI) for Nmap, a security scanner. Written in Python, Zenmap is open-source and free, supporting multiple operating systems (Windows/Linux/Unix/Mac OS, etc.). Its primary purpose is to make Nmap easier to use. Commonly used commands can be saved as profiles for simpler scanning, and it allows users to compare different scan results easily. Zenmap also provides graphical representation of network topology.
Note: The environment in the Lab uses SSH to log into Kali, and graphical interfaces are temporarily unavailable.
3. Obtaining Basic Information About the Target Host OS
3.1 Gathering Basic Information About the Target Host
At this stage, we aim to collect as much basic information about the target host’s operating system as possible. This increases the success rate of penetration tests. The process involves fingerprint detection using active fingerprinting tools such as Nmap’s
-Oand-sVparameters. Although “fingerprinting” sounds complex, it essentially identifies the OS version and application version of the target, helping us investigate vulnerabilities at the OS or application level.3.1.1 Active Fingerprinting Tools
To identify the target host OS, use the following command:
nmap -O # Operating system detectionRun the above command in the Kali terminal to inspect the OS on Kali:
nmap -O 192.168.122.102As shown, the target host:
Running: Linux 2.6xis detected as a Linux OS.To reiterate, the target machine IP address is:
192.168.122.102, while the Kali host address is:192.168.122.101.To gather more OS details of the target host, use the following command:
nmap -sVExecute the command in the Kali terminal to retrieve target host details:
nmap -sV 192.168.122.1023.1.2 Passive Fingerprinting Tools
Passive fingerprinting tools do not send specific probing data to the target. Instead, they analyze received data passively, avoiding detection. p0f is a powerful tool for network analysis, capable of identifying details such as NAT, load balancing, and application proxy usage.
Key information identified by p0f includes:
- OS type and ports
- NAT mode detection
- Use of firewalls
- Load balancing mode
Usage format for p0f:
p0fExecute the following command in the Kali terminal to analyze the target host using p0f:
p0f 192.168.122.1023.1.3 Stealth Scan (TCP Half-Open Scan)
Stealth scanning with a TCP half-open connection can be performed with the following syntax:
nmap -sSPerform a stealth scan in the Kali terminal using this command:
nmap -sS 192.168.122.102This technique is less likely to be detected and typically leaves no records on the target host.
3.1.4 TCP Connect Scan
TCP connect scanning, with the following syntax:
nmap -sTRun the following command in the Kali terminal for a TCP connect scan:
nmap -sT 192.168.122.102This type of scan will be logged by most systems but can provide more information compared to stealth scans.
4. Gathering Network Service Details from Target Sites
4.1 Retrieving Network Service Information
Acquire details about network services offered by the target site. Collecting extensive information about the network services running on the target machine improves the probability of penetration test success.
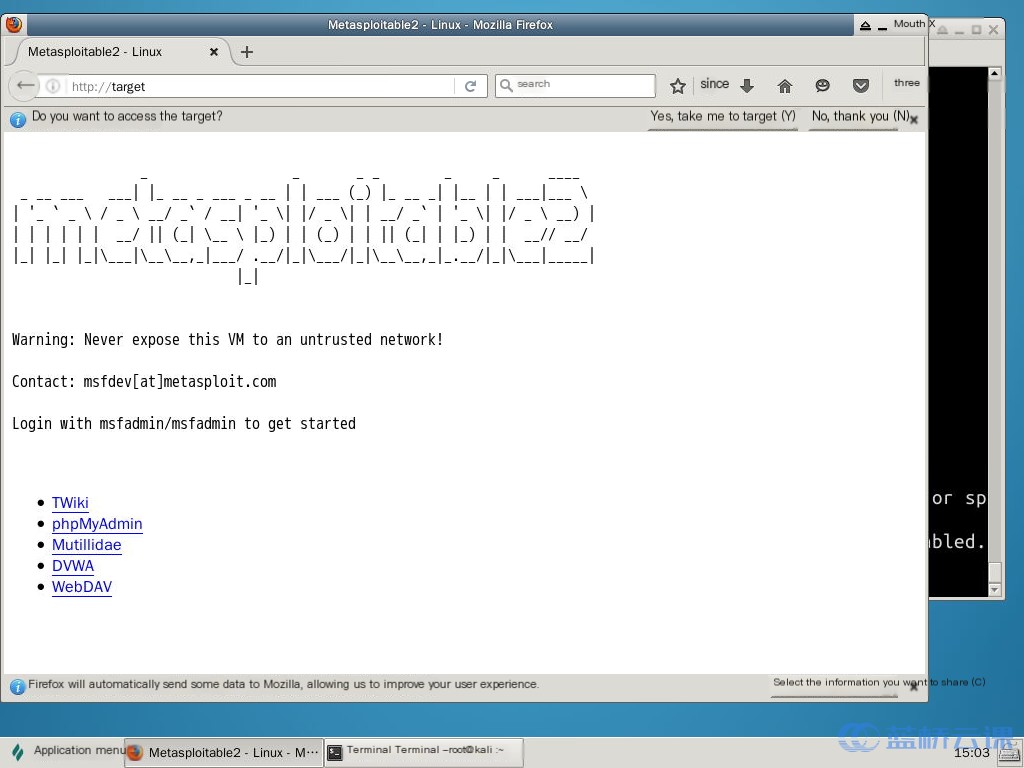
Open Firefox browser and enter
http://targetin the address bar. Test if the target machine can be accessed. If successful, you will see the following:4.1.1 Scanning Specific Ports of the Target Host with amap
The tool amap is used to scan specific ports of a host. The usage is as follows:
amap -bqv <target IP> <port>In the Kali terminal provided by Shiyanlou, enter the command to scan the target host’s port 21:
amap -bqv 192.168.122.102 214.1.2 Enumerating Users with smtp-user-enum
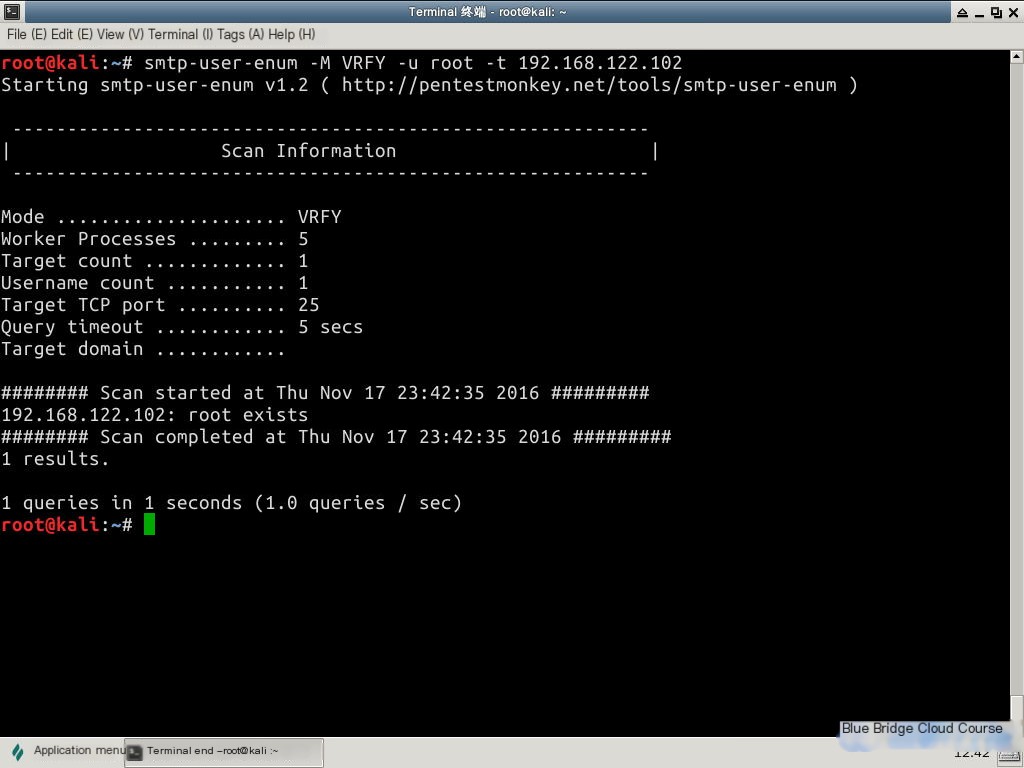
The tool smtp-user-enum is primarily used for enumerating SMTP users. Usage:
smtp-user-enum -M VRFY -u root -t <target IP>In the Kali terminal provided by Shiyanlou, enter the command to enumerate SMTP users:
smtp-user-enum -M VRFY -u root -t 192.168.122.1025. Summary
In this experiment, we explored a variety of commonly used security tools to gather information on the target host. We practiced the following concepts:
- Utilizing tools to scan open ports on the target host
- Retrieving essential information like the target host’s operating system
- Gathering details on network services provided by the target site
- Analyzing information collectively for potential exploitation