Note: This experiment was tested separately using Kali and CentOS 6.8. Unfortunately, the experiment could not be fully completed on Kali due to difficulties encountered during the process, while it was successfully completed on CentOS 6.8.
Software used in the experiment:
https://download.csdn.net/download/weixin_52553215/88800055
[Experiment Objective]
Understand the basic principles of IDS;
Master the advanced IDS implementation using Snort;
[Experiment Content]
1. Experimental environment: Kali
2. Implementation task: Snort
[Experiment Environment]
1. Virtual platform: VMware Workstation
2. Operating system: Kali, CentOS 6.8
3. Snort: Open-source intrusion detection system
[Experiment Steps]
Kali:
1. Install Kali, and check the network
Installation process skipped.
1.1 Change the source
Execute the following command:
vim /etc/apt/sources.list
Comment out the original sources
University of Science and Technology of China (USTC) Kali mirror source
deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
deb-src http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
Paste the above sources in the position shown below:
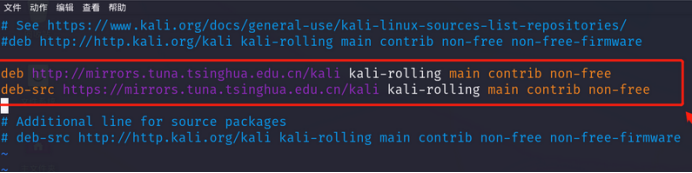
Save and exit the configuration
Execute the following commands:
apt-get update
apt-get upgrade
apt-get dist-upgrade
apt-get clean
2. Install the intrusion detection system Snort
2.1 Install DAQ dependencies
Execute the following commands:
sudo apt-get install flex
sudo apt-get install bison
sudo apt install aptitude
sudo aptitude install libpcap-dev
2.2 Install DAQ
Execute the following commands:
wget https://www.snort.org/downloads/snort/daq-2.0.7.tar.gz
tar xvfz daq-2.0.7.tar.gz
cd daq-2.0.7
./configure && make && sudo make install
make
2.3 Install Snort dependencies
Execute the following commands:
sudo su
aptitude install libpcre3-dev
aptitude install libdumbnet-dev
aptitude install zlib1g-dev
apt install openssl
apt-get install libssl-dev
Install LuaJIT:
sudo wget http://luajit.org/download/LuaJIT-2.0.5.tar.gz
sudo tar -zxvf LuaJIT-2.0.5.tar.gz
cd LuaJIT-2.0.5/
sudo make && sudo make install
LuaJIT-2.0.5 installation complete:
2.4 Install Snort
Execute the following commands:
wget https://www.snort.org/downloads/snort/snort-2.9.20.tar.gz
tar xvfz snort-2.9.20.tar.gz
cd snort-2.9.20
./configure –enable-sourcefire && make && sudo make install
Error: fatal error: rpc/types.h: No such file or directory
Execute the following commands:
sudo apt-get install -y libtirpc-dev
sudo ln -s /usr/include/tirpc/rpc/* /usr/include/rpc
Error: fatal error: netconfig.h: No such file or directory
Execute the following command:
sudo ln -s /usr/include/tirpc/netconfig.h /usr/include
Execute the following command:
snort
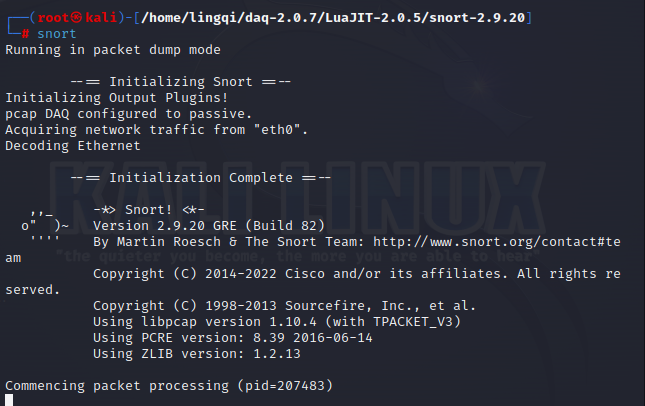
Successfully installed
3. Configure Snort
3.1 Create necessary directories
Snort installation directory
sudo mkdir -p /etc/snort/rules/iplists
sudo mkdir -p /etc/snort/preproc_rules
sudo mkdir /usr/local/lib/snort_dynamicrules
sudo mkdir /etc/snort/so_rules
Store filtering rules and server black/white lists
sudo touch /etc/snort/rules/iplists/default.blacklist
sudo touch /etc/snort/rules/iplists/default.whitelist
sudo touch /etc/snort/rules/so_rules
Create log directory
sudo mkdir /var/log/snort
sudo mkdir /var/log/snort/archived_logs
Adjust permissions
sudo chmod -R 5775 /etc/snort
sudo chmod -R 5775 /var/log/snort
sudo chmod -R 5775 /var/log/snort/archived_logs
sudo chmod -R 5775 /etc/snort/rules/so_rules
sudo chmod -R 5775 /usr/local/lib/snort_dynamicrules
3.2 Copy files to /etc/snort
cd /home/lingqi/daq-2.0.7/LuaJIT-2.0.5/
cp ./snort-2.9.20/etc/*.conf* /etc/snort
cp ./snort-2.9.20/etc/*.map /etc/snort
cp ./snort-2.9.20/etc/*.dtd /etc/snort
cp ./snort-2.9.20/src/dynamic-preprocessors/build/usr/local/lib/snort_dynamicpreprocessor/* /usr/local/lib/snort_dynamicpreprocessor/
3.3 Modify the default configuration
Open the configuration file
sudo vim /etc/snort/snort.conf
Modify paths
var RULE_PATH /etc/snort/rules
var SO_RULE_PATH /etc/snort/so_rules
var PREPROC_RULE_PATH /etc/snort/preproc_rules
var WHITE_LIST_PATH /etc/snort/rules/iplists/
var BLACK_LIST_PATH /etc/snort/rules/iplists/
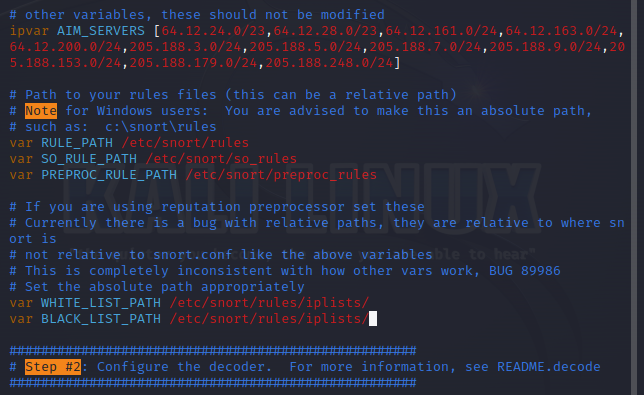
Enable black/white lists
3.4 Install rules package
wget Snort – Network Intrusion Detection & Prevention System
sudo tar zxvf snortrules-snapshot-29181.tar.gz -C /etc/snort
Error:
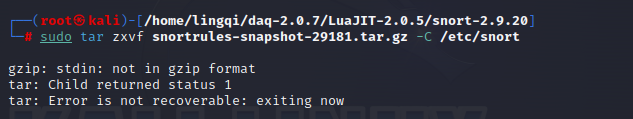
The error description indicates `stdin: not in gzip format`, which clearly points to the problem—the file is not in gzip format. You can use the `file` command to check the specific file information:
Finding:
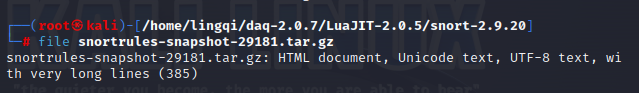
This file was identified as an HTML document. Return to the Snort website and download the file directly.
sudo tar zxvf snortrules-snapshot-29181.tar.gz -C /etc/snort
sudo cp /etc/snort/so_rules/precompiled/RHEL-8/x86-64/2.9.18.1/* /usr/local/lib/snort_dynamicrules/
4. Runtime Testing
sudo snort -T -c /etc/snort/snort.conf
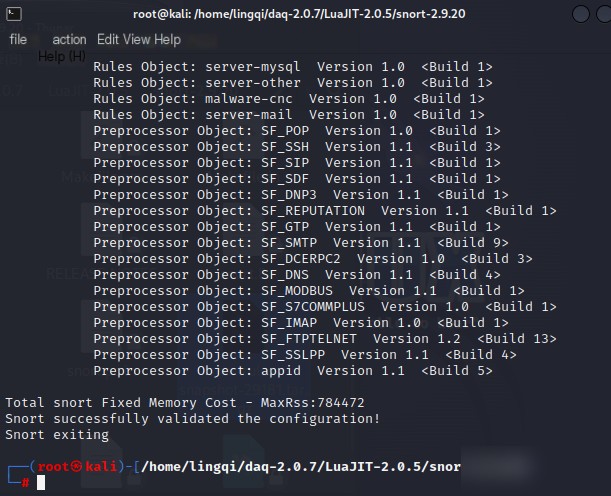
CentOS:
1. Preparations
Install the operating system on a virtual machine using the CentOS-6.8-x86_64-mini image.
By default, the network IP is set to dynamic (automatic) configuration, so it needs to be changed to a static IP address.
ifconfig -a // View network interface configuration information
vi /etc/sysconfig/network-scripts/ifcfg-eth0 // Edit the network card configuration file
To set up a static IP address, replace BOOTPROTO=dhcp with static and add the following content (configure the IP based on your internal network):
IPADDR=192.168.91.128
NETMASK=255.255.255.0
GATEWAY=192.168.91.2
DNS1=192.168.91.2
DNS2=8.8.8.8 // Add additional DNS addresses as per your ISP
Save the changes and restart the network service.
Step 1: Use the `cat /etc/issue` command to check the system version (e.g., CentOS 6.x). Note the version for later use.
Step 2: Back up critical files to ensure you can roll back in case of issues:
1. mkdir /etc/yum.repos.d/bakk // Create a backup folder
2. mv /etc/yum.repos.d/* /etc/yum.repos.d/bakk // Ignore any errors
Step 3: Open and edit the CentOS-Base.repo configuration file:
vim /etc/yum.repos.d/CentOS-Base.repo
Clear the file contents and copy the configuration block below into the file.
Note: If your system version is not 6.7, replace “6.7” in the following block with your actual system version (e.g., 6.8 or 6.x).
CentOS-Base.repo Configuration:
[base]
name=CentOS-$releasever – Base
baseurl=https://mirrors.aliyun.com/centos-vault/6.7/os/$basearch/
gpgcheck=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6
[updates]
name=CentOS-$releasever – Updates
baseurl=https://mirrors.aliyun.com/centos-vault/6.7/updates/$basearch/
gpgcheck=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6
[extras]
name=CentOS-$releasever – Extras
baseurl=https://mirrors.aliyun.com/centos-vault/6.7/extras/$basearch/
gpgcheck=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6
[centosplus]
name=CentOS-$releasever – Plus
baseurl=https://mirrors.aliyun.com/centos-vault/6.7/centosplus/$basearch/
gpgcheck=1
enabled=0
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6
[contrib]
name=CentOS-$releasever – Contrib
baseurl=https://mirrors.aliyun.com/centos-vault/6.7/contrib/$basearch/
gpgcheck=1
enabled=0
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6
Step 4: Clear the YUM cache:
yum clean all
Step 5: Cache the package metadata locally to improve speed when searching and installing software:
yum makecache
At this stage, YUM should be functioning correctly.
yum -y update // Updates the system (this step may take some time)
Step 6: Copy the required software to a specified directory.
Copy the following four files:
– `libdnet-1.12.tgz`
– `daq-2.0.4.tar.gz`
– `snort-2.9.7.0.tar.gz`
– `snortrules-snapshot-2970.tar.gz`
Use WinSCP to transfer these files to the `/usr/local/src/` directory of the CentOS 6.8 system.
At this point, Snort installation preparation is complete.
If you need further assistance setting up Snort or troubleshooting, feel free to ask!html
2. Compile and Install Snort
After completing the preparations, we proceed to officially install Snort. Compiling and installing Snort requires the following 10 steps.
Step 1: Install the basic environment and dependencies.
yum install -y gcc gcc-c++ flex bison zlib-devel zlib-static libxml2 libpcap pcre-devel pcre-static libpcap-devel.x8664 tcpdump git libtool curl man make
Note: If PCRE is not installed, the following error will appear during precompilation. For example, when running ./configure, the error is shown below:
ERROR! Libpcre library not found, go get it from http://www.pcre.org
Step 2: Extract the libdnet, DAQ, and Snort installation packages.
During the server installation and configuration process, you may download the latest source packages from the official website, but this can lead to dependency issues that may prevent successful installation. Certain software (like Snort) requires the DAQ (Data AcQuisition) library to be installed first, which in turn depends on libdnet. Follow the steps below:
cd /usr/local/src
tar -zxvf libdnet-1.12.tgz
tar -zxvf daq-2.0.4.tar.gz
tar -zxvf snort-2.9.7.0.tar.gz
You must install the libdnet, DAQ, and Snort packages in sequence:
● Install libdnet-1.12.tgz.
cd /usr/local/src/libdnet-1.12/
./configure
make && make install
● Install DAQ.
wget http://www.tcpdump.org/release/libpcap-1.0.0.tar.gz
tar xvfz libpcap-1.0.0.tar.gz
cd libpcap-1.0.0/
./configure
make
make install
cd daq-2.0.4
./configure
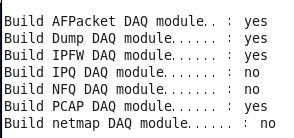
After verifying the compilation environment, you should see that the statuses of AFPacket DAQ module, Dump DAQ module, IPFW DAQ module, and PCAP DAQ module are all “yes.” Only then can you proceed with building the software package.
make && make install //Compile and install
● Install Snort 2.9 (ensure you properly install libdnet, DAQ, and zlib beforehand).
cd /usr/local/src/snort-2.9.7.0
./configure –enable-sourcefire
make && make install
During compilation, no error messages should appear if the installation is done correctly.
Step 3: Add a user and group.
Create a user and group, and set appropriate permissions. Files extracted under the root account are associated with root by default, so you need to modify ownership and permissions to align with Snort users.
groupadd -g 40000 snort //Create a new Snort group
useradd snort -u 40000 -d /var/log/snort -s /sbin/nologin -c SNORT_IDS -g snort
//Add the Snort user to the Snort group, create the /var/log/snort directory, and disallow system login for this user
Step 4: Configure Snort.
● Create a new directory /etc/snort/.
mkdir /etc/snort/
● Extract snortrules-snapshot-2970.tar.gz to the /etc/snort/ directory.
cd /etc/snort
tar –zxvf /usr/local/src/snortrules-snapshot-2970.tar.gz –C . (This step is critical; extract to the current directory)
After executing this command, you should see four directories—etc, preproc_rules, rules, so_rules—within /etc/snort/.
cp /etc/snort/etc/sid-msg.map /etc/snort
● Copy the Snort compressed package (snort-2.9.7.0.tar.gz), extract it, and move its contents to the /etc/snort/ directory.
cd /etc/snort/
cp /usr/local/src/snort-2.9.7.0/etc/* .
● Set ownership and group permissions for /etc/snort and its subdirectories.
chown -R snort:snort *
● Create black and white list rule files.
touch /etc/snort/rules/white_list.rules /etc/snort/rules/black_list.rules
Create two files, white_list.rules and black_list.rules, under /etc/snort/rules.
● Edit the configuration file snort.conf, modifying the following lines:
vi /etc/snort/snort.conf
● Configure variables in snort.conf.
The snort.conf file includes many variables and options, which apply to all rules in the rules directory. As a beginner, focus on two key variables:
$HOME_NET: The network you want to monitor (expressed in CIDR format).
$EXTERNAL_NET: External, untrusted networks.
Both variables default to “any,” meaning “monitor everything.” However, you should modify them as needed. For example, set your network segment as follows. In this example, the monitored segment is 192.168.11.0/24:
ipvar HOME_NET [192.168.11.0/24] //To monitor all traffic, you can leave it as “any.”
Replace ipvar EXTERNAL_NET any with ipvar EXTERNAL_NET $HOME_NET.
If your network segment also includes DNS, SMTP, HTTP, SQLServer, or SSH services, modify the configuration as follows:
ipvar DNS_SERVERS $HOME_NET
ipvar SMTP_SERVERS $HOME_NET
ipvar HTTP_SERVERS $HOME_NET
ipvar SQL_SERVERS $HOME_NET
ipvar SNMP_SERVERS $HOME_NET
ipvar SSH_SERVERS $HOME_NET
Note: It is not mandatory to modify $HOME_NET and $EXTERNAL_NET. Beginners can use the default “any” values. However, relative rule paths must be changed to absolute paths to avoid startup errors.
Change the following lines:
Line 104: var RULE_PATH ../rules → var RULE_PATH /etc/snort/rules
Line 105: var SO_RULE_PATH ../so_rules → var SO_RULE_PATH /etc/snort/so_rules
Line 106: var PREPROC_RULE_PATH ../preproc_rules → var PREPROC_RULE_PATH /etc/snort/preproc_rules
Line 113: var WHITE_LIST_PATH ../rules → var WHITE_LIST_PATH /etc/snort/rules
Line 114: var BLACK_LIST_PATH ../rules → var BLACK_LIST_PATH /etc/snort/rules
● Set the log path.
Line 186: config logdir:/var/log/snort/
● Configure output plugins.
Use database plugins (spo_database.c and spo_database.h) to store logs in a database. The following example writes alerts to the alert file and stores logs in the unified2 binary format for Barnyard2.
Modify Line 521 as follows:
output unified2: filename snort.log, limit 128
Remember to remove any comment marks, save, and exit. With the snort.conf file configured, move on to the next step.
Step 5: Create the snort_dynamicrules directory and set ownership and permissions.
mkdir -p /usr/local/lib/snort_dynamicrules
chown -R snort:snort /usr/local/lib/snort_dynamicrules
chmod -R 755 /usr/local/lib/snort_dynamicrules
Step 6: Create a symbolic link named Snort in the /usr/sbin/ directory.
cd /usr/sbin
ln -s /usr/local/bin/snort snort
Step 7: Add a test rule.
While many rule files are copied during Snort’s installation, most of these rules are commented out by default. Create a simple test rule as follows:
vi /etc/snort/rules/local.rules
Add the following rule:
alert icmp any any -> $HOME_NET any (msg:"ICMP Packet Detected";sid:1000003;rev:1;)
Save and exit. You’ve just written your first detection rule.
Step 8: Test Snort.
snort -T -i eth0 -u snort -g snort -c /etc/snort/snort.conf
Note: The -T parameter runs a test and exits Snort after completion.
If configured properly, the system will display the following output upon startup:
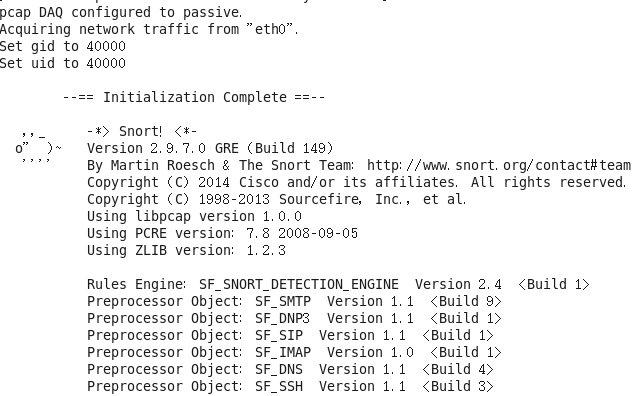
html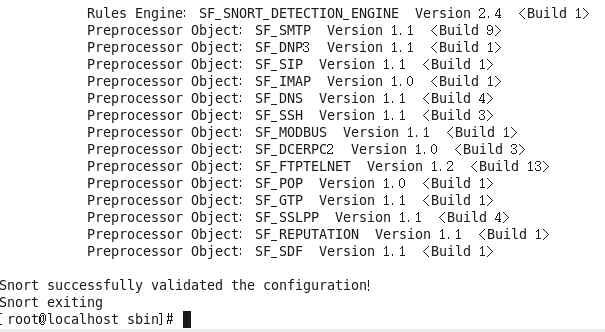
If you see the message “Snort successfully validated the configuration!” it means the installation and configuration were successful.
Step 9: Test using the `ping` command.
The purpose of testing with the `ping` command is to generate alerts from Snort. The `ping` command uses the ICMP protocol, and Snort uses the `libpcap` library to capture ICMP packets. Below are the operations performed on the Snort host:
snort -i eth0 -c /etc/snort/snort.conf -A fast
Note: The `-A fast` option in the command above is defined as follows:
The `-A fast` mode provides alert information that includes:
A timestamp
Alert message
Source/Destination IP addresses
Ports
After entering the above command, alert records will be saved in `/var/log/snort/alert` and `/var/log/snort/snort.log.timestamp` (the latter being a binary file for packet storage, which cannot be read using the `tail` command). Use the following command to directly view alerts:
cd /var/log/snort/
tail -f /var/log/snort/alert //View alerts
Example:
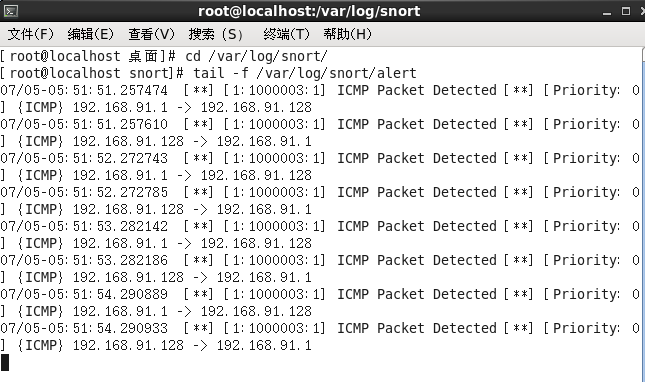
The file `/var/log/snort/alert` is a plain text file and can be opened with any text editor.
The next step is to store these alerts in a database.
Note: If a path has not been correctly configured in steps 6 or 7 above, Snort may fail to locate its dynamic rules files on startup, triggering a fatal error and causing the program to exit abnormally.
ERROR: parser.c (5047)
Understanding the Process: Understanding the `/etc/snort/sid-msg.map` file is crucial. A signature entity in Snort represents a structured list of alert messages, where details such as event information are standardized using rule identifiers (`sig_id`), descriptions (`sig_name`), classification identifiers (`sig_class_id`), priority values (`sig_priority`), version numbers (`sig_rev`), and internal IDs in Snort (`sig_sid` and `sig_gid`).
The specific details of `sig_class_id` and `sig_priority` are described in the `classification.config` file. The signature IDs `sig_sid` and `sig_gid` map events to rules within the `/etc/snort/gen-msg.map` file.
Classification Explanation:
The file `classification.config` originates from the `snortrules-snapshot-2970.tar.gz` archive.
Here, the term “classification” primarily refers to categories of issues. The Snort installation package available on the official website includes a user guide that contains a detailed classification table.
Within this context, it indicates how intrusion signatures are categorized. During Snort rule development, each intrusion signature is classified by setting the `classification` attribute with an appropriate value from the classification table.
The `classification.config` configuration file is referenced by both `/etc/snort/snort.conf` and `/etc/snort/barnyard2.conf`, which are key configuration files.
Later, during experiments involving BASE (Basic Analysis and Security Engine), you will observe the importance of classifications.
Additionally, basic users should understand that Snort reserves the range 1–1,000,000 for its internal use, while IDs higher than 1,000,000 can be assigned by users. This is a convention, not a requirement. When creating custom rules, entries in the `sid-msg.map` file must include custom rule IDs and corresponding alert messages. The attributes `sig_reference` and `sig_class` extend the information of `sig_id` and `sig_class_id` respectively.
3. Storing Snort Alerts in a MySQL Database
To store Snort alerts in a MySQL database, the following steps are required:
Step 1: Install the MySQL database and PHP extensions.
yum install -y mysql-server mysql-devel php-mysql php-pear php-gd libtool php-imap php-ldap php-odbc php-xml php-pecl-apc
chkconfig --level 235 mysqld on //Enables the MySQL service for run levels 2, 3, and 5
/etc/init.d/mysqld start
Step 2: Assign a password to the database administrator (`root`). (For convenience during debugging, a numeric password `123456` is used here.)
/usr/bin/mysqladmin -u root password '123456'
Note that the `root` user will use this password when accessing phpMyAdmin.
Step 3: Create a Snort database and set access permissions.
mysql -u root -p //Connect to MySQL
Enter the password `123456` set in Step 2.
mysql> CREATE DATABASE snort; //Create a new database
mysqlBased on your request, I'll translate the plain text in the post while retaining the original formatting, HTML tags, and American English terminology.
Spawning daemon child…
My daemon child 12903 lives…
Daemon parent exiting (0)
Snort is now quietly running in the background (“-D” flag enables daemon mode).
● Testing Barnyard2.
The following command is used to test whether Barnyard2 is functioning correctly:
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort/ -f snort.log -w /var/log/snort/barnyard2.waldo -g snort -u snort -T
The command output is as follows:
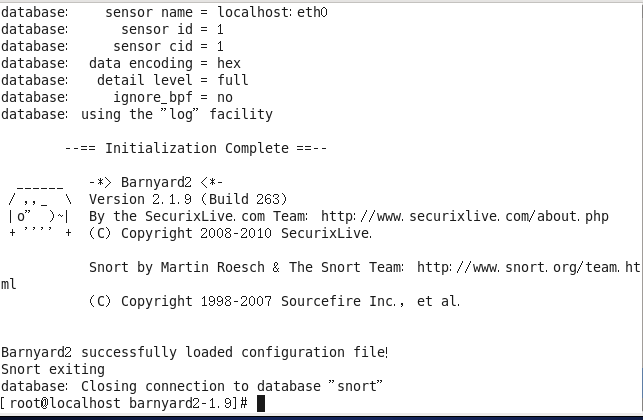
If you see the output shown above on your machine, it means Barnyard2 is running correctly, and we can proceed to the next steps.
Similarly, after pinging the host, officially initiate the Barnyard2 process using the following command:
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort/ -f snort.log –w /var/log/snort/barnyard2.waldo
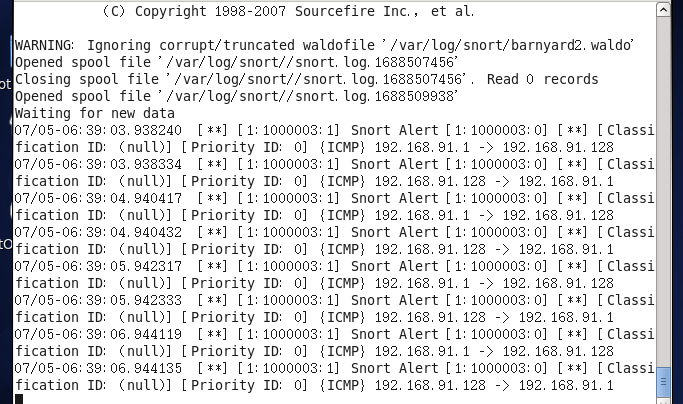
The explanations for the command parameters are detailed as follows:
● -c: This flag specifies the path to the Barnyard configuration file. This is a mandatory parameter.
● -d: Specifies the path to the Unified format files, here set to /var/log/snort/. All the Unified files must be stored in this directory. This parameter is also mandatory.
● -f: This flag designates the filename of the Unified file Barnyard will process in ongoing mode. Snort appends a UNIX timestamp to each generated Snort Unified file; removing the timestamp suffix gives you the filename.
As observed in the results above, Snort creates log files in /var/log/snort/ in the format snort.log.timestamp. Why must the format be snort.log.XXXXXXX? It is due to the configuration in step 5 of snort.conf:
output unified2:filename snort.log,limit 128
This defines the format of the output log files. If you want to change the format to unified2.alert.XXXXX, modify the configuration line as follows:
output unified2:filename unified2.alert,limit 128
Correspondingly, the value following the -f flag would need to be unified2.alert instead of snort.log, so ensure the naming matches accordingly.
● -w: Enables file-checking functionality and specifies the filename (also known as a waldo file). This file keeps track of the last processed alert. Without a waldo file, Barnyard would need to load the entire log file each time. This parameter facilitates transferring the alert information to the intrusion detection database.
In the /var/log/snort directory, you’ll find some snort.log+timestamp binary files, which are generated by Snort’s output plugin.
Step 5. Use the following command to verify whether alert data has been stored in the database:
mysql -u snort -p -D snort -e “SELECT COUNT(*) FROM event”
The actual operational result is shown below:
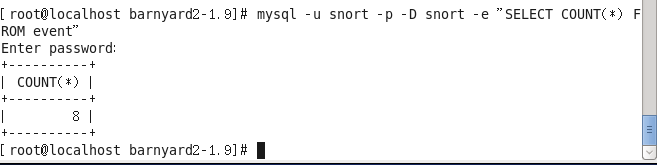
If you see no numbers under count(*), it means alert data has not been stored in the database, and you’ll need to revisit and verify the configuration steps.
Below is the most crucial command for fully starting Barnyard2:
[root@localhost ~] barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort/ -f snort.log -w /var/log/snort/barnyard2.waldo -g snort -u snort
4. Setting Access Permissions
In a simple test environment, this step can be ignored.
Suppose we want to allow only a specific IP address to access ports 22 and 80 on the Snort server. Perform the following steps on the Snort host:
Deny access on ports 22 and 80 for all IP addresses:
iptables -I INPUT -p tcp –dport 80 -j DROP
iptables -I INPUT -p tcp –dport 22 -j DROP
Allow access for IP address 192.168.11.2 to access ports 22 and 80 on the Snort server:
iptables -I INPUT -s 192.168.11.2 -p tcp –dport 80 -j ACCEPT
iptables -I INPUT -s 192.168.11.2 -p tcp –dport 22 -j ACCEPT
Save the iptables rules:
service iptables save
Restart the firewall:
service iptables restart
5. Setting Up BASE for Visualized Intrusion Detection
If all previous steps are completed successfully, Snort has been installed and is storing alert data in the database. Proceed to install BASE (Basic Analysis and Security Engine, which builds upon ACID).
BASE will allow the alert information stored in the MySQL database to be visualized on a web interface. The version used here is base-1.4.5.tar.gz. Since it involves web services, ensure the LAMP stack is installed before proceeding with BASE. The steps are as follows:
Step 1. Install httpd, mysql-server, mysql-devel, php, and php-mysql.
The command is as follows:
yum install -y httpd mysql-server php php-mysql mysql-devel php-gd
[Translation continues in this format…]
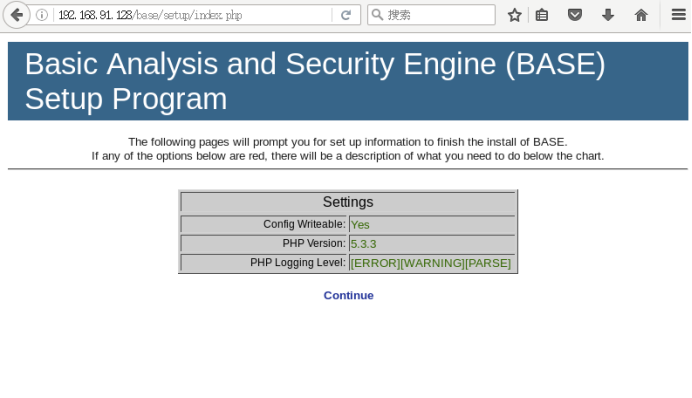
Click the “Continue” button to start selecting the language and ADOdb path, as shown in the image above.
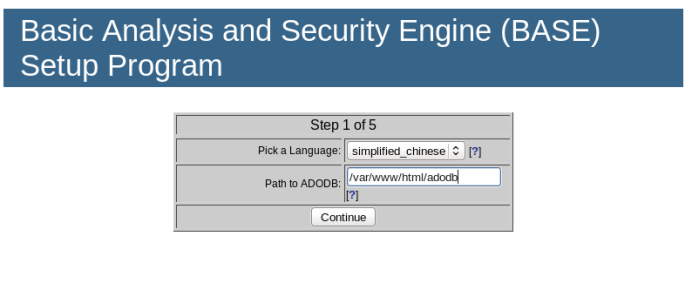
Choose “Chinese” as the language, input `/var/www/html/adodb` in the ADOdb path field, and then click the “Continue” button.
Next, enter the database name, access username, and password, as shown below.
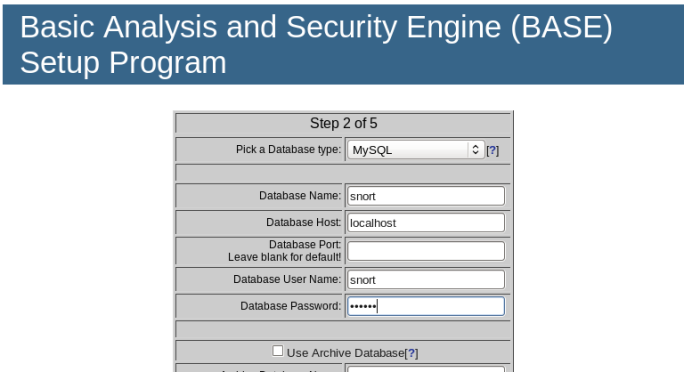
There’s no need to configure an archive database, so the last five fields can remain empty.
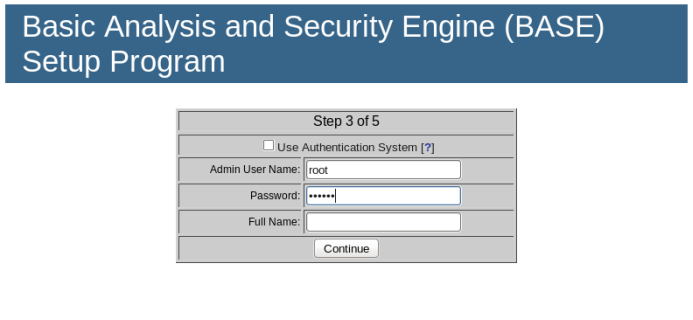
In the following step, set the administrator’s name to `root` and the password to “123456.” The “Full Name” field can be left blank, as shown below.
Proceed to create the BASE table structure.
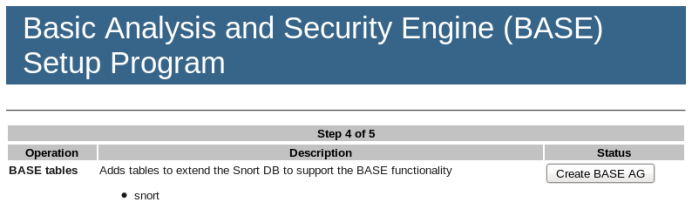
In the figure above, “BASE AG” refers to “Alert Group (AG).”
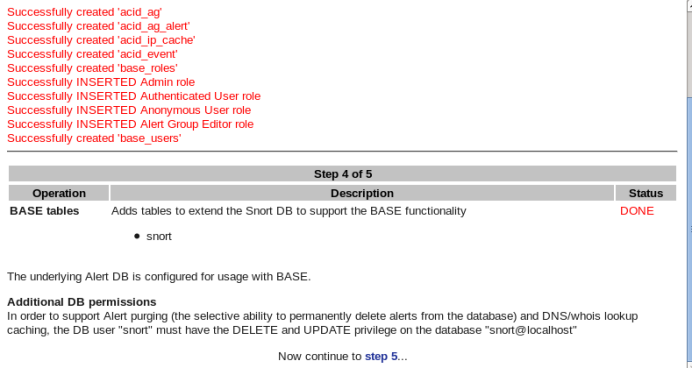
If you see a confirmation message that the “acid” table has been successfully created and the “BASE tables” status shows “DONE,” the installation is complete. Click the “step5…” button at the bottom of the screen to conclude the installation.
[Result Analysis]
Demonstrating Snort’s Working Process
1. Kali: Detecting Ping Attacks Using Snort
1.1 Setting Rules in the `rules/icmp-info.rules` File
cd /etc/snort/rules/
Add the following rule to the `rules/icmp-info.rules` file.
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:”ICMP Large ICMP Packet”; dsize:> 800; reference:arachnids,246; classtype:bad-unknown; sid:499; rev:4;)
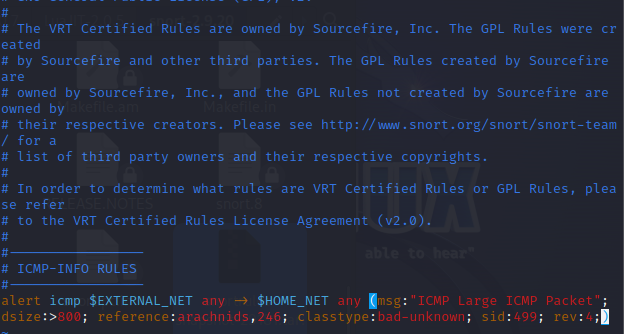
1.2 Using Snort Rules to Monitor Traffic and Output Logs
snort -i eth0 -c /etc/snort/snort.conf -A fast -l /var/log/snort/
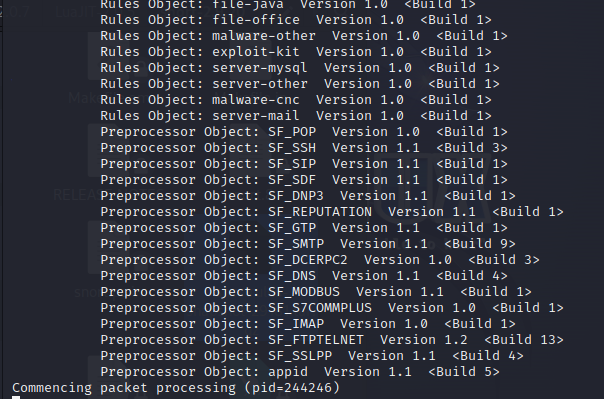
Successfully started Snort for monitoring.
1.3 Launching a Ping Attack (>800 bytes) Against the Snort Host
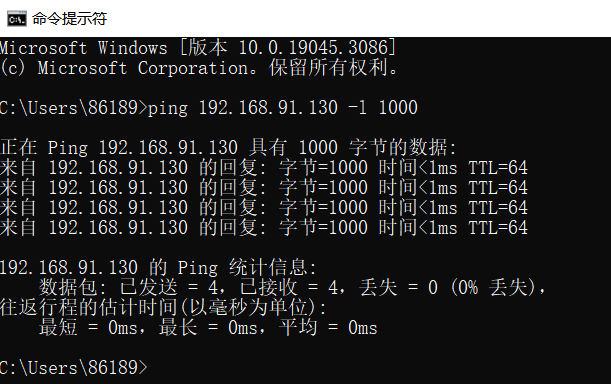
1.4 Viewing the Detection Results in Logs

Successfully detected the ping attack with packet sizes exceeding 800 bytes.
2. Kali: Detecting Nmap Scans Using Snort
2.1 Setting Up TCP Rules in `/etc/snort/rules/local.rules`
vim /etc/snort/rules/local.rules
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:”nmap scan”;sid:1000000888;)
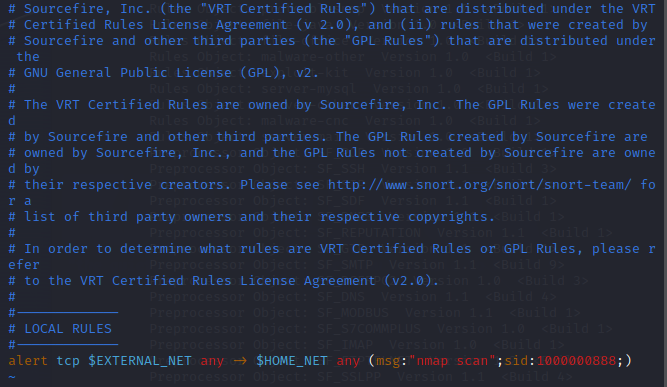
2.2 Starting Snort to Detect LAN Scanning
sudo snort -i eth0 -c /etc/snort/snort.conf -A fast -l /var/log/snort/
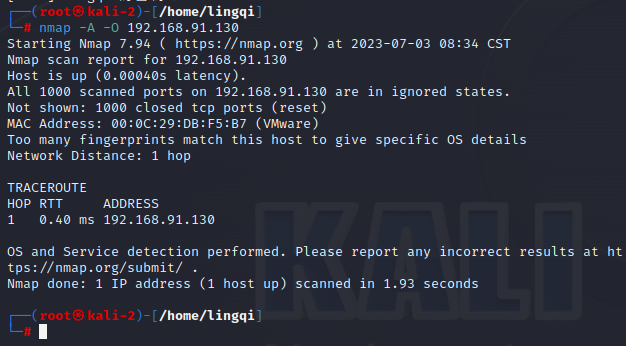
2.3 Conducting an Nmap Scan Using Another Kali Machine in the LAN
2.4 Viewing the Detection Results in `/var/log/snort/alert`
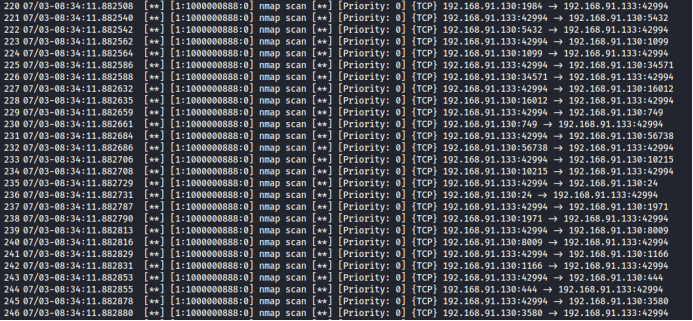
Successfully detected the Nmap scan.
3. CentOS: Monitoring ICMP Packets with Snort and Displaying Results on a Webpage
Run the following command:
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort/ -f snort.log –w /var/log/snort/barnyard2.waldo
On a client terminal, use the `ping` command to send ICMP packets to host `192.168.91.128`. You will see ICMP alerts appear in the BASE interface.
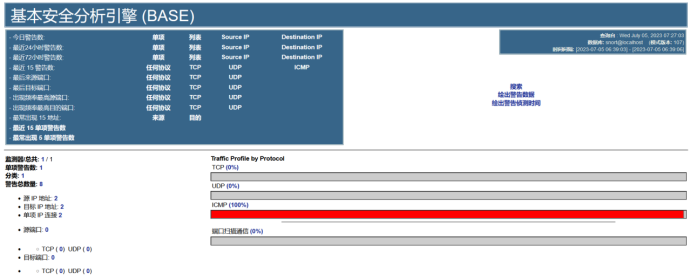
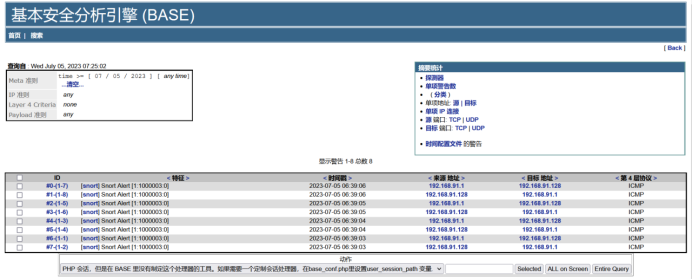
The ICMP packets can be viewed in the list.
[Personal Insights & Reflections]
During this experiment, I used the Kali Linux operating system. From installation to successfully configuring Snort, I encountered several issues but resolved them via online research, eventually testing Snort successfully. Overall, the process was smooth. However, when attempting to install the MySQL database, I discovered that Kali only supports MariaDB, which caused issues during table creation and configuration file downloads. Ultimately, I abandoned the use of Kali for setting up the MySQL database.
I switched to CentOS 6.8 for the experiment. Building on the experience of installing Snort on Kali, I was able to successfully configure Snort, Barnyard2, and BASE. I documented every problem encountered along with the solutions, which greatly enriched my understanding of building an intrusion detection system using Snort.


