Essentially, based on the scope of firewall management, firewalls can be classified as domain-based and single-host based controls. In terms of single-host control, the main types of firewalls include the packet filtering Netfilter and the service application-based analysis TCP Wrappers (pertaining only to service names). As for domain-based firewalls, because these firewalls act as routers, they mainly utilize packet filtering through Netfilter and access proxies via proxy servers.
When making packet filtering decisions, the firewall adheres to a set of rules stored in dedicated packet filtering tables, integrated within the Linux kernel. In these packet filtering tables, rules are grouped into what we call chains. The netfilter/iptables IP packet filtering system is a powerful tool for adding, editing, and removing rules.
Although the netfilter/iptables IP packet filtering system is referred to as a single entity, it consists of two components: netfilter and iptables.
1. The netfilter component, also known as kernel space, is part of the kernel, composed of several packet filtering tables that contain the rules controlling packet filtering processing.
2. The iptables component is a tool, also referred to as user space, that facilitates the insertion, modification, and removal of rules from the packet filtering tables. Unless you are using Red Hat Linux 7.1 or later, you will need to download this tool and install it for use.
The greatest advantage of netfilter/iptables is its ability to configure stateful firewalls, which can specify and remember the state of connections established for packet sending or receiving.
In deciding on new packet filtering, these stateful features utilized by the firewall can enhance its efficiency and speed. There are four effective states: ESTABLISHED, INVALID, NEW, and RELATED.
The state ESTABLISHED indicates that the packet belongs to an already established connection that is used for sending and receiving packets and is entirely legitimate. The INVALID state signifies that the packet is not associated with any known flow or connection; it may contain erroneous data or headers. The state NEW implies that the packet is initiating or will initiate a new connection, or it is associated with a connection not yet used for sending and receiving packets. Lastly, RELATED means that the packet is initiating a new connection and is associated with an already established connection.
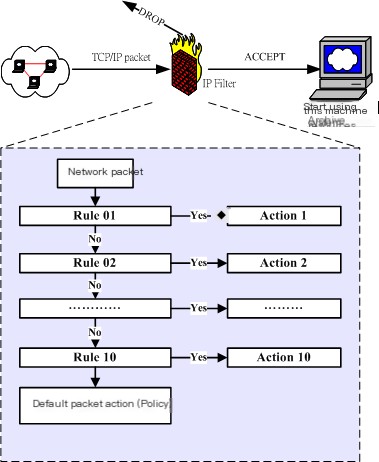
As shown in the diagram: The firewall’s rules specify the characteristics of the packets to be checked, and the target. If a packet does not match, it will be sent to the next rule in the chain for checking; if it matches, the next rule is determined by the target value. The target value can be a user-defined chain name, or a specific value such as ACCEPT, DROP, QUEUE, or RETURN.
However, it is important to note: firewall rules allow access if they pass, so the order of host policy customization is required (example 3)
Detailed introduction and configuration example of iptables:
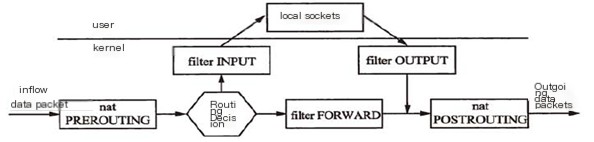
Currently, iptables has three tables and five chains: namely, the filter, nat, and mangle tables; INPUT, OUTPUT, FORWARD, PREROUTING, POSTROUTING.
filter: General filtering function, default is this table.
nat: Used for nat functions (port mapping, address mapping, and packet forwarding).
mangle: Used for modifying specific packets.
PREROUTING: Before a packet enters the routing table (DNAT), the destination is changed before routing.
INPUT: Destination is the host after passing the routing table.
FORWARDING: Destination is not the host after passing the routing table.
OUTPUT: Generated by the host, forwarded outside.
POSTROUTING: Before sending to network interface (SNAT).
Detailed commands for iptables setup:
Management control options of iptables command (commonly used):-A Append a new rule at the end of the specified chain.-D Delete a specific rule in the specified chain, can be deleted by rule number or content.-I Insert a new rule in the specified chain, default added to the first line.-L List all rules in the specified chain for review.-F Flush, clear all rules.-n Display output in numeric form.Note: For more usage details, refer to iptables -hFour ways the firewall handles packets:ACCEPT Allow packets to pass.DROP Discard packets directly without any return message.REJECT Reject packets from passing, provide response message when necessary.LOG Log information in the /var/log/messages file, then pass to the next rule.Saving and restoring iptables firewall rules#iptables-save Save the rules to a file, automatically loaded by the script under the rc.d directory (/etc/rc.d/init.d/iptables).You can also use #service iptables save (directly save to configuration file for automatic boot startup).Use iptables-save command to save rules. Generally use iptables-save > /etc/sysconfig/iptables
Note: It is common to clear current policies when redefining iptables strategies.
#iptables -F
After completing policy configuration, we must save and load from the configuration file for automatic loading on boot.
#/etc/init.d/iptables save
Now let’s demonstrate with some examples:
1. Reject all ICMP protocol packets entering the firewall (default table is filter if not specified with -t).#iptables -A INPUT -p icmp -j REJECT2. Allow the firewall to forward all packets except ICMP protocol ones.#iptables -A FORWARD -p ! icmp -j ACCEPTNote: Use “!” to invert the condition.3. Reject forwarding packets from host 192.168.0.10, allow forwarding from network segment 192.168.0.0/24.#iptables -A FORWARD -s 192.168.0.11 -j REJECT#iptables -A FORWARD -s 192.168.0.0/24 -j ACCEPTNote: When actually adding rules, REJECT must precede because if ACCEPT is first, subsequent rules won’t be checked.4. Drop packets entering the firewall from the external interface (eth1) with private address source.#iptables -A INPUT -i eth1 -s 192.168.0.0/16 -j DROP#iptables -A INPUT -i eth1 -s 172.16.0.0/12 -j DROP#iptables -A INPUT -i eth1 -s 10.0.0.0/8 -j DROP5. Block network segment (192.168.0.0/24), unblocking after two hours.# iptables -A INPUT -s 192.168.0.0/24 -j DROP Rejects all ingress from 192.168.0.0# iptables -A FORWARD -s 192.168.0.0/24 -j DROP Prohibit forwarding from 192.168.0.0’s remit.# at now +2 hoursat> iptables -D INPUT 1at> iptables -D FORWARD 1Note: Be careful when maintaining servers in a machine room, or else performing remote maintenance may result in immediate disconnection after executing the first command, leading you to maintain the server in the room instead ^*^6. Restrict using SSH to log in remotely to the firewall host.#iptables -A INPUT -p tcp –dport 22 -s 192.168.0.2 -j ACCEPT Host 192.168.0.2 allowed access to 22#iptables -A INPUT -p tcp –dport 22 -j DROP Other SSH (22) connections cut off.Note: This rule is mainly used to set the protection scheme of a specific host so that remote SSH access is blocked.7. Allow the application services provided from TCP port 20-1024 of the host.#iptables -A INPUT -p tcp –dport 20:1024 -j ACCEPT#iptables -A OUTPUT -p tcp –sport 20:1024 -j ACCEPT8. Allow forwarding DNS resolution request packets from the 192.168.0.0/24 LAN segment. (Note DNS supports both UDP and TCP)#iptables -A FORWARD -s 192.168.0.0/24 -p udp –dport 53 -j ACCEPT#iptables -A FORWARD -d 192.168.0.0/24 -p udp –sport 53 -j ACCEPT9. Prohibit forwarding packets from MAC address 00:0C:29:27:55:3F and host.#iptables -A FORWARD -m mac –mac-source 00:0c:29:27:55:3F -j DROPNote: Use “-m module keyword” form to invoke display match in iptables. Here we use “-m mac –mac-source” to represent the source MAC address of packets.10. Allow the firewall host to open TCP ports 20, 21, 25, 110, and passive mode FTP ports 1250-1280.#iptables -A INPUT -p tcp -m multiport –dport 20,21,25,110,1250:1280 -j ACCEPTNote: Here, “-m multiport –dport” is used to specify multiple destination ports.11. Prohibit forwarding of TCP packets with source IP addresses from 192.168.1.20-192.168.1.99.iptables -A FORWARD -p tcp -m iprange –src-range 192.168.1.20-192.168.1.99 -j DROPNote: Use “-m –iprange –src-range” to specify IP range here. It is often needed as a NAT server.12. Reject new packets accessing the firewall, but allow response or related packets of established connections.#iptables -A INPUT -p tcp -m state –state NEW -j DROP#iptables -A INPUT -p tcp -m state –state ESTABLISHED,RELATED -j ACCEPTNote: “ESTABLISHED” refers to packets that have established a connection or have responded to requests. “RELATED” refers to those associated with an established connection, such as FTP data connections.13. Only allow the host’s web service (80), FTP (20, 21, 20450-20480), and allow reply packets from external hosts while dropping all other inbound packets.#iptables -I INPUT -p tcp -m multiport –dport 20,21,80 -j ACCEPT#iptables -I INPUT -p tcp –dport 20450:20480 -j ACCEPT#iptables -I INPUT -p tcp -m state –state ESTABLISHED -j ACCEPT#iptables -P INPUT DROP
Clients from the 192.168.0.0 network segment coming through eth0 link SSH will be rejected.# iptables -A INPUT -i eth0 -p tcp -s 192.168.0.0/24 –sport 1024:65535 –dport ssh -j DROP
Note: The significance of the port specified by –sport is about the TCP/IP connection mechanism (the client gives a 1024+ port, the server returns a 1024- port).
Note: The simple configuration of iptables in this article is mostly annotated based on my understanding of application, so if there is any inadequate explanation, I hope you can promptly point it out. Meanwhile, many parameters have not been specified in detail; visitors in need can look them up themselves.


