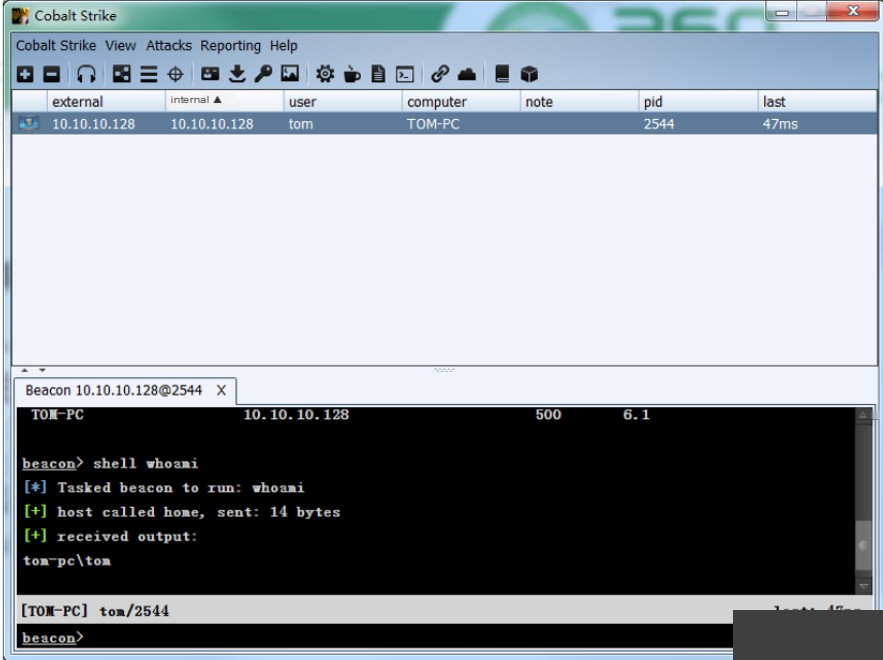
Cobalt Strike
Cobalt Strike is a penetration testing software that includes a client and a server, allowing for distributed team operations. It also supports **payload generation**, enabling security professionals to create and deploy custom payloads for testing network defenses.
- Server: 1
- Client: n
Cobalt Strike integrates various features and modules:
- Port forwarding
- Multi-mode port scanning Listener
- Windows executable generation
- Windows DLL dynamic link library generation
- Java program generation
- Office macro code generation
Configuration Process
Operating System Type: Kali 2021
Directory Structure
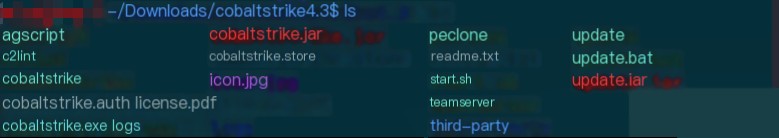
- teamserver: Shell script for running the team server
- cobaltstrike.jar: JAR package for running the client
- cobaltstrike: Shell script for running the client, e.g., java -XX:+UseParallelGC -XX:+AggressiveHeap -XX:ParallelGCThreads=4 -jar cobaltstrike.jar $
- start.sh: Shell script for running the client, similar to cobaltstrike
- cobaltstrike.exe: Windows client program
- cobaltstrike.store: SSL keystore, which can be modified using keytool (Java certificate management tool)
- agscript: Command-line tool for connecting to the team server and running CNA plugins
- c2lint: Tool for checking errors in the profile configuration file
- update.jar: CS upgrade JAR package
- update.bat: CS upgrade batch script
- log: Log directory that records target connections and operations
- third-party: Third-party tools
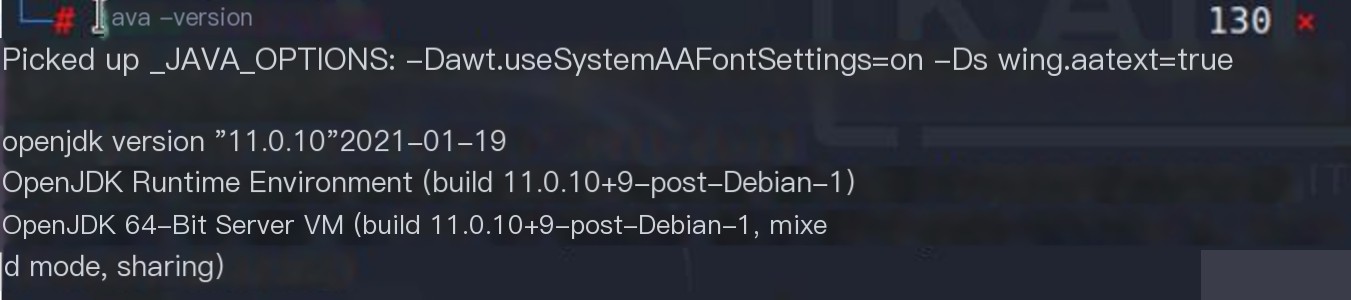
Checking JDK Version
Server Configuration
Enter the Cobalt Strike directory and start the server.
Copy
./teamserver [profile] [YYYY-MM-DD]
# ip: Server IP
# passwd: Password for client-server connection
# profile: User configuration file
# YYYY-MM-DD: Expiration date for all payloads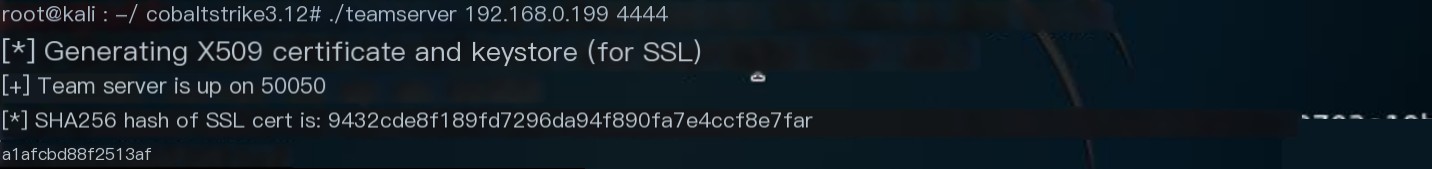
Typically, the nohup command is used to run the teamserver in the background. Note that nohup by default outputs runtime information to the nohup.out file. To suppress output, redirect standard output/error (if nohup is missing, install the coreutils package):
Copy
apt-get install coreutils
nohup ./teamserver [profile] [YYYY-MM-DD] >/dev/null 2>&1 &Client Configuration
- The client only requires a Java environment and has no specific platform requirements.
- Ubuntu:
Copy
java -jar cobalt strike- On Windows, simply double-click to launch.
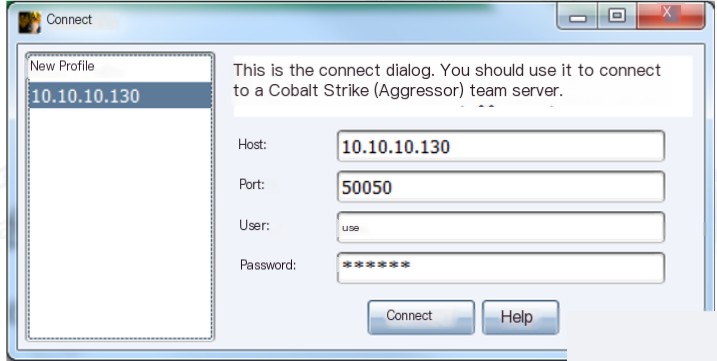
Connecting to the Server
- Host: Server hostname
- Port: 50050
- User: Custom
- Password: Set on the server
Main Client Interface
Usage
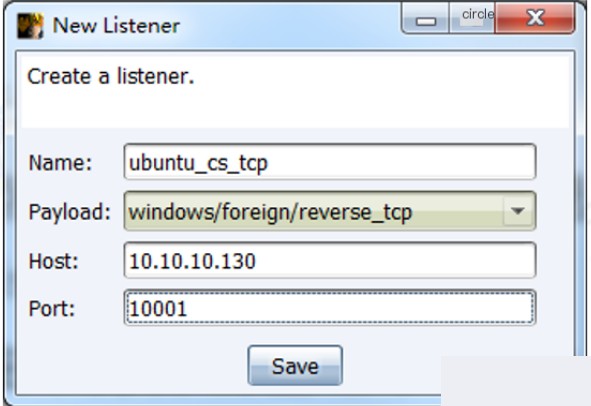
First, configure the listener. Click the “Cobalt Strike” option at the top, select “Listeners” from the dropdown menu, and click the “Add” button in the lower section. In the pop-up dialog, enter the listener name, select the payload type, specify the host as the reverse shell receiver, set the port for the reverse connection, and click “Save.”
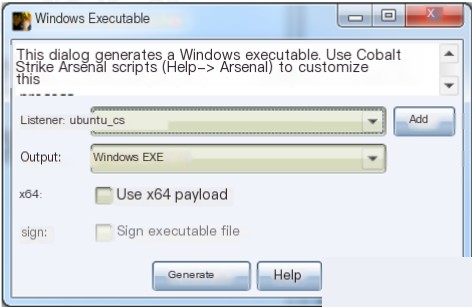
Generating a payload. Click “Attacks” -> “Packages” -> “Windows Executable.” In the pop-up dialog, select the previously added listener, set the output type to match the target machine, and click “Generate.” Then, choose a save location and enter a name for the payload.
Bringing the target online. Deploy and execute the generated payload on the target machine. Once the target is online, change the default heartbeat interval to 0. By default, Cobalt Strike sends a connection request every 60 seconds to maintain the session, but this can cause lag. To modify this, right-click the target, select “Session” -> “Sleep” from the dropdown menu, enter “0” in the pop-up dialog, and click “OK.”