Article Introduction
In an internal network, traffic monitoring mainly focuses on unencrypted service protocols within a subnet. The primary targets include service connection passwords, website login passwords, and sensitive data, and Cain software is commonly used for this purpose.
Traffic Analysis
Cain
Experiment Environment
- Attacking Host: 192.168.174.169
- Target Host: 192.168.174.170
- WEB Host: 192.168.174.1
Experiment Steps
Install Cain on the attacking host, then use Cain to act as a man-in-the-middle to perform ARP spoofing to intercept the communication traffic between the target host and the gateway to obtain unencrypted data information.
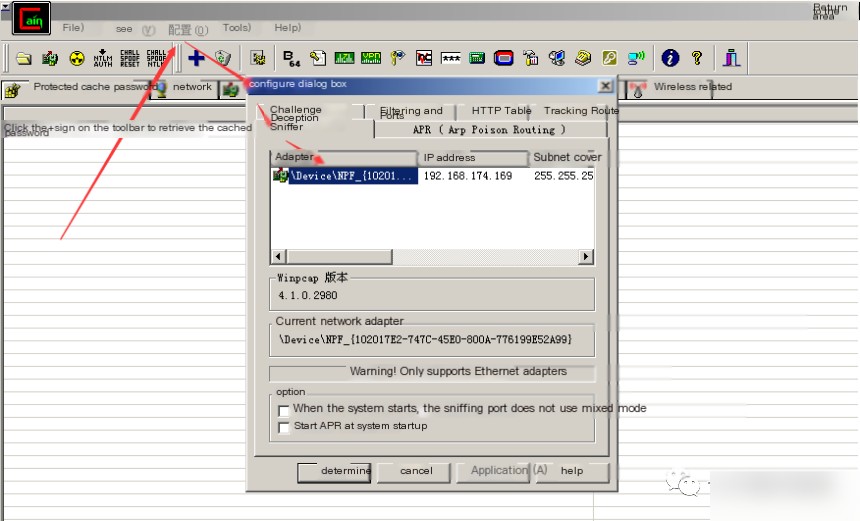
Step 1: Select the network card
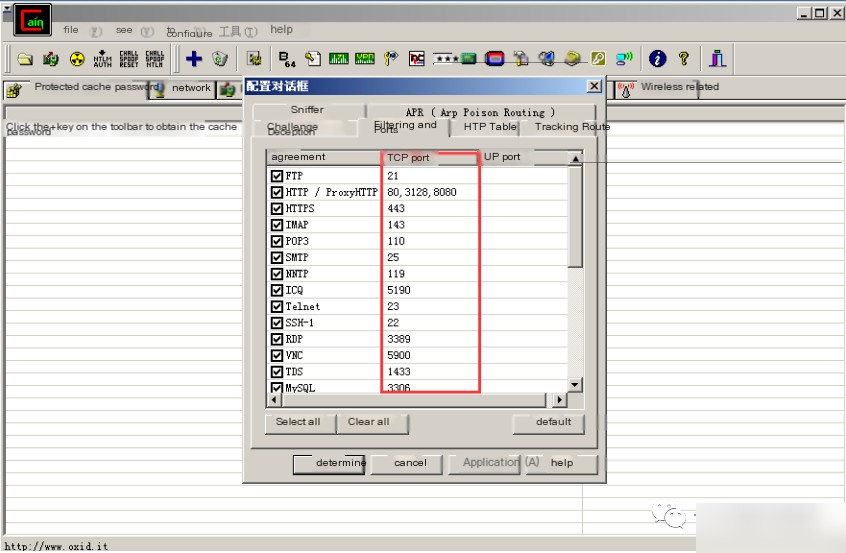
Step 2: Select the filtered port
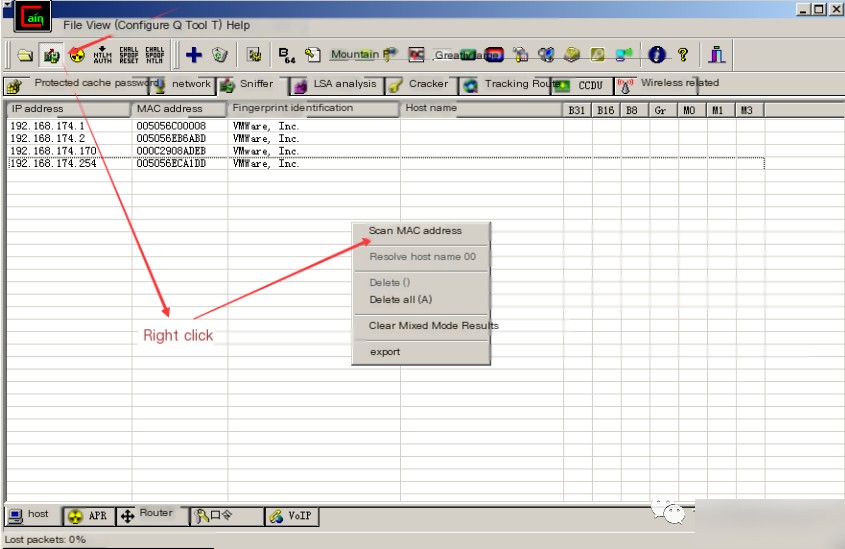
Step 3: Begin scanning the segment for host survival
Step 4: Select the gateway and spoof the target host
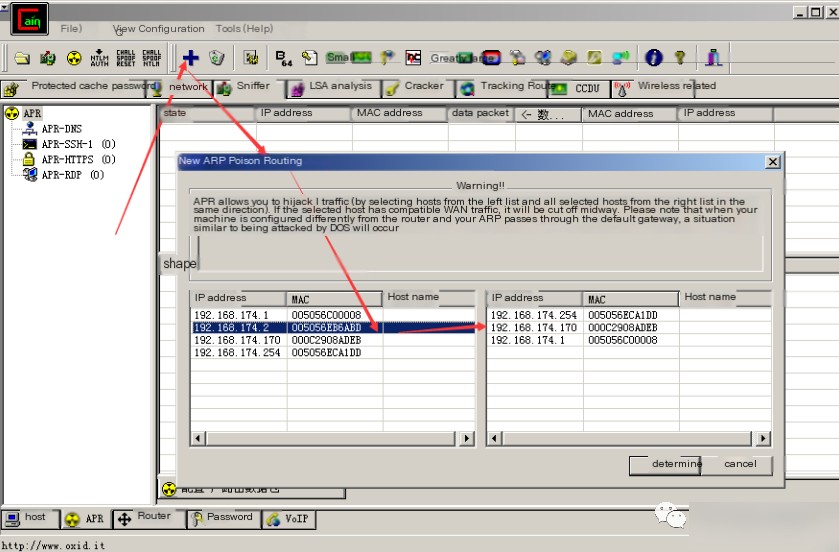
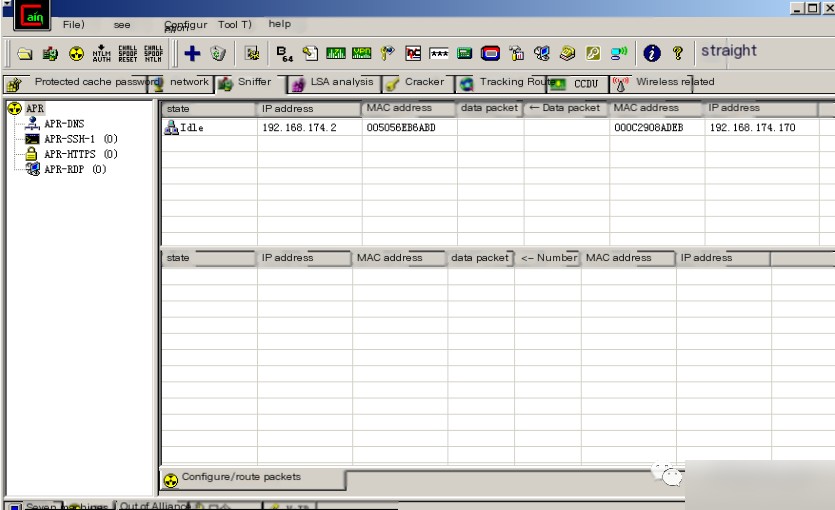
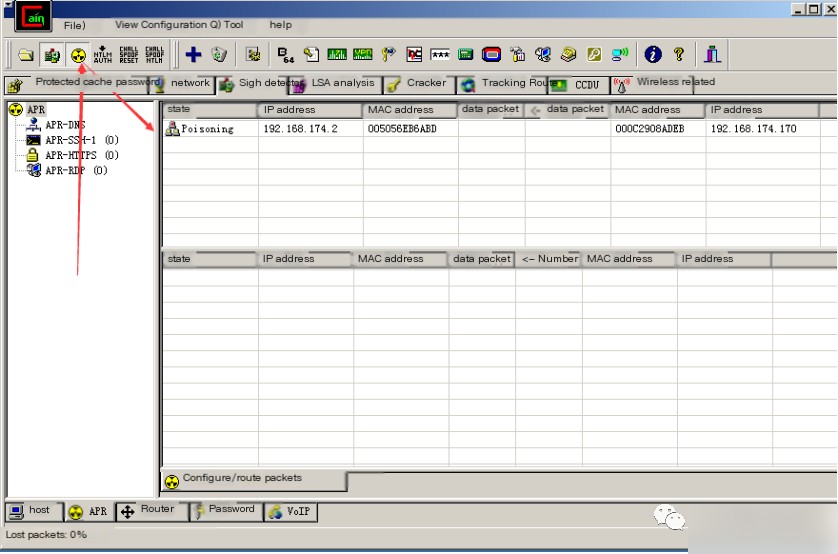
Step 5: Begin spoofing
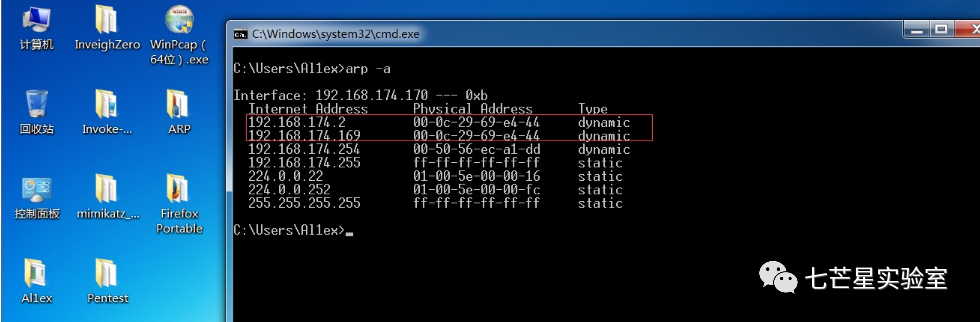
Step 6: Check the ARP list on the target host. You can see that the MAC addresses of the gateway and the attacking host are the same, indicating that ARP spoofing has been completed.
Step 7: Start the Telnet service on the WEB service host
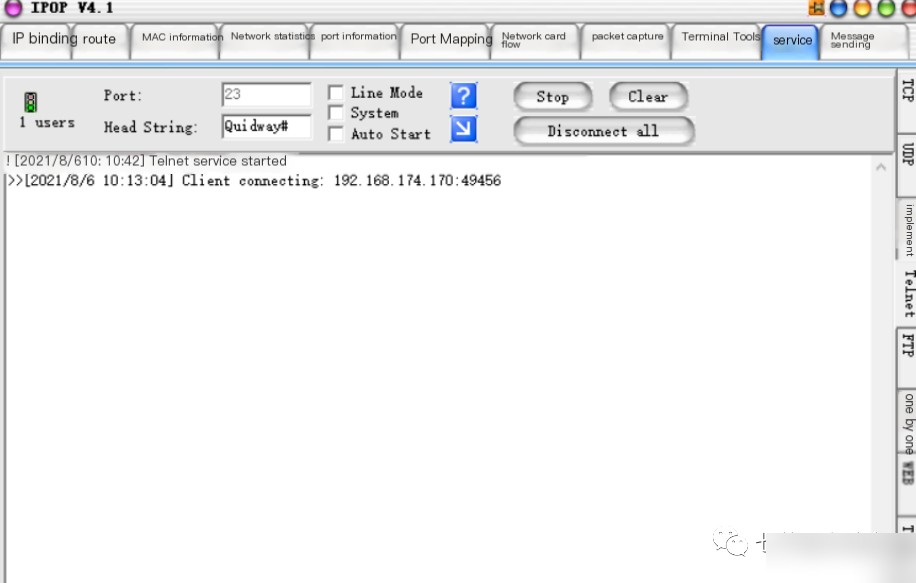
Step 8: Then simulate normal user login
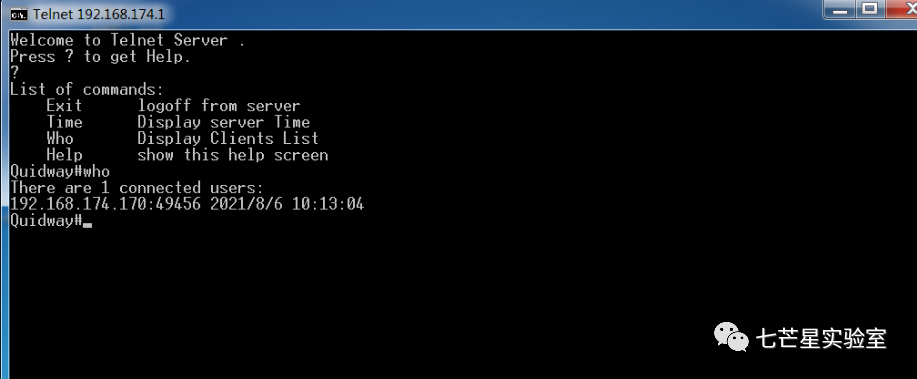
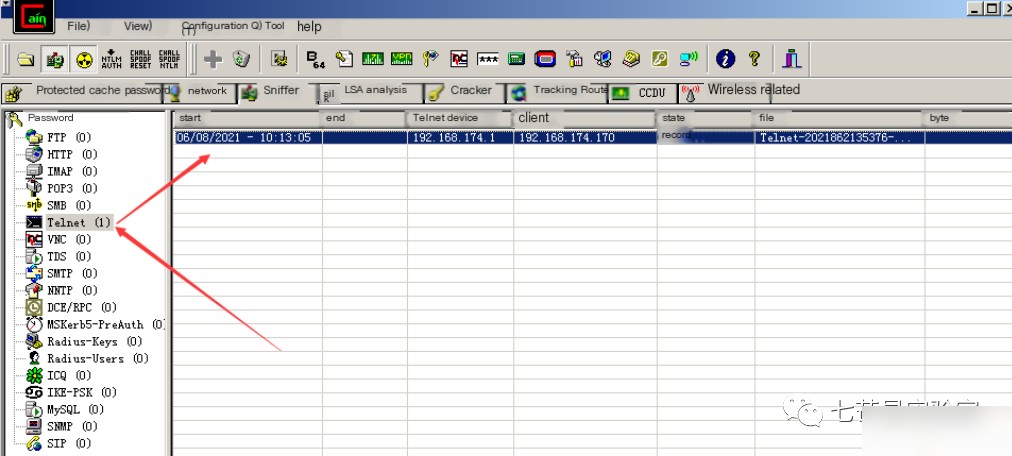
Wireshark
Experiment Environment
- Attacking Host: 192.168.174.169
- Target Host: 192.168.174.170
- WEB Host: 192.168.174.1
Experiment Steps
Wireshark is an essential tool for network engineers, with powerful capabilities. Here, we briefly introduce its filter syntax for traffic monitoring.
1. Filter HTTP traffic
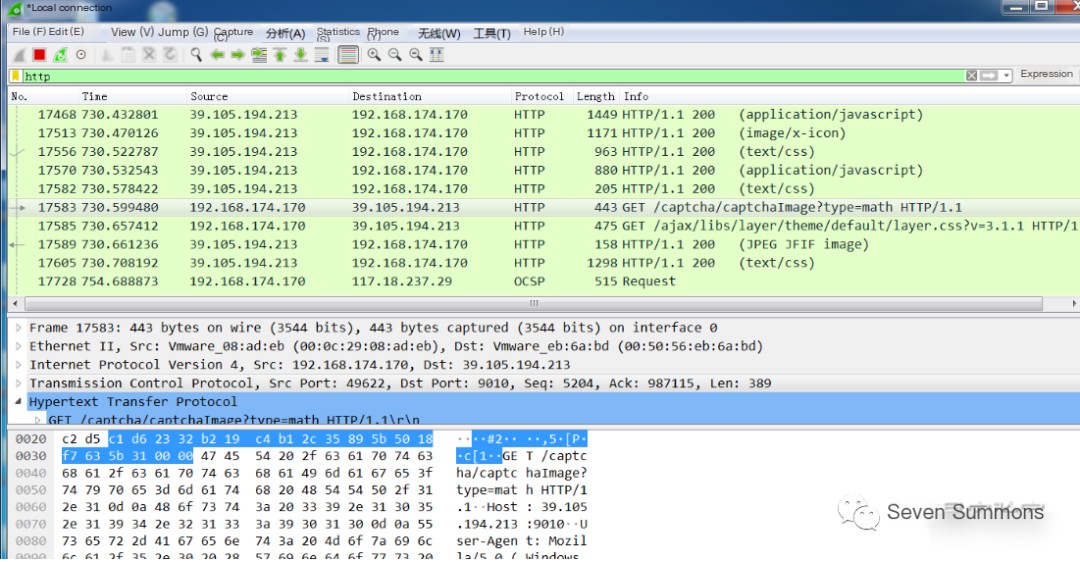
2. Filter HTTP traffic from a specified source address
http && ip.src==192.168.174.170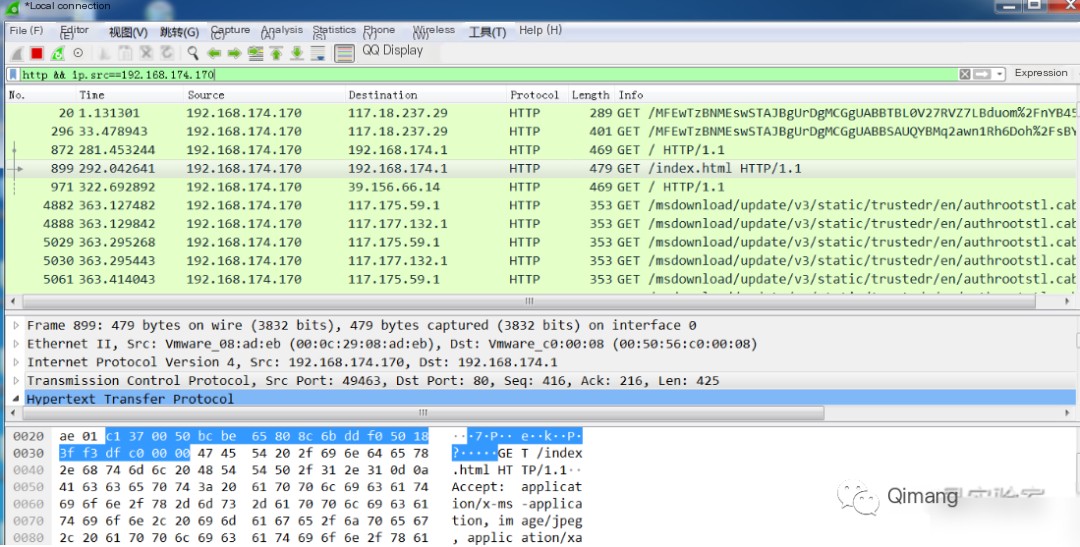
3. Filter POST data containing a username and password
http && ip.src==192.168.174.170 && http.request.method=="POST"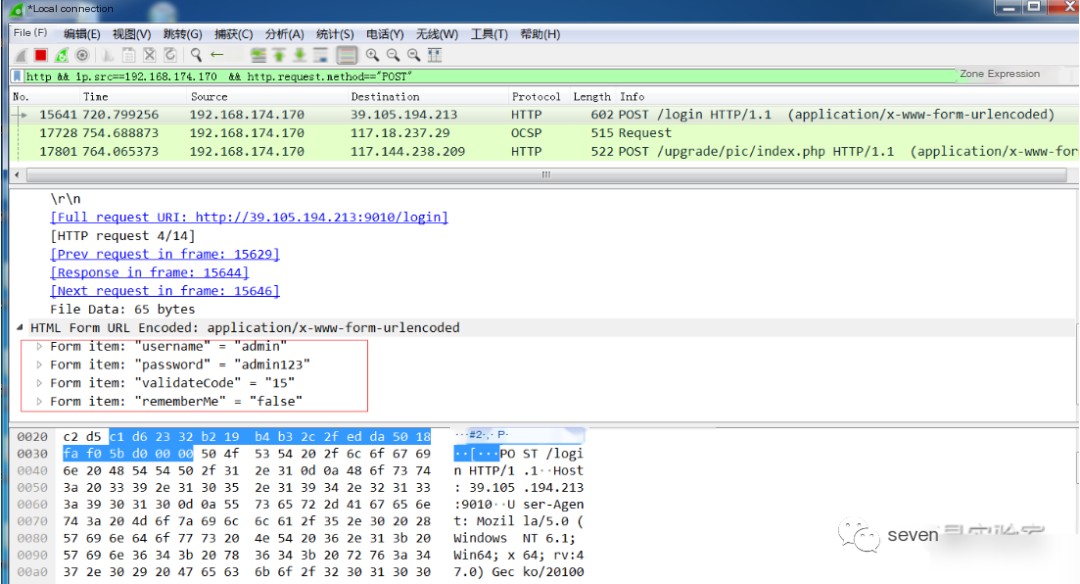
4. Filter HTTP traffic accessing a specified destination address
http && ip.dst==39.105.194.213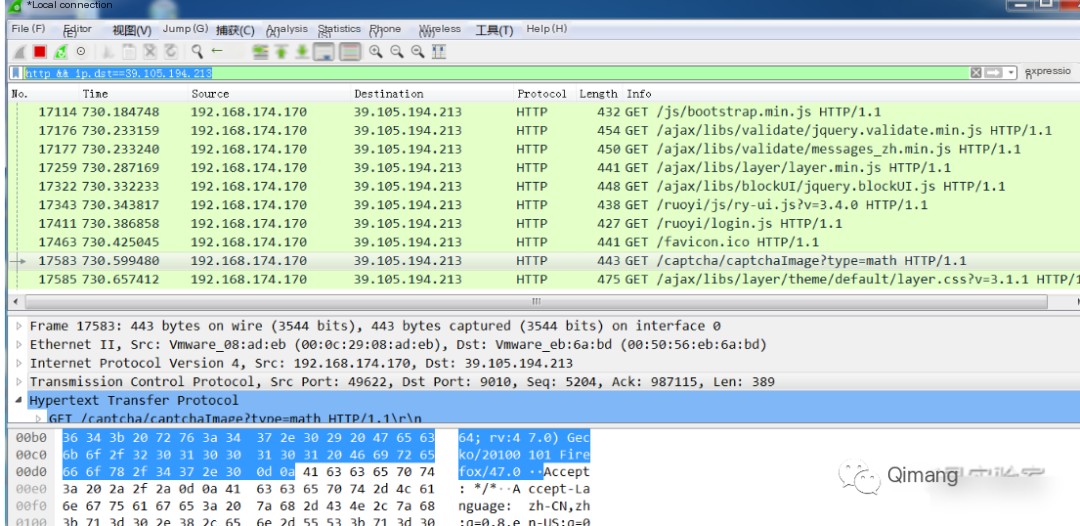
5. Filter FTP traffic
ftp && ip.dst==192.168.198.133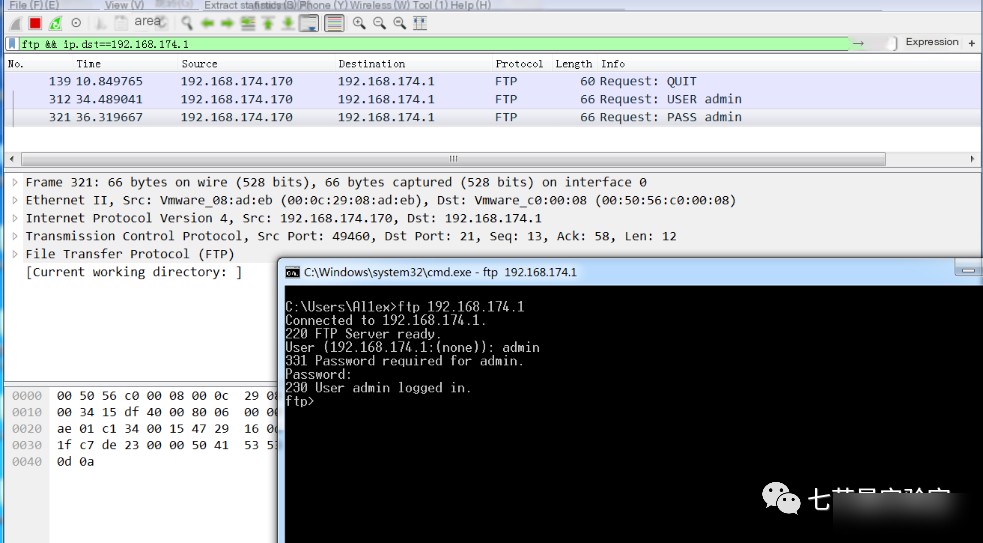
6. Filter Telnet traffic
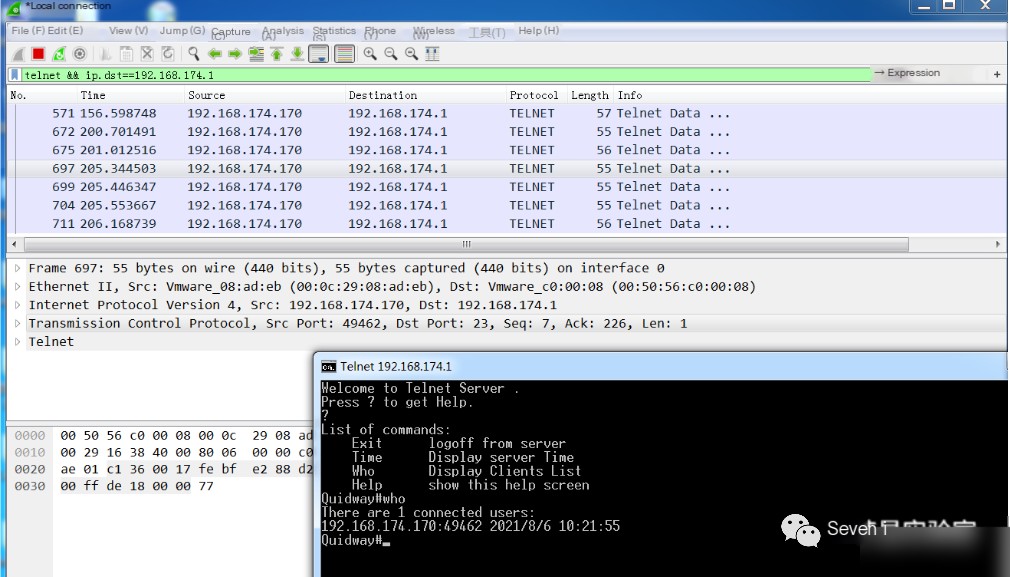
telnet && ip.dst==192.168.198.133