In Windows privilege escalation during penetration testing, after gaining shell access, many users typically create a new user, elevate it to an administrator, and enable Remote Desktop Connection. However, Remote Desktop Connection does not allow connections with empty passwords by default. Additionally, most cloud servers have password policies enabled by default, which prevents us from setting a password for the newly created user.
Using a certain cloud server as an example, after gaining shell access, I created a new user in the virtual terminal of the web shell tool.

Prompt: The password does not meet the password policy requirements. Check the minimum password length, password complexity, and password history requirements.
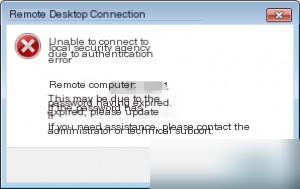
If the account has an empty password, Remote Desktop Connection will display the following error:
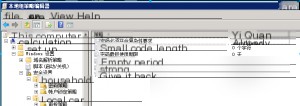
To disable password complexity, the usual method is to modify it in the Local Security Policy settings.
However, during recent penetration tests, I discovered that the secedit command can be used to bypass Windows password policies.
The secedit command is something that many people may not have used before. I stumbled upon its powerful capabilities by chance.
Secedit
This command is part of the Windows NT series and serves as the command-line version of the Group Policy tool. It configures and analyzes system group policy security by comparing it with a group policy template. Group Policy is a critical tool for establishing a secure Windows environment, especially in Windows domain environments. A proficient system administrator should be well-versed in using and applying Group Policy. The graphical interface for accessing Group Policy is gpedit.msc, while the command-line tool is secedit.exe.
Parameters
/configure: Configures Group Policy/analyze: Analyzes Group Policy/import: Imports Group Policy/export: Exports Group Policy/generaterollback: Generates a rollback and configuration template/validate: Validates the syntax in the configuration file/db <database file name>: Required parameter specifying the database file that contains the analyzed storage data. If the database is new, the/cfgparameter is required./cfg <configuration file name>: Specifies the path and name of the security template. Used only with the/dbparameter. If not specified, the stored data is executed./overwrite: Determines whether to overwrite/log <log file name>: Specifies the name and path of the log file. If not specified, the default is used./quiet: Enables silent mode/areas: Specifies allowed security areas of the system. If not specified, all areas are selected by default. Separate each area with a space./mergedpolicy: Merges and exports domain and local security policies.
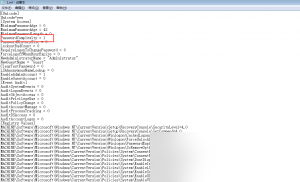
First, export the Group Policy file to the current directory and name it 1.inf for analysis:
Modify PasswordComplexity to 0 and re-import the file to disable password complexity. However, the file contains a lot of content, and we only need to modify this one parameter. Therefore, it is unnecessary to import all the content.
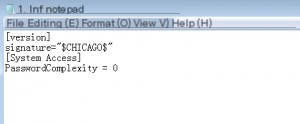
After researching, I found that the content can be reduced to just a few lines, including only the necessary parts:
[version]
signature=”$CHICAGO$” [System Access] PasswordComplexity = 0
In the command line, you can use echo to write this content into a file:
echo [version] > 1.inf && echo signature="$CHICAGO$" >> 1.inf && echo [System Access] >> 1.inf && echo PasswordComplexity = 0 >> 1.inf
Then, import the Group Policy file:
secedit /configure /db temp.sdb /cfg 1.inf
At this point, two files, 1.inf and temp.sdb, will be generated in the current directory. The temp.sdb file is an intermediate file created by the /db parameter. To clean up, combine all commands and delete the generated files:
echo [version] > 1.inf && echo signature="$CHICAGO$" >> 1.inf && echo [System Access] >> 1.inf && echo PasswordComplexity = 0 >> 1.inf && secedit /configure /db temp.sdb /cfg 1.inf && del 1.inf temp.sdb
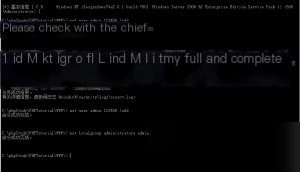
Now, we have successfully created a new user and elevated it to administrator privileges.
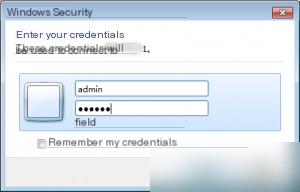
Using the newly created administrator account, we can now successfully connect to the cloud server via Remote Desktop.
Conclusion: The secedit command is incredibly powerful and allows for more efficient privilege escalation during penetration testing.


