About BruteShark
BruteShark is a powerful Network Forensics Analysis Tool (NFAT). With the help of this tool, researchers can easily perform in-depth processing and examination of network traffic (primarily PCAP files, but it can also capture live traffic directly from network interfaces). The main features of this tool include password extraction, network mapping construction, TCP session reconstruction, and extracting encrypted password hashes. The tool’s settings also allow converting extracted encrypted password hashes to Hashcat format for brute force testing.
The main goal of the tool is to provide security solutions for security researchers and network administrators responsible for network traffic analysis, while also identifying potential network security weaknesses.
Currently, BruteShark offers two available versions: a GUI-based application (Windows) and a command-line tool (Windows and Linux).
Besides, many projects and components provided within this solution can be used independently as infrastructure for analyzing network traffic on Linux or Windows.
BruteShark Features Introduction
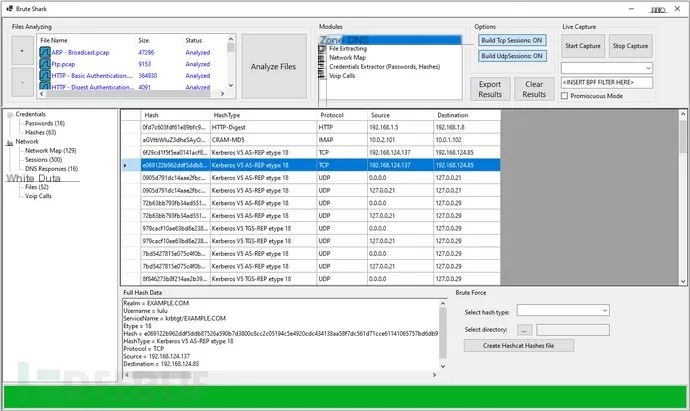
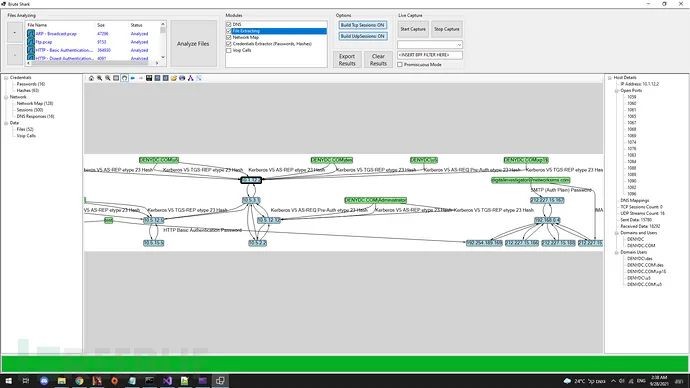
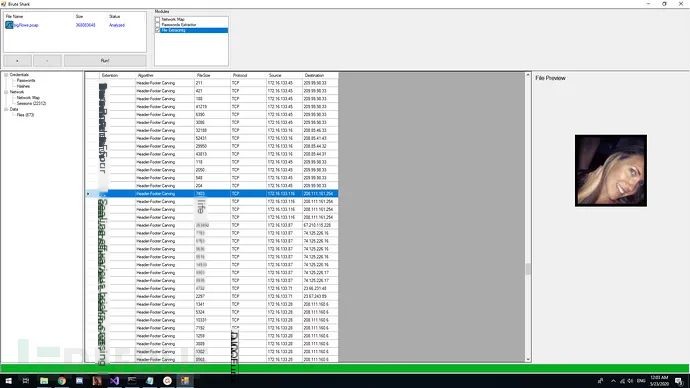
1. Extract and encode usernames and passwords (HTTP, FTP, Telnet, IMAP, SMTP, etc.);2. Extract authentication hashes and use Hashcat for cracking (Kerberos, NTLM, CRAM-MD5, HTTP Digest…);3. Construct visual network topology maps (including network nodes, open ports, domain users, etc.);4. Extract DNS queries;5. Reconstruct all TCP & UDP sessions;6. File splitting;7. Extract VoIP calls (SIP, RTP);
BruteShark Tool Download
BruteShark: Windows
First, we need to download and install the following dependencies:
1. Npcap driver (installed by default after installing the latest version of Wireshark);2. .NET Core Runtime
Desktop version: BruteSharkDesktop Windows Installation Package (64 Bit)
Command-line tool version: BruteSharkCli Windows 10 Executable
Linux: BruteShark
First, we need to download and install the following dependencies:
1. libpcap driver
Next, use the following command to download BruteSharkCli:
Code language: javascriptCopy
wget https://github.com/odedshimon/BruteShark/releases/latest/download/BruteSharkCli./BruteSharkCliBruteShark Tool Usage
Using the BruteSharkDesktop desktop client is quite simple, just operate according to the illustrated interface. We mainly introduce the usage of the BruteSharkCli command-line tool.
Print help menu:
Code language: javascriptCopy
BruteSharkCli --helpObtain credential data from all files in the directory. Passwords and hashes will be printed to stdout:
Code language: javascriptCopy
BruteSharkCli -m Credentials -d "C:\Users\King\Desktop\Pcap Files"Obtain credential data from all files in the directory, and export extracted hashes to a Hashcat input file:
Code language: javascriptCopy
BruteSharkCli -m Credentials,NetworkMap,FileExtracting -d C:\Users\King\Desktop\Pcap_Examples -o C:\Users\King\Desktop\ResultsRun multiple feature modules on all files in the directory and export all results:
Code language: javascriptCopy
BruteSharkCli -m Credentials,NetworkMap,FileExtracting -d C:\Users\King\Desktop\Pcap_Examples -o C:\Users\King\Desktop\ResultsSniff an interface named “Wi-Fi”, run multiple modules, and then export all results to a directory (results are only exported after pressing CTRL+C to stop sniffing):
Code language: javascriptCopy
BruteSharkCli -l Wi-Fi -m Credentials,NetworkMap,FileExtracting,DNS -o C:\Users\King\Desktop\Test ExportTool Operation Screenshots
Hash Extraction
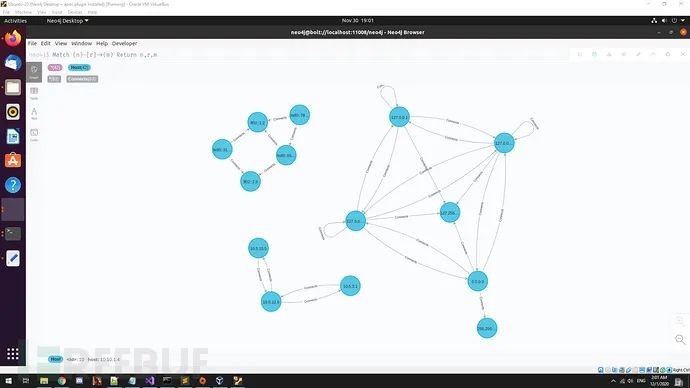
Construct Network Topology Map
File Splitting
Password Extraction
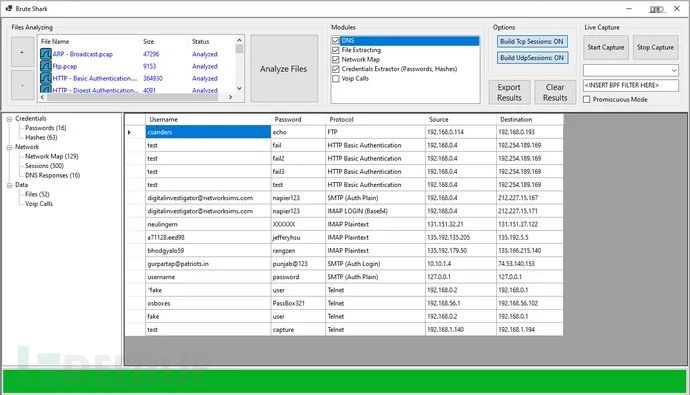
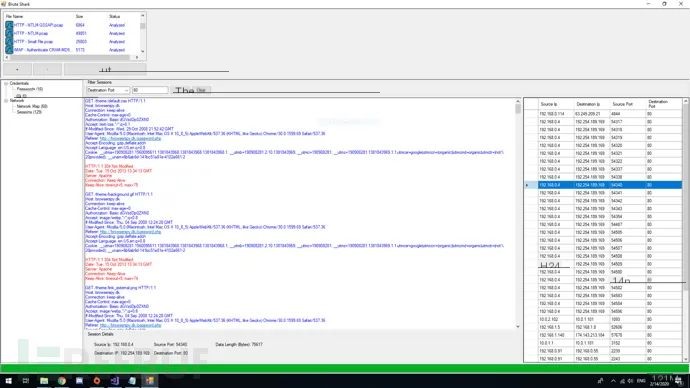
Reconstruct All TCP Sessions
Extract VoIP Calls
Tool Demo Videos
Build a network map:
BruteSharkCli usage example – extracting multiple passwords and hashes:



