1.1What is Cobalt Strike?
Cobalt Strike is a penetration testing software designed to execute targeted attacks and simulate the post-exploitation behavior of advanced threat actors. This section introduces the installation and features of Cobalt Strike, including the Beacon payload. The rest of this manual discusses these features in detail.
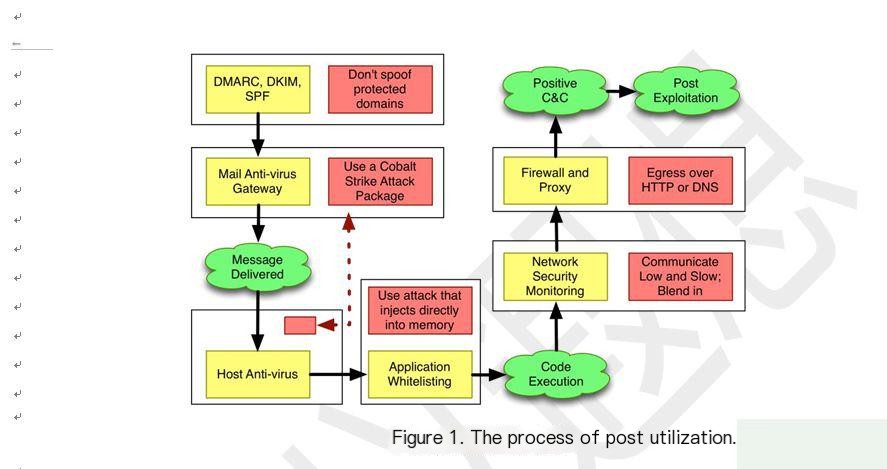
Figure 1. Post-exploitation process with Beacon payload
Begin your attack by gathering intelligence on the target. Cobalt Strike’s system profiler is a web application that analyzes the client-side attack surface of the target. The **Beacon payload** can be used to execute further actions based on the gathered information.
Use Cobalt Strike to weaponize common documents. Set up a malicious Java Applet, embed a malicious macro into a Word document, or create an executable that drops and runs a payload. These user-driven attacks are perfect tools for gaining a foothold in the target network.
Attack using Cobalt Strike’s spear-phishing tool. This tool repurposes saved emails for pixel-perfect phishing. Use it to send weaponized documents or direct targets to cloned sites with embedded exploits.
Control the target network using Cobalt Strike’s Beacon. This payload uses the same asynchronous “low and slow” communication mode as advanced threat malware. Beacon communicates via DNS, HTTP, or HTTPS and can evade detection by common proxy configurations while communicating with multiple hosts to prevent interception.
Use Beacon’s Malleable Command and Control language to practice attack attribution and analysis evasion. Reprogram Beacon to use network indicators that mimic known malware or blend with existing traffic.
Move laterally within the compromised network, discover hosts, and automate Beacon’s peer-to-peer communication via named pipes. Cobalt Strike is optimized to capture trust relationships and facilitate lateral movement using captured credentials, password hashes, access tokens, and Kerberos tickets.
Demonstrate meaningful business risks using Cobalt Strike’s user-developed tools. Cobalt Strike’s unique workflow makes it easy to deploy keyloggers and screenshot capture tools at scale across multiple compromised systems. Use the browser pivoting feature to access websites logged into by the infected target using Internet Explorer. This Cobalt Strike-exclusive technique works on most sites and bypasses two-factor authentication.
Cobalt Strike’s reporting capabilities can reconstruct your client’s engagement. Provide network administrators with an activity timeline so they can identify attack indicators in their sensors. Cobalt Strike generates high-quality reports that you can present as standalone products to your clients or append to your written narrative.
1.2 Installation and Updates
Strategic Cyber LLC provides the Cobalt Strike package, including the Beacon payload, as a native archive for Windows, Linux, and macOS. To install Cobalt Strike, simply extract the archive on your operating system.
System Requirements
Cobalt Strike requires an environment with Oracle Java 1.8, Oracle Java 11, or OpenJDK 11.
If your system has antivirus software, ensure that it is disabled before installing Cobalt Strike.
Trial Version vs. Full Version
The primary Cobalt Strike package is a trial version. The trial version is time-limited, but there are significant differences between the trial and licensed products. The Cobalt Strike trial version does not encrypt tasks and responses in its Beacon payload. Additionally, the trial version generates executables and network traffic that deliberately alert most security products. (Translator’s note: At this point, I believe many people would want to disable it.)
Updating a Licensed Cobalt Strike Product
To fully benefit from Cobalt Strike’s features, you must update to a licensed product using a license key. The trial version includes an updater for this purpose. This program accepts a license key and retrieves the latest version of Cobalt Strike for you. The licensed Cobalt Strike software includes communication security features and removes the limitations present in the trial version.
Figure 2. Update process (very simple, but the key shown in the illustration is no longer valid)
Ensure that you update both the team server and client software using the license key. Cobalt Strike is typically licensed per user. The team server does not require a separate license.
1.3 Team Server
Cobalt Strike consists of client and server components. The server, known as the team server, acts as the controller for the Beacon payload and hosts Cobalt Strike’s social engineering features. The team server also stores collected data and manages logging.
The Cobalt Strike team server must run on a supported Linux system to deploy the Beacon payload. To start it, use the `teamserver` script included in the Cobalt Strike Linux package.
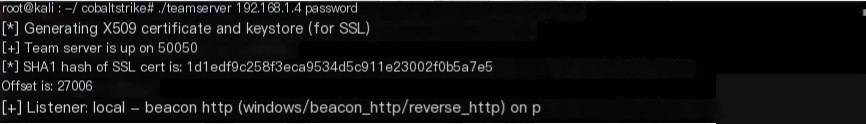
Figure 3. Starting the Team Server
The team server requires two mandatory parameters and has two optional parameters. The first is the externally reachable IP address of the team server. Cobalt Strike uses this value as the default host for its features. The second is the password that your team members will use to connect their Cobalt Strike clients to the team server.
The third parameter is optional. It specifies the Malleable C2 communication profile. This feature is discussed in Chapter 12.
The fourth parameter is also optional. It specifies an expiration date in YYYY-MM-DD format. The team server embeds this expiration date into every generated Beacon stage. The Beacon payload will refuse to run on or after this date. If the Beacon payload wakes up on or after this date, it will also exit.
When the team server starts, it publishes the SHA256 hash of its SSL certificate. Distribute this hash to your team members. When your team members connect, their Cobalt Strike client will ask if they recognize this hash before authenticating with the team server. This is an important protection against man-in-the-middle attacks.
1.4 Cobalt Strike Client
The Cobalt Strike client connects to the team server. To start the Cobalt Strike client, use the launcher included in the platform package.
When the Cobalt Strike client starts, you will see a connection dialog for the Beacon payload.
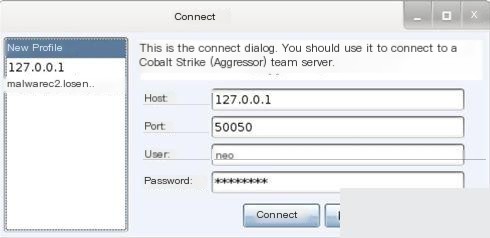
Figure 4. Cobalt Strike Connect Dialog
Specify the team server’s address in the “Host” field for the Beacon payload. The default port is 50050, and it rarely needs to be changed. “User” is your nickname on the team server—update it to your alias or hacker name. “Password” is the shared password for the team server.
Click “Connect” to connect to the Cobalt Strike team server and send the Beacon payload.
1.5 Distributed and Team Operations
Use Cobalt Strike to coordinate distributed red team operations. Deploy Cobalt Strike in stages on one or more remote hosts. Start your team server and have your team connect.
1.6 Cobalt Strike Scripting
Cobalt Strike can be scripted using its Aggressor Script language. Aggressor Script is the spiritual successor to Armitage’s Cortana scripting language, but the two are not compatible. To manage scripts, go to Cobalt Strike -> Script Manager.