Apache HTTPD is an HTTP server that can run PHP web pages through mod_php. Versions 2.4.0 to 2.4.29 contain a parsing vulnerability where 1.php\x0A is parsed as a PHP file extension, allowing bypassing of certain server security policies.
After starting the vulhub environment, accessing the page shows nothing, so let’s directly examine the code.
<?php
if(isset($_FILES['file'])){$name=basename($_POST['name']);$ext=pathinfo($name,PATHINFO_EXTENSION);if(in_array($ext,['php','php3','php4','php5','phtml','pht'])){exit('bad file');}move_uploaded_file($_FILES['file']['tmp_name'],'./'.$name);}
As seen, the code directly processes POST parameters. If the file extension is PHP, the upload is rejected. Uploading a file named 1.php is intercepted.
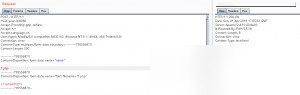 By appending a
By appending a \x0A to 1.php (note: it must be \x0A and not \x0D\x0A), the file is no longer intercepted.
Accessing the uploaded /1.php%0a file reveals that it is successfully parsed.
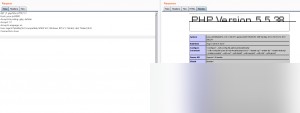
However, this file does not have a PHP extension, indicating the presence of a parsing vulnerability in the target.


