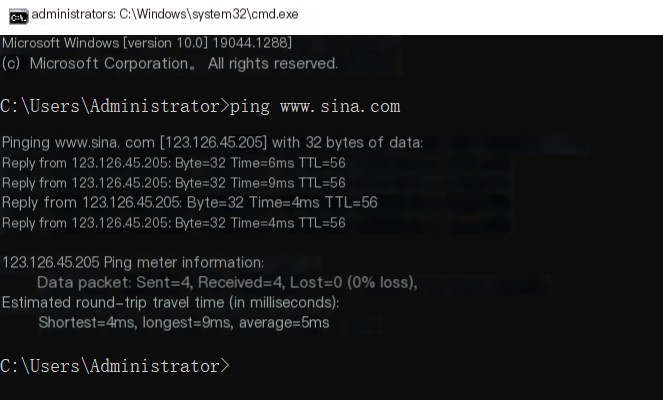
Using Wireshark, a packet capture tool, to capture and analyze UDP protocol packets in detail. DNS is by default based on the UDP protocol. Accessing a domain name involves domain name resolution, which uses the DNS protocol (an application layer protocol) over Port 53.
Now, trigger DNS traffic and capture packets to see the implementation of the UDP protocol:
 />
/>
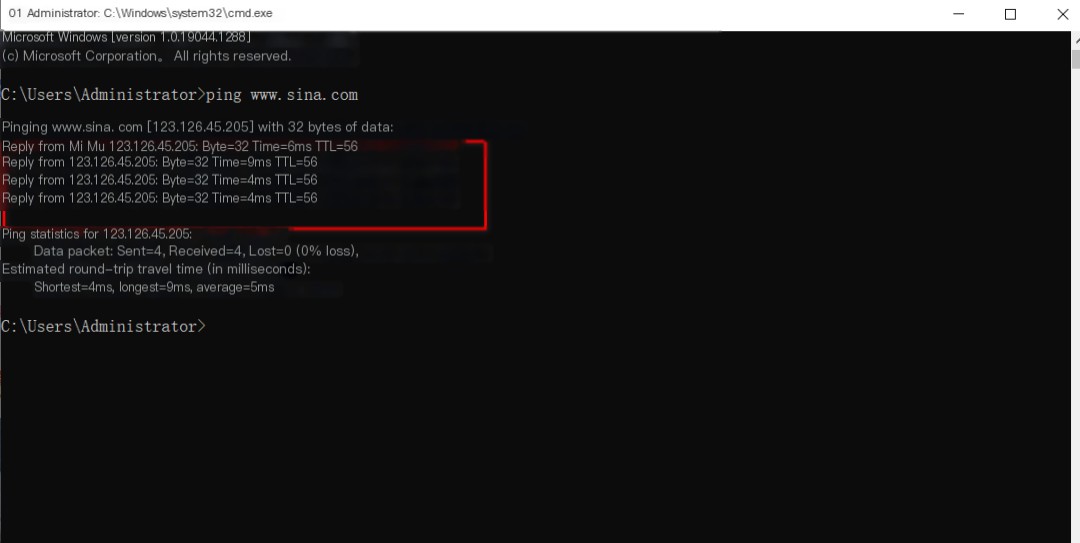
Pinging a domain name translates it into an IP address, during which the DNS protocol is invoked.
Below is the DNS protocol captured in the packet:
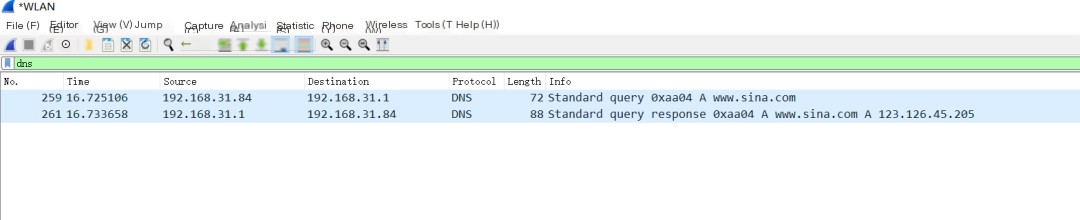
First, a domain name request is sent, then the gateway handles the domain name resolution and responds with the corresponding IP address.
1. Double-click to open the first packet on Port 53:
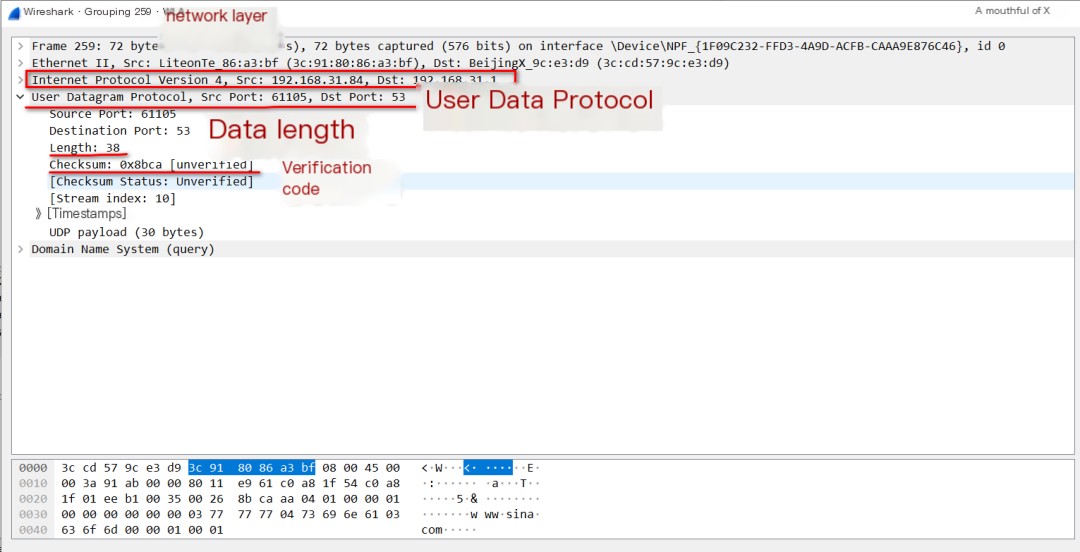
The default port for the DNS protocol is port 53, and the source port is random. In this packet, there are no sequence numbers, acknowledgment numbers, or flags. This is what the UDP protocol looks like.
The DNS Protocol Operates on Top of UDP, Specifically Using Port 53:
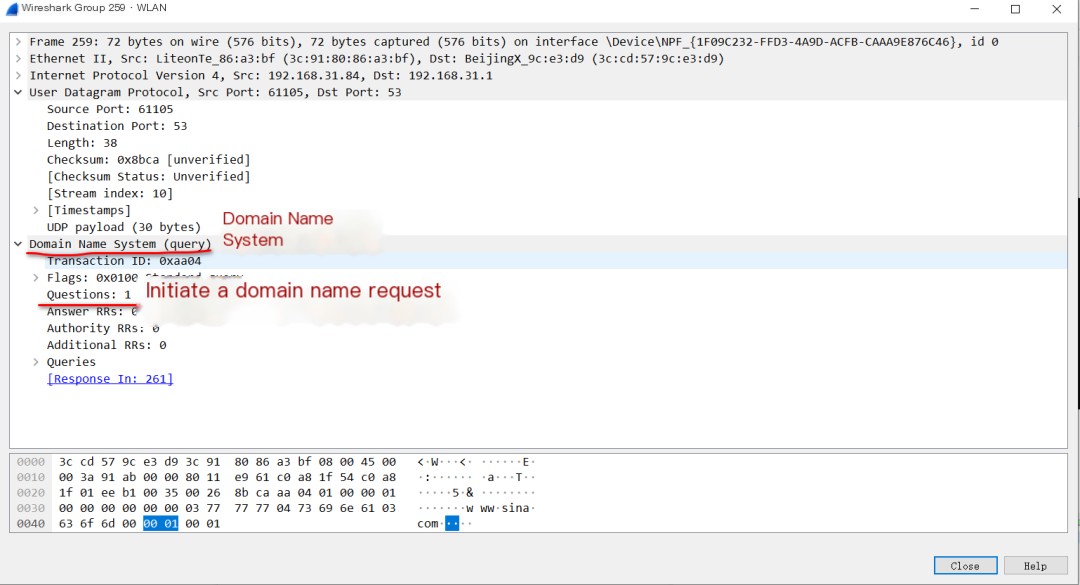
2. Below is the domain name resolution returned by the gateway:
Double-click the second packet to view details:
It is also based on a UDP protocol. Because the gateway returns it to me, the source and destination IP and source and destination ports are swapped, with everything else unchanged.
The content of the DNS protocol:
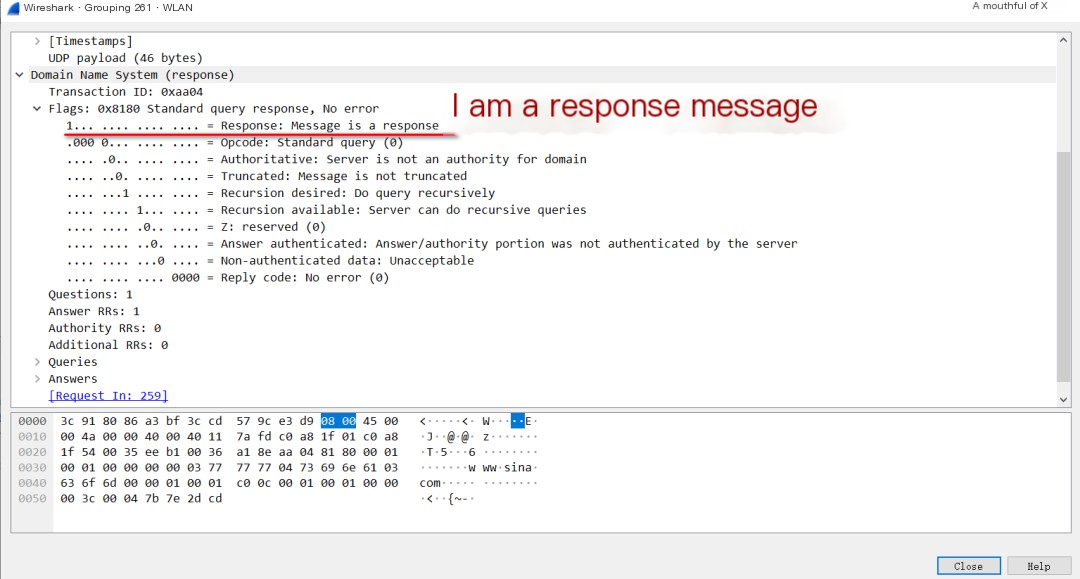
The response message contains an “Answers” section, which is an answer provided to you.
Content inside the Answers section:
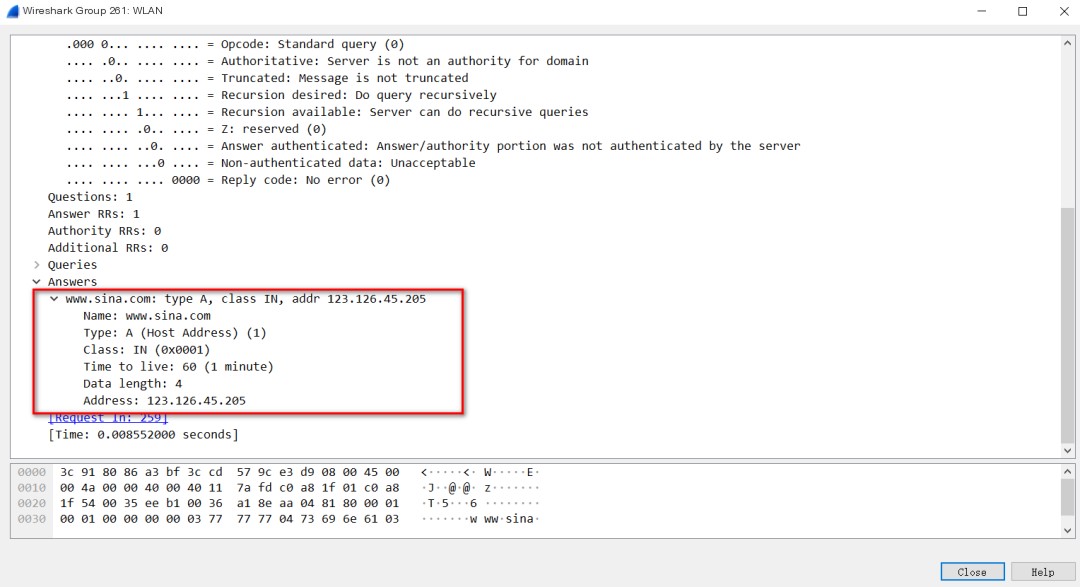
The packet reveals a step-by-step lookup that finally retrieves the IP address. The client is informed of the IP address, and through this process, the client obtains the IP address. The client pings, interacting directly with the IP address.
Except for images marked as “images from the internet”, all other images in the article are drawn by me. Computer knowledge is the same; if there are similarities, it is purely coincidental.



