0x00 Introduction
Cobalt Strike is a powerful tool commonly used for post-exploitation. This tool is designed for team-based operations, allowing information sharing and supporting multiple communication protocols. It integrates features such as port forwarding, port scanning, socket proxying, privilege escalation, phishing, and more. In addition to its built-in capabilities, Cobalt Strike also leverages functionalities from other well-known tools like Metasploit and Mimikatz.
0x01 Cobalt Strike Architecture
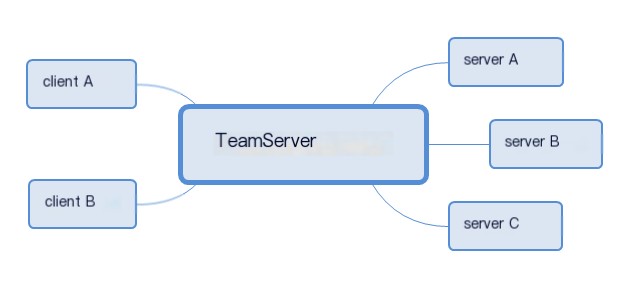
File Structure
Copy
│ agscript - Scripts for extending functionality
│ c2lint - Checks for errors in the profile
│ cobaltstrike
│ cobaltstrike.jar - Client program
│ icon.jpg
│ license.pdf
│ readme.txt
│ releasenotes.txt
│ teamserver - Server program
│ update
│ update.jar
│
└─third-party - Third-party tools
README.vncdll.txt
vncdll.x64.dll
vncdll.x86.dllCustomization
- Cobalt Strike can be enhanced using AggressorScripts, which allow for menu extensions, Beacon command-line modifications, privilege escalation scripts, and more.
- The communication configuration file for Cobalt Strike is called Malleable C2, which allows you to modify CS’s communication characteristics and the behavior of the Beacon payload.
- Cobalt Strike supports integrating with other communication frameworks through ExternalC2. ExternalC2 is a specification/framework proposed by Cobalt Strike that enables hackers to extend the default HTTP(S)/DNS/SMB C2 communication channels as needed.
Overall, CS offers powerful customization options and is highly flexible. We will cover its usage in later sections.
0x02 Execution
Cobalt Strike requires a team server to function, known as the teamserver. The necessary files are `teamserver` and `cobaltstrike.jar`, which can be hosted on a public server if needed.
Starting the Team Server
Copy
Run sudo ./teamserverSure! Please provide the content you’d like me to rewrite in English, including the keyword **socket proxying**.
Copy
./teamserver [/path/to/c2.profile] [YYYY-MM-DD]
t is the (default) IP address of this Cobalt Strike team server
t is the shared password to connect to this server
t[/path/to/c2.profile] is your Malleable C2 profile
t[YYYY-MM-DD] is a kill date for Beacon payloads run from this serverSure! Please provide the content you’d like me to rewrite in English, including the keyword **socket proxying**.
If you are not using a custom Malleable C2 profile, you only need to specify the host and password.
Sure! Please provide the content you’d like me to rewrite in English, including the keyword **socket proxying**.
Sure! Please provide the content you’d like me to rewrite in English, including the keyword **socket proxying**.
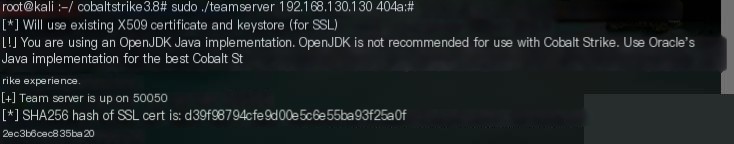
Start CS with `./cobaltstrike.jar`
Sure! Please provide the content you’d like me to rewrite in English, including the keyword **socket proxying**.
Sure! Please provide the content you’d like me to rewrite in English, including the keyword **socket proxying**.
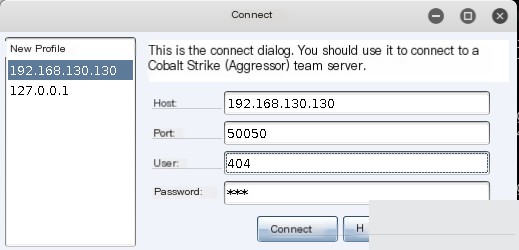
The `user` field is where you enter your desired username, and `password` is the password used to start the teamserver.
Sure! Please provide the content you’d like me to rewrite in English, including the keyword **socket proxying**.
Sure! Please provide the content you’d like me to rewrite in English, including the keyword **socket proxying**.
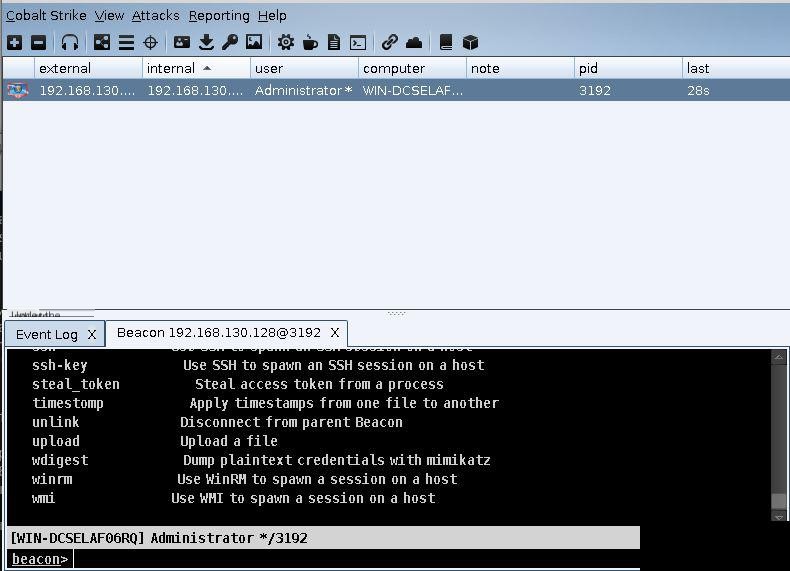
Enter the main interface
0x03 Menu Functions
Cobalt Strike
 Copy
Copy
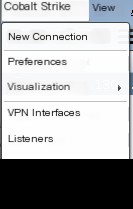
New Connection // Create a new connection
Preferences - Settings
Visualization - Window view mode
V** interfaces - V** access
Listeners - Listener management
Script Manager - Script management
Close - ExitThe `Preferences` section allows you to delete login records, account passwords, and team server SSL settings. Other options include software color themes and general settings.
View
 Copy
Copy
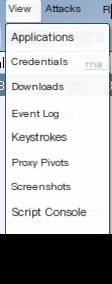
Applications - Displays target browser, OS, and Flash version obtained via System Profiler
Credentials - Shows all acquired user hashes
Downloads - Displays downloaded files
Event log - Logs team activities and target connections
Keystrokes - Records target keystrokes
Proxy Pivots - Proxy information
Screenshots - Captured screenshots
Script Console - Loads custom scripts
Targets - Displays all hosts
Web log - Web service logsAttack
 Copy
Copy
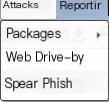
Packages
HTML Application - Generates an HTA file
MS Office Macro - Creates an Office macro file
Payload Generator - Generates payloads in various languages
USB/CD AutoPlay - Uses autoplay to execute a controlled file
Windows Dropper - Binds payloads to legitimate files
Windows Executable - Generates an executable payload (commonly used)
Windows Executable (S) - Generates a stageless executable payload with additional featuresCopy
Web Drive-by
Manage - Manages all active web services
Clone Site - Clones a website
Host File - Hosts a file for web-based downloads
Scripted Web Delivery - Provides a web service for downloading and executing payloads
Signed Applet Attack - Starts a web service to deliver a self-signed Java applet
Smart Applet Attack - Detects Java versions and exploits known vulnerabilities to bypass security
System Profiler - Retrieves system, Flash, and browser version detailsCopy
Spear Phish - Spear phishing attackReporting
 Copy
Copy
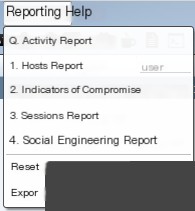
Activity report - Activity logs
Hosts report - Host reports
Indicators of Compromise - Threat reports
Sessions report - Session reports
Social engineering report - Social engineering analysis0x04 Right-Click Functions
 Copy
Copy
Interact - Open Beacon
Access
tdump hashes - Retrieve hashes
tElevate - Privilege escalation
tGolden Ticket - Generate and inject a Golden Ticket
tMake token - Credential manipulation
tRun Mimikatz - Execute Mimikatz
tSpawn As - Generate a Cobalt Strike listener under another userBeacon
beacon> help
Beacon Commands
===============
Command Description
------- -----------
browserpivot Setup a browser pivot session
bypassuac Spawn a session in a high integrity process
cancel Cancel a download that's in-progress
cd Change directory
checkin Call home and post data
clear Clear beacon queue
covertV** Deploy Covert V** client
cp Copy a file
dcsync Extract a password hash from a DC
desktop View and interact with target's desktop
dllinject Inject a Reflective DLL into a process
download Download a file
downloads Lists file downloads in progress
drives List drives on target
elevate Try to elevate privileges
execute Execute a program on target
exit Terminate the beacon session
getsystem Attempt to get SYSTEM
getuid Get User ID
hashdump Dump password hashes
help Help menu
inject Spawn a session in a specific process
jobkill Kill a long-running post-exploitation task
jobs List long-running post-exploitation tasks
kerberos_ccache_use Apply kerberos ticket from cache to this session
kerberos_ticket_purge Purge kerberos tickets from this session
kerberos_ticket_use Apply kerberos ticket to this session
keylogger Inject a keystroke logger into a process
kill Kill a process
link Connect to a Beacon peer over SMB
logonpasswords Dump credentials and hashes with mimikatz
ls List files
make_token Create a token to pass credentials
mimikatz Runs a mimikatz command
mkdir Make a directory
mode dns Use DNS A as data channel (DNS beacon only)
mode dns-txt Use DNS TXT as data channel (DNS beacon only)
mode dns6 Use DNS AAAA as data channel (DNS beacon only)
mode http Use HTTP as data channel
mode smb Use SMB peer-to-peer communication
mv Move a file
net Network and host enumeration tool
note Assign a note to this Beacon
portscan Scan a network for open services
powerpick Execute a command via Unmanaged PowerShell
powershell Execute a command via powershell.exe
powershell-import Import a powershell script
ppid Set parent PID for spawned post-ex jobs
ps Show process list
psexec Use a service to spawn a session on a host
psexec_psh Use PowerShell to spawn a session on a host
psinject Execute PowerShell command in specific process
pth Pass-the-hash using Mimikatz
pwd Print current directory
rev2self Revert to original token
rm Remove a file or folder
rportfwd Setup a reverse port forward
runas Execute a program as another user
runu Execute a program under another PID
screenshot Take a screenshot
shell Execute a command via cmd.exe
shinject Inject shellcode into a process
shspawn Spawn process and inject shellcode into it
sleep Set beacon sleep time
socks Start SOCKS4a server to relay traffic
socks stop Stop SOCKS4a server
spawn Spawn a session
spawnas Spawn a session as another user
spawnto Set executable to spawn processes into
spawnu Spawn a session under another PID
ssh Use SSH to spawn an SSH session on a host
ssh-key Use SSH to spawn an SSH session on a host
steal_token Steal access token from a process
timestomp Apply timestamps from one file to another
unlink Disconnect from parent Beacon
upload Upload a file
wdigest Dump plaintext credentials with mimikatz
winrm Use WinRM to spawn a session on a host
wmi Use WMI to spawn a session on a host

