Here’s an introduction to iptables with a focus on the chain rules concept:
“Iptables is a powerful tool used in Linux
netfilter/iptables (commonly referred to as iptables) is a packet filtering firewall on the Linux platform. Like most Linux software, this packet filtering firewall is free. It can replace costly commercial firewall solutions by providing features such as packet filtering, packet redirection, and Network Address Translation (NAT).
Basics of iptables
Rules are essentially predefined conditions set by network administrators. These rules are defined typically as “if a packet header matches certain conditions, then process the packet in a specific manner.” Rules are stored in the kernel’s packet filtering table, specifying source addresses, destination addresses, transport protocols (e.g., TCP, UDP, ICMP), and service types (e.g., HTTP, FTP, SMTP). When a packet matches a rule, iptables will handle it according to the defined actions, such as accepting, rejecting, or dropping the packet. The main task of configuring a firewall is to add, modify, and delete these rules.
Relationship between iptables and netfilter: chain rules
This is the first point worth mentioning. The relationship between iptables and netfilter can be quite unclear. Many people know about iptables but not netfilter. In fact, iptables is only a management tool for the Linux firewall located at /sbin/iptables. The true firewall functionality is implemented by netfilter, which is the internal structure within the Linux kernel that performs packet filtering.
Packet processing workflow of iptables
① When a packet arrives at the network card, it first enters the PREROUTING chain, where the kernel determines whether the packet needs to be routed based on its destination IP.
② If the packet is meant for the local machine, it moves downward to the INPUT chain. After reaching the INPUT chain, any process can receive the packet. Programs running on the local machine can send packets, which will pass through the OUTPUT chain and then be sent out via the POSTROUTING chain.
③ If the packet is to be forwarded and the kernel allows forwarding, the packet will move rightward as shown and pass through the FORWARD chain before exiting via the POSTROUTING chain.
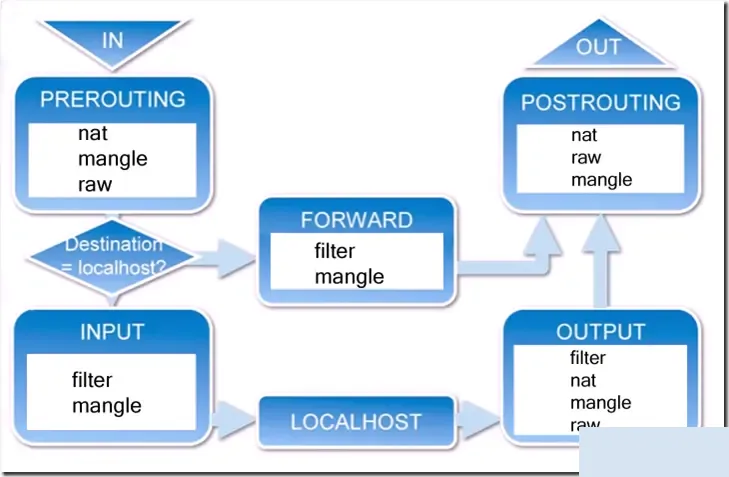
iptables: Tables and Chains
Tables provide specific functionalities. iptables has four built-in tables: the filter table, nat table, mangle table, and raw table, each serving to perform packet filtering, network address translation, packet modification, and connection tracking, respectively.
Chains are paths on which packets travel. Each chain is a checklist of numerous rules. A chain can have one or more rules. When a packet arrives at a chain, iptables starts checking from the first rule to see if the packet meets the defined conditions. If it does, the system processes the packet according to the rule; otherwise, iptables continues checking the next rule. If the packet doesn’t match any rule in the chain, iptables handles the packet according to the chain’s predefined default policy.
iptables uses a layered structure of “tables” and “chains.” In REHL4, there are three tables and five chains, but in REHL5, there are four tables and five chains. However, the additional table is not used frequently, so it remains largely similar to before. Here is a list of these four tables and five chains. It’s crucial to understand the relationship and roles of these tables and chains.
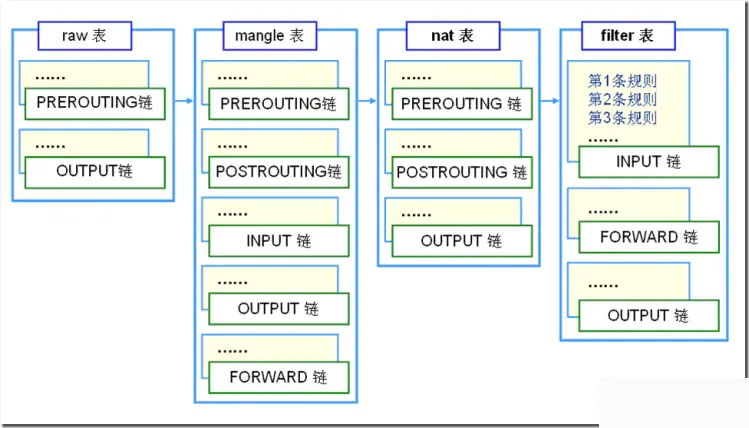
Rule Tables:
1. Filter Table—Three chains: INPUT, FORWARD, OUTPUT
Function: To filter packets. Kernel module: iptables_filter.
2. Nat Table—Three chains: PREROUTING, POSTROUTING, OUTPUT
Function: Used for network address translation (IP, port). Kernel module: iptable_nat
3. Mangle Table—Five chains: PREROUTING, POSTROUTING, INPUT, OUTPUT, FORWARD, acting on all chains.
Function: To modify the service type, TTL of packets, and configure routing for QOS. Kernel module: iptable_mangle (Though this table seems complicated, we rarely use it when setting policies.)
4. Raw Table—Two chains: OUTPUT, PREROUTING
Function: To decide if a packet is subject to the state tracking mechanism. Kernel module: iptable_raw
(This table is not present in REHL4 but is not frequently used.)
The most important and commonly used are Filter and Nat tables.
Rule Chains:
1. INPUT—Applies the policies of this rule chain to incoming packets.
2. OUTPUT—Applies the policies of this rule chain to outgoing packets.
3. FORWARD—Applies the policies of this rule chain when forwarding packets.
4. PREROUTING—Rules applied to packets before they are routed.
(Note! All incoming packets are processed by this chain first.)
5. POSTROUTING—Rules applied to packets after they are routed.
(All outgoing packets are processed by this chain first.)
Priority Order of Rule Tables:
Raw—mangle—nat—filter
Priority Order among Rule Chains (divided into three scenarios):
Scenario One: Incoming Traffic Flow
Packets arriving from outside are first processed by the PREROUTING chain (e.g., whether the address of the packet should be modified). Routing then determines where the packet should be sent. If the packet
targets the firewall itself (e.g., Internet users accessing a web server hosted on the firewall), it is then processed by the INPUT chain (to decide if it should be allowed), and finally handed over to the system’s higher-level application (like an Apache server) to respond.
Scenario Two: Forwarded Traffic Flow
Packets from outside reach the firewall and are first processed by the PREROUTING chain. After routing, if the destination address of the packet is another external address (e.g., a LAN user accessing the QQ website via a gateway), the kernel passes the packet to the FORWARD chain for processing (to decide whether to forward or block it). It is then handed to the POSTROUTING chain (to decide whether to modify the packet’s address).
Scenario Three: Outgoing Traffic Flow
Packets sent from the firewall itself to external addresses (e.g., testing a public DNS server from the firewall) are first processed through the OUTPUT chain, then routed, and finally passed to the POSTROUTING chain for further processing (e.g., whether to modify the packet’s address).
Management and Configuration of iptables Rules
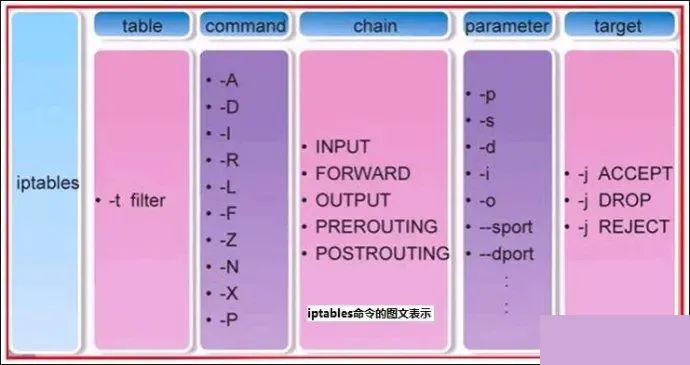
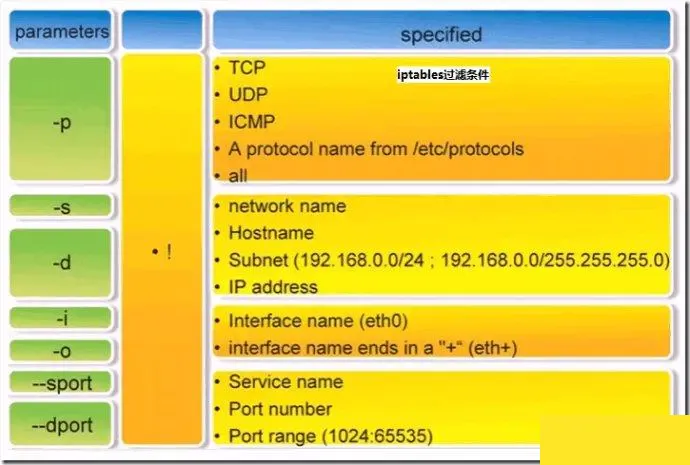
Basic Syntax of iptables
iptables [-t table_name] command_option [chain_name] [condition_match] [-j target_action_or_jump]
Explanation: Table names and chain names specify the tables and chains the iptables command operates on. Command options designate how iptables rules are managed (e.g., inserting, adding, deleting, viewing), and condition matching specifies the conditions packets must meet to be processed. The target action or jump specifies how the packet should be handled (e.g., allowed, rejected, dropped, or jumped to another chain).
Management Control Options for iptables Commands
-A Append a new rule to the end of a specified chain
-D Delete a specific rule in a chain by rule number or content
-I Insert a new rule into a specified chain, default is adding the first line
-R Replace a specific rule in a chain by rule number or content
-L List all rules in a specified chain
-E Rename a user-defined chain without changing the chain itself
-F Clear all rules
-N Create a new user-defined chain
-X Remove a user-defined chain from a specified table
-P Set the default policy for a specified chain
-Z Zero the byte and packet counters of all chains in all tables
-n Display output in numeric format
-v View detailed verbose information of rule tables
-V View version information
-h Access the help menu
Four Methods of Handling Packets by Firewalls
ACCEPT Permit a packet to pass through
DROP Discard the packet without any response
REJECT Deny passage of the packet, possibly sending a response back to the sender
LOG Record log information in /var/log/messages and forward the packet to the next rule
Saving and Restoring iptables Firewall Rules
iptables-save stores rules to a file, which is automatically loaded by scripts in the rc.d directory (/etc/rc.d/init.d/iptables).
To save rules, use the command iptables-save. A common usage is:
iptables-save > /etc/sysconfig/iptables
This command generates a file in /etc/sysconfig/iptables that saves the rules.
Alternatively, use:
service iptables save
This automatically stores rules in /etc/sysconfig/iptables.
Upon system startup, a script in rc.d uses the command iptables-restore to load this file, thereby automatically restoring the rules.
Deleting the First Rule in the INPUT Chain
iptables -D INPUT 1
Commonly Used iptables Firewall Policies
1. Reject all ICMP protocol packets entering the firewall
iptables -I INPUT -p icmp -j REJECT
2. Allow the firewall to forward all packets except those using the ICMP protocol
iptables -A FORWARD -p ! icmp -j ACCEPT
Note: Use “!” to negate a condition.
3. Reject packets forwarded from the host 192.168.1.10 but allow packets from the 192.168.0.0/24 subnet
iptables -A FORWARD -s 192.168.1.11 -j REJECT
iptables -A FORWARD -s 192.168.0.0/24 -j ACCEPT
Note: Ensure the rejection rule is placed first; otherwise, it will have no effect.
4. Drop packets with private source addresses entering the firewall from the external network interface (eth1)
iptables -A INPUT -i eth1 -s 192.168.0.0/16 -j DROP
iptables -A INPUT -i eth1 -s 172.16.0.0/12 -j DROP
Description: This usage is particularly suitable for remote management of devices, such as when an SQL server located at a branch office needs to be managed by administrators from the main office.
7. Allow the local machine to open applications provided by TCP ports 20-1024.
8. Allow forwarding of DNS resolution request packets from the 192.168.0.0/24 local network segment.
9. Prevent other hosts from pinging the firewall host, but allow pings from the firewall to other hosts.
10. Block forwarding packets from and to a host with the MAC address 00:0C:29:27:55:3F.
Description: iptables uses the “-m module keyword” format to invoke display matches. Here we use “-m mac –mac-source” to indicate the source MAC address of the packet.
11. Allow the firewall local machine to open TCP ports 20, 21, 25, 110, and passive mode FTP ports 1250-1280 to the outside.
Description: Here we use “-m multiport –dport” to specify the destination ports and range.
12. Prohibit forwarding TCP packets with source IP addresses from 192.168.1.20-192.168.1.99.
Description: Use “-m –iprange –src-range” here to specify the IP range.
13. Block forwarding of non-syn request packets unrelated to normal TCP connections.
Description: “-m state” signifies the connection state of the packet, with “NEW” indicating it’s not related to any existing connections.
14. Deny access to new packets at the firewall but allow responsive connections or packets related to existing connections.
Description: “ESTABLISHED” represents packets that have responded to requests or have established connections, while “RELATED” indicates connections related to established sessions, such as FTP data connections.
15. Only open the local machine’s web services (80), FTP (20, 21, 20450-20480), allow response packets from other servers’ ports, and discard all other incoming packets.
Common Linux iptables Rules
# 1. Delete all existing rules
# 2. Set default chain policies
# 3. Block a specific IP address
# 4. Allow all incoming SSH
# 5. Allow SSH only from a specific network
# 6. Allow incoming HTTP
# 7. Multiport (allow incoming SSH, HTTP, and HTTPS)
# 8. Allow outgoing SSH
# 9. Allow outgoing SSH but only access a specific network
# 10. Allow outgoing HTTPS
# 11. Load balance incoming HTTPS traffic
# 12. Ping from inside to outside
# 13. Ping from outside to inside
# 14. Allow loopback access
# 15. Allow packets from the intranet to access the internet
# 16. Allow outgoing DNS
# 17. Allow NIS connections
# 18. Allow a specific network rsync access to this machine
# 19. Only allow MySQL connections from a specific network
# 20. Allow Sendmail or Postfix
# 21. Allow IMAP and IMAPS
# 22. Allow POP3 and POP3S
# 23. Prevent DoS attacks
# 24. Forward port 422 to port 22
# 25. Log dropped packets
References
Official iptables website
iptables configuration manual
iptables configuration tutorial


