Before officially sharing, let me give a brief introduction to Wireshark. Previously known as Ethereal, this open-source software functions as its name suggests, uncovering the details of Ethernet. It is widely used for analyzing network traffic, including examining the TCP protocol.

Wireshark can capture network packets and display the most detailed network packet information as possible. By analyzing the captured packets, one can understand the user’s behavior and the content of the transmitted data.
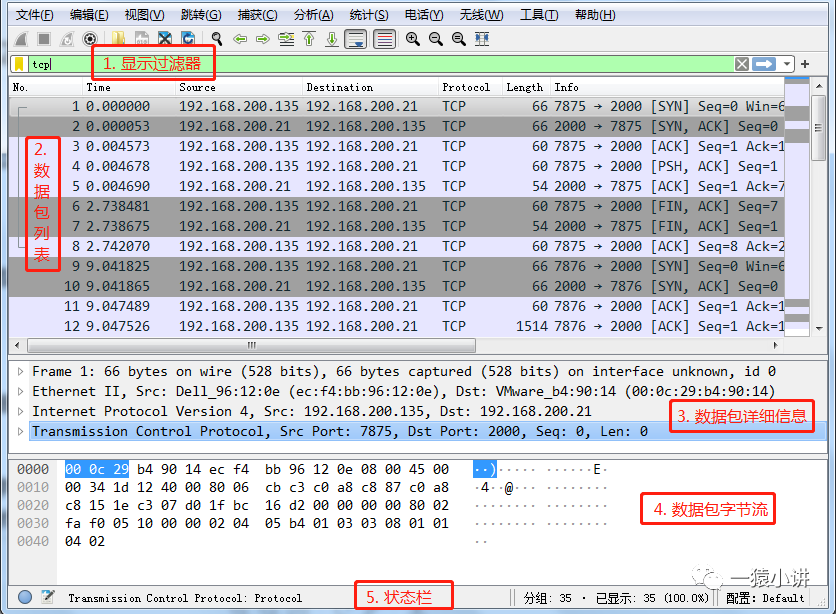
As shown in the figure above, the main interface of Wireshark primarily includes a display filter, packet list, packet details, packet byte stream, and a status bar. Here, it’s important to mention filter expressions, which are very helpful for quickly pinpointing problems in daily usage.
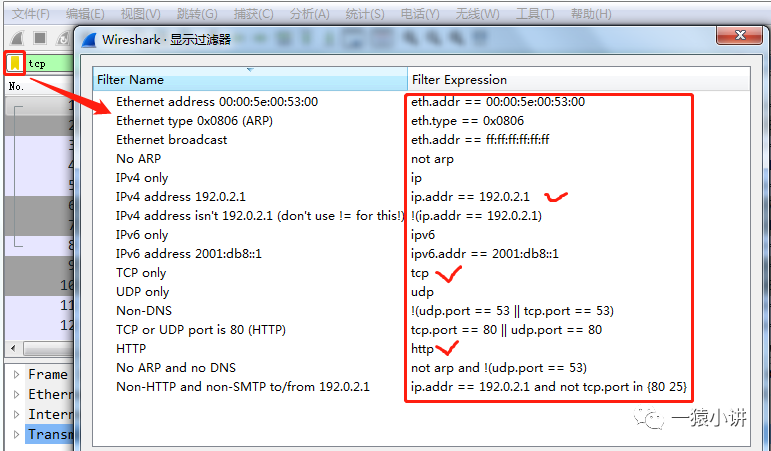
As shown in the figure, Wireshark has many built-in filter expressions, and the tool itself performs strict verification on the input filter expressions. To lay the groundwork for subsequent sharing and to help users get started quickly, I’ll briefly summarize some commonly used filtering methods (keep in mind: those not listed are not necessarily unimportant).
| Filter by Protocol | tcp, only display TCP protocol |
|---|---|
| Filter by IP Address | ip.src == 192.168.200.135, filter packets with a source address of 192.168.200.135; ip.dst == 192.168.200.21, filter packets with a destination address of 192.168.200.21; |
| Filter by Port | tcp.port == 80, display packets with TCP port 80; tcp.srcport == 80, display packets where the source port of the TCP protocol is 80 |
| Filter by HTTP Method | http.request.method == “GET”, only display packets with the HTTP GET method. |
| Filter using Logical Operations | Example: ip.src == 192.168.1.13 or ip.src == 192.168.1.16 |
It’s just a tool software; go ahead and experiment, and you’ll figure out how to use it. Specific operations will not be elaborated on here. Next, let’s discuss the TCP three-way handshake and four-way teardown, commonly mentioned in interviews, by capturing packets with Wireshark.
When a user accesses a website, a connection is first established using the TCP protocol before an HTTP request is sent to obtain the website’s content. The server’s response to the client is also transmitted via the TCP protocol.
The TCP protocol is a transport layer protocol in the Internet, primarily establishing connections using a three-way handshake and disconnecting using a four-way handshake.
Before formally analyzing the data packets of TCP protocol connection establishment, let’s introduce its working principle to help users more easily understand the transmitted data packets. The process of the TCP protocol’s three-way handshake is shown in the figure below.
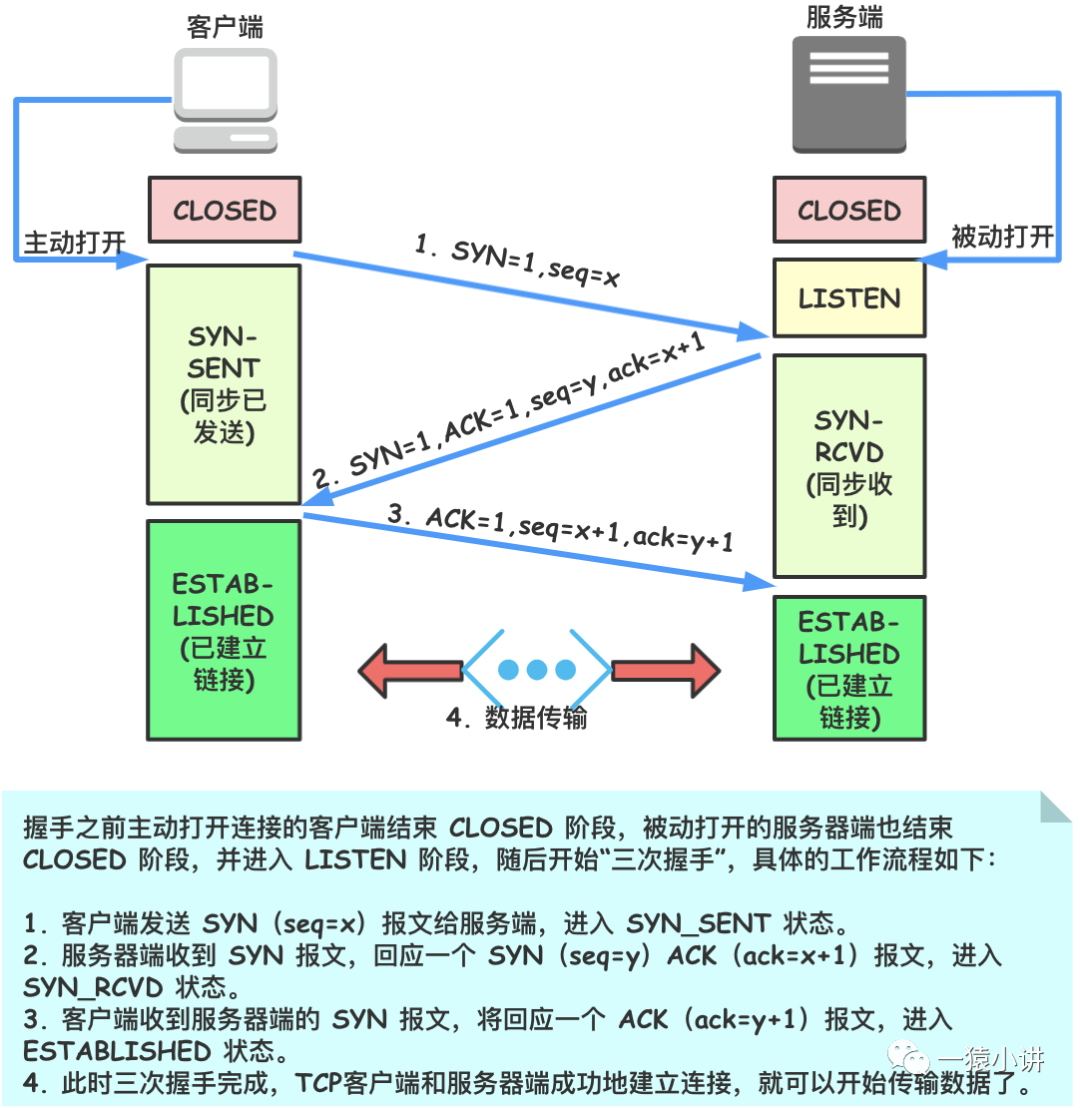
From understanding the TCP three-way handshake, we know that the TCP protocol establishes connections by sending packets with different flag positions (such as SYN, SYN+ACK, ACK), and each request and response has a different sequence number. Next, let’s analyze by capturing packets with Wireshark.
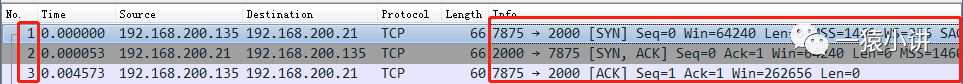
The figure above shows the complete “three-way handshake” process when establishing a TCP connection, where 7875 -> 2000, 7875 is the client’s port, and 2000 is the server’s port. The three exchanges between port 7875 and port 2000 constitute the “three-way handshake” process.
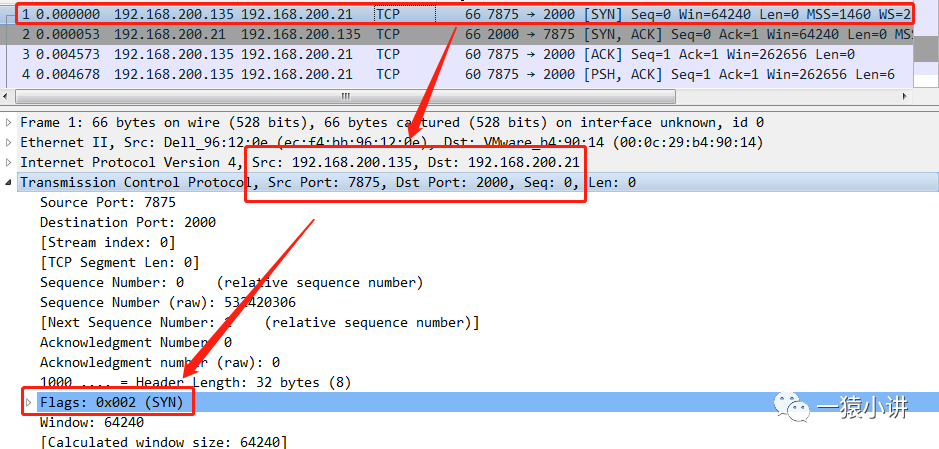
The TCP message sent by the client uses [SYN] as the flag position, and the client sequence number Seq=0.
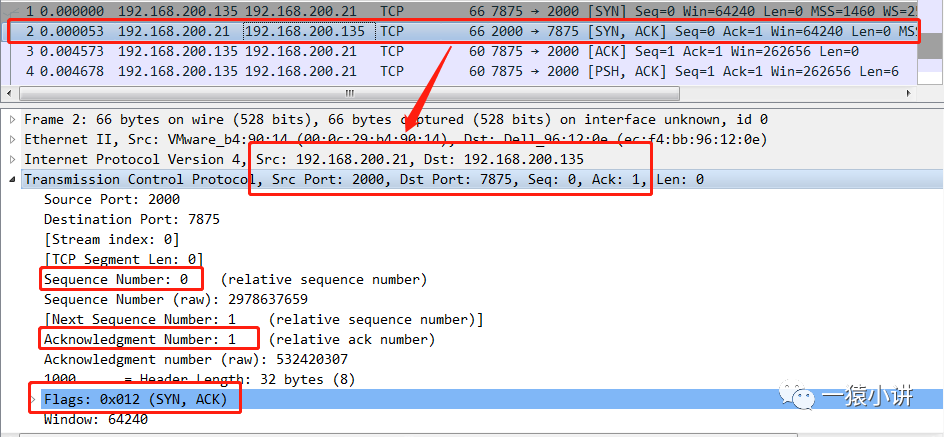
The TCP message returned by the server uses [SYN, ACK] as the flag position; and the server-side sequence number Seq=0; acknowledgment number Ack=1, which is the client sequence number Seq value +1 in the “first handshake”.
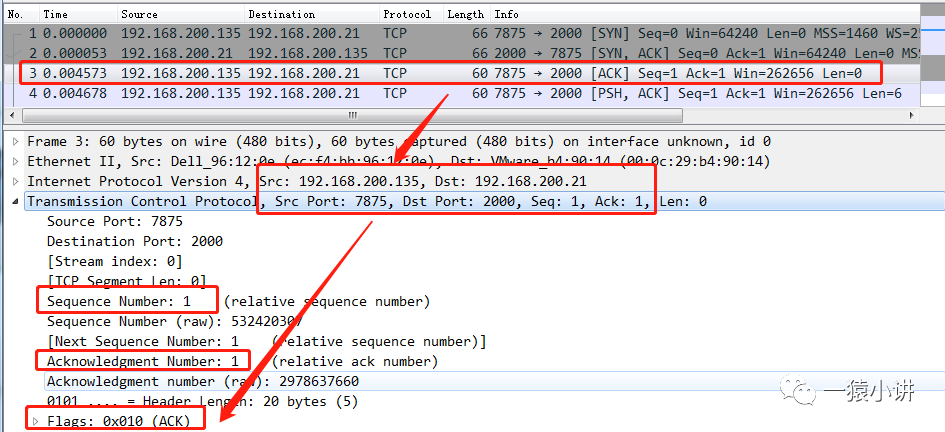
The TCP message sent by the client to the server uses [ACK] as the flag position; the client sequence number Seq=1, which is the server acknowledgment number Ack value in the “second handshake”; acknowledgment number Ack=1, which is the server sequence number Seq value +1 in the “second handshake”.
Now, looking back at the process diagram of the TCP protocol’s three-way handshake, it shouldn’t seem so unfamiliar. If it’s still very unfamiliar, go through it several more times (the idea that practice leads to perfection applies here), and I suggest capturing packets and analyzing them yourself with Wireshark.
Establishing a connection with the TCP protocol requires a three-way handshake, while disconnecting requires a four-way teardown, the process of which is shown in the figure below.
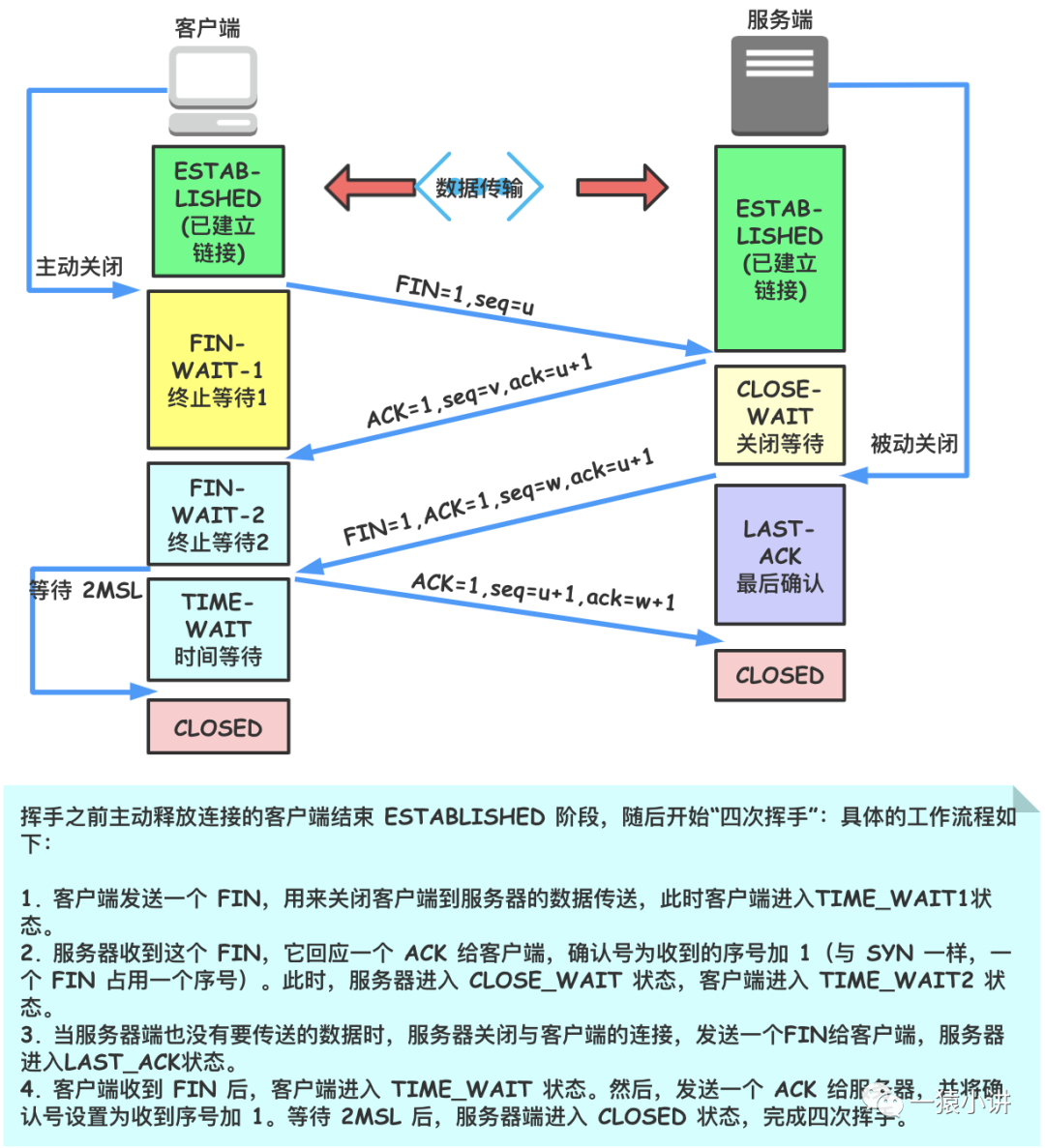
For those interested, I hope you can use Wireshark personally to analyze the TCP four-way teardown. We won’t elaborate on it this time, but hope to demonstrate the TCP four-way teardown next time when exploring HTTP protocol packets.
It has been 10 years since I first encountered Wireshark, but it was only recently that I truly started to promote the use of this software within my team to analyze issues because the team I am responsible for interacts a lot with banks and third parties. This often results in inefficiencies due to back-and-forth blaming and finger-pointing. I hope to bring problems to the forefront so that boundary issues caused by network environments become increasingly clear.
Considering I’m not a Wireshark expert, I will combine the problems encountered by my team and try to consult as many resources and books as possible. I hope each sharing can be accurate and genuinely beneficial to everyone.
This concludes the Wireshark sharing for this time. Next, we’ll use Wireshark to explore HTTP packets (there’s really no privacy), so stay tuned.
We will continue to deliver original, exciting content, so stay tuned!



