“`html
WireShark+Winhex: A Great Pair for Traffic Analysis
WireShark+Winhex: A Great Pair for Traffic Analysis
 />
/>1. Advanced Wireshark traffic analysis, including decoding, stream tracking, and file export.2. Utilize HackBar for base64 URL encoding conversion.3. Use WinHex to restore files from network traffic.4. Discuss common image file and compressed file header tags, and their sensitivity to excess delimiters.
Here we use a recently challenging traffic analysis question from the Anheng Cup as an example for explanation, the topic is called “Chinese Broadsword 666”. Link to download the topic traffic package: https://pan.baidu.com/s/1c2WFQ3Q password: v0e7. The format is pcapng encapsulation, here opened with wireshark:
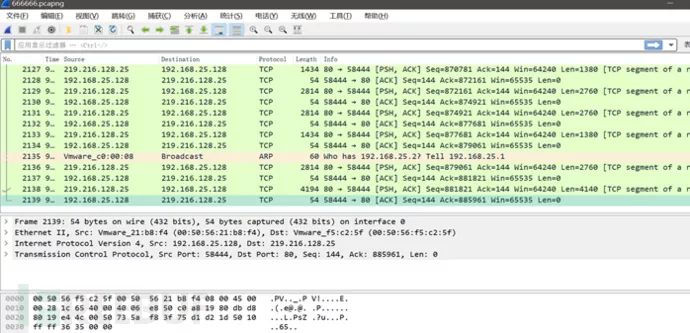 />
/>A total of 2139 packets, mentioning Chinese Broadsword, thinking it might be web-related, first try entering http in the filter above to show http packets:
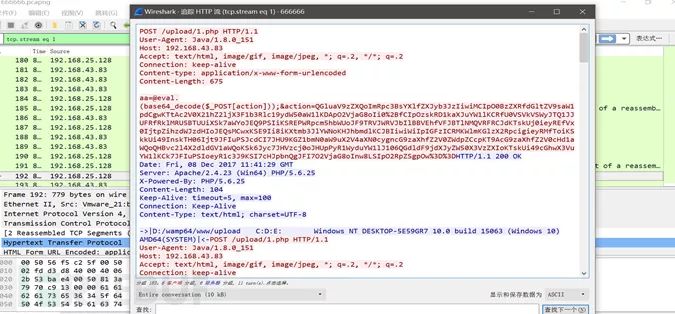
First, randomly click on a message, right-click – track stream – http stream, we can see a lot of red and blue message parsing, red represents sent, blue represents server response. We can see a long string of base64_decode, followed by alphanumeric characters, occasionally also %2B” and ”%3D”, so first thought is URL, first use hackbar’s urldecode for url decoding:
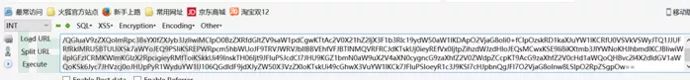
Here, after removing some “%” escapes, it becomes true base64 encoding, we use base64_decode for further conversion:

There are many similar conversions here:
Have you seen the final upload? It’s highly possible that during the intrusion process, a web shell will be uploaded, then connected with Chinese Broadsword. We observe that there are not many http message entries, take the message, according to the general invasion ideas and sequence to repeatedly analyze using the methods mentioned above:
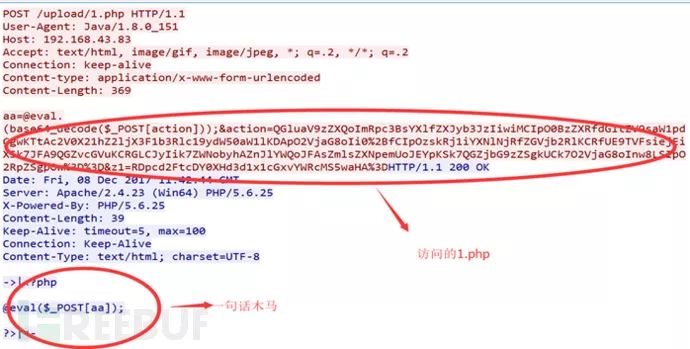
Here there is a sentence trojan, verifying the invasion idea assumption. This is also why our filtered http messages have a large number of 1.php names, we then trace back and find:
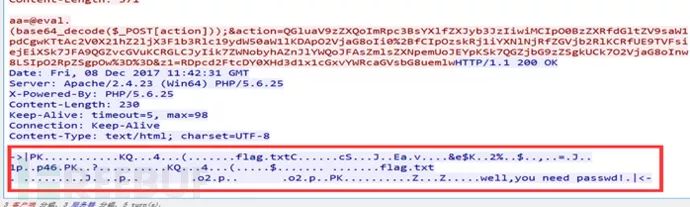
The answer is inside, hinting that a password is needed. Let’s check the raw data of the traffic to see the corresponding file type:
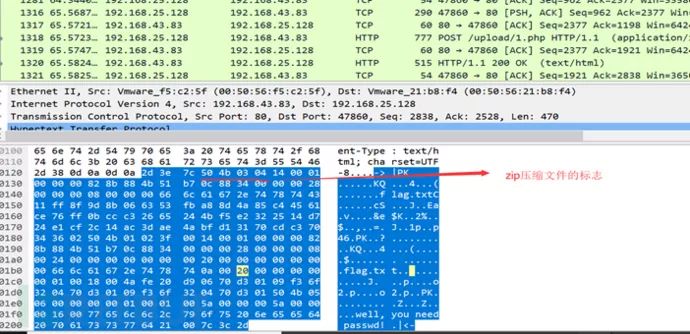
Here we need to know, generally speaking, seeing pk is very likely a zip compressed file, besides this, you need to know:
50 4B 0304: This is the header file marker 14 00: Decompression file requires pkware version 00 00: Global method bit flag (whether encrypted) 08 00: Compression method 07 76: Last modified file time F2 48: Last modified file date
Interested comrades can try this is pseudo-encryption, of course, the hint that follows “you need password” suggests this is not pseudo-encryption, there are two schemes below:
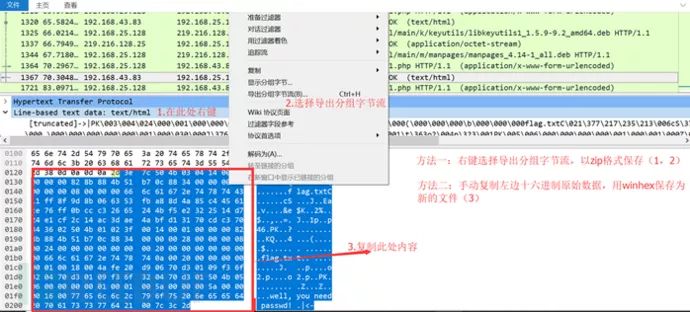
Here we choose method one, later on. We successfully save the file as hello.zip when we open it, we will find that a password must be entered:
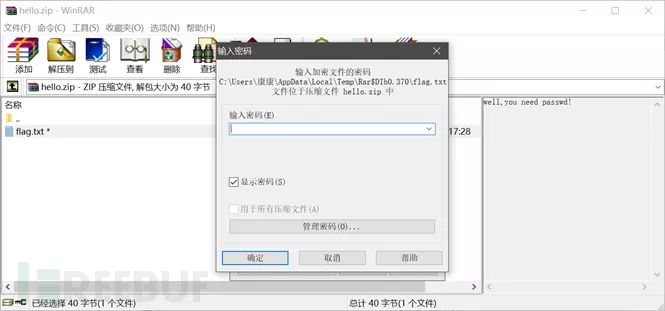
One thing to note here is that if you are careful, you will find that the saved file, when opened with winhex, has added things to distinguish between different protocol layers, but because zip compressed files are not sensitive to delimiters, you can directly identify 50 4B 03 onwards, so even with delimiters you can successfully open the document:
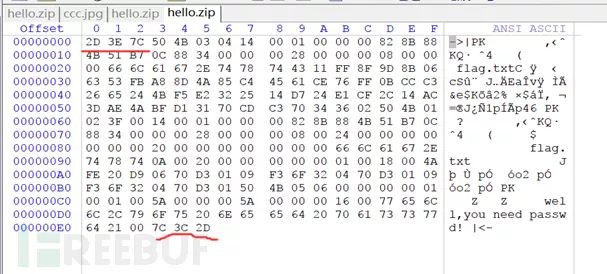
Alright, so far, this traffic analysis is only half done, we still need to know what the password for decompression is. Go back to the message, search upwards, and you will find a very large message:
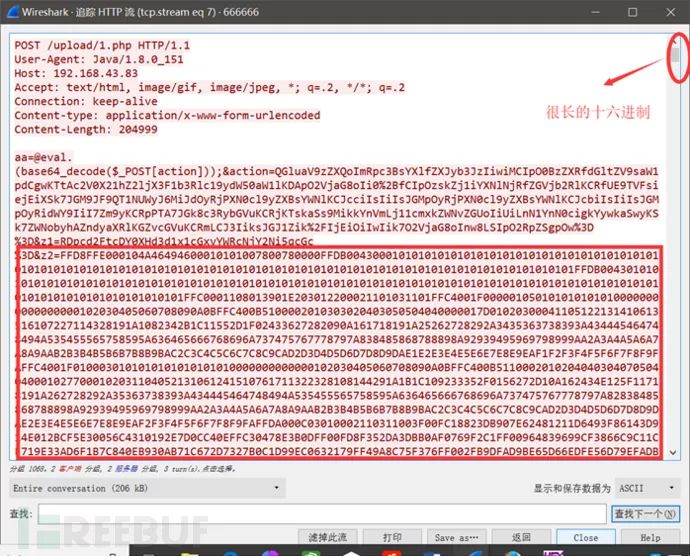
Here you have to think about what this long string is. Video? Audio? We need to remember that. We correspondingly check the information in the red box and find that the transmission is in hexadecimal characters corresponding to the original data of the image, meaning that the transmission here is the corresponding hexadecimal characters, not the image! It’s evident how sharp this question is.
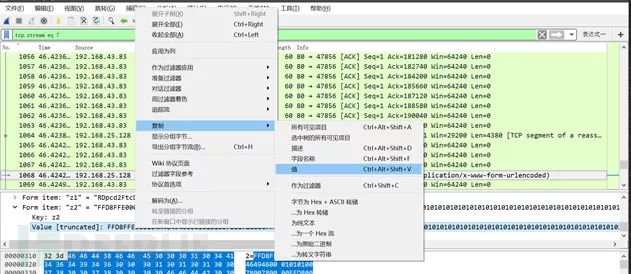
We must keep our heads clear; we only need to use these hexadecimal characters to restore the whole image, so we find the value of the corresponding data layer area z2, right-click to copy the value. Next, we use winhex to restore this kind of image: choose to create a new file around 5000 bytes, choose ASCII-HEX for copying, select OK:
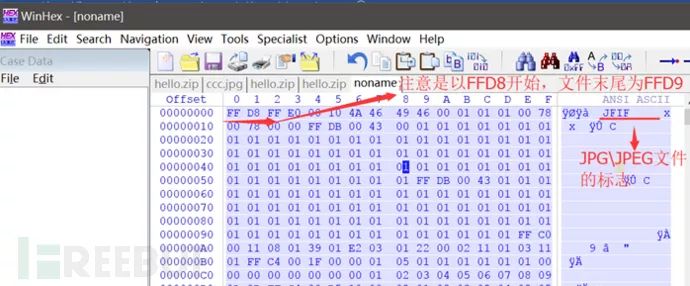
Note here that because if you copy the original hexadecimal in other situations, you must remove the 3-digit delimiters designed by wireshark; otherwise, the file cannot be opened properly! Setting the delimiter as 00 00 00 allows access, directly operating the hexadecimal code of the file is the essence of winhex! Save the file as XXX.JPG and open it:

If you find it troublesome, use an OCR tool to directly recognize the characters inside and use it to open the zip compressed file
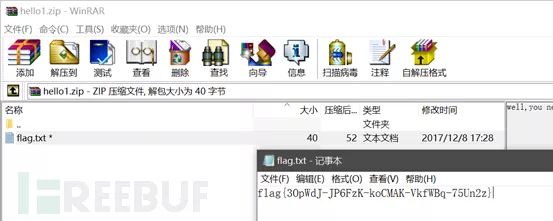
Reviewing the entire process, we notice:
1. Zip is not sensitive to delimiters, images are sensitive to delimiters. As long as you understand this, whether by any method, you can restore files.2. Zip package does physically exist, while the image containing the answer is transmitted as corresponding hexadecimal in text.3. The topic is Broadsword 666, tracing the whole traffic, it first accessed 1.php, and finally, the server returned a single sentence trojan caused while holding the site, the image is from kali, no wonder there are kali related deb files in the message, however, all these are distracting messages, the really important one is the zip and the password image.4. Most messages are not transmitted in one go, split into many shards, but in fact, we only need to see the shard, but the analysis does not feel it.
Topics introduced this time:
1. How to analyze traffic, track streams.2. How to decode base64, URL.3. Two methods for extracting files from traffic.4. File identifiers for zip packages and jpg image files, and whether they are sensitive to delimiters.5. Use winhex to restore and save files in traffic.
Community
Activities
Resources
About
Tencent Cloud Developer

Popular Products
Popular Recommendations
More Recommendations
Copyright © 2013 – 2024 Tencent Cloud. All Rights Reserved. Tencent Cloud 版权所有
Tencent Computer System Co., Ltd. ICP Filing/License Number:
Tencent Cloud Computing (Beijing) Co., Ltd. Jing ICP Certificate No.150476 | |
Copyright © 2013 – 2024 Tencent Cloud.
All Rights Reserved. Tencent Cloud 版权所有
https://cloud.tencent.com/developer/article/1073556
“`



