Introduction to the MaxMind Database
Frequent occurrences of network scanning and DDoS attacks pose a significant threat to network security. To effectively tackle these security challenges, it is crucial to deeply analyze the distribution and behavior of network traffic sources to identify potential threats. This article will explain how to use the MaxMind Database (including GeoLite2 ASN, GeoLite2 City, and GeoLite2 Country) in conjunction with Wireshark to parse and analyze IP geographical location information. It will also discuss how to utilize Wireshark’s built-in 26 Geo-related fields to accurately filter the desired feature packets and present them on the map distribution.
Obtaining the MaxMind Database
After registering and logging in, download the database package from the GeoIP database download address:

Mainly download three files:
| Database | Description |
|---|---|
| GeoLite2 ASN | AS number database |
| GeoLite2 City | City database |
| GeoLite2 Country | Country database |
To maintain relatively accurate database data, it is recommended to update the database periodically.
Configuring MaxMind Database and Field Interpretation
1. Configuring the MaxMind Database
Open Wireshark, and in the -> -> options, enable and edit the database directory, setting the directory where the database is stored:

Place the three MaxMind database files in the directory:

2. MaxMind Database Field Interpretation
Then, open any packet, if you have already opened a packet, click reload to reload the packet:
At this time, clicking on an IP header with an external IP will display a series of GeoIP database data:
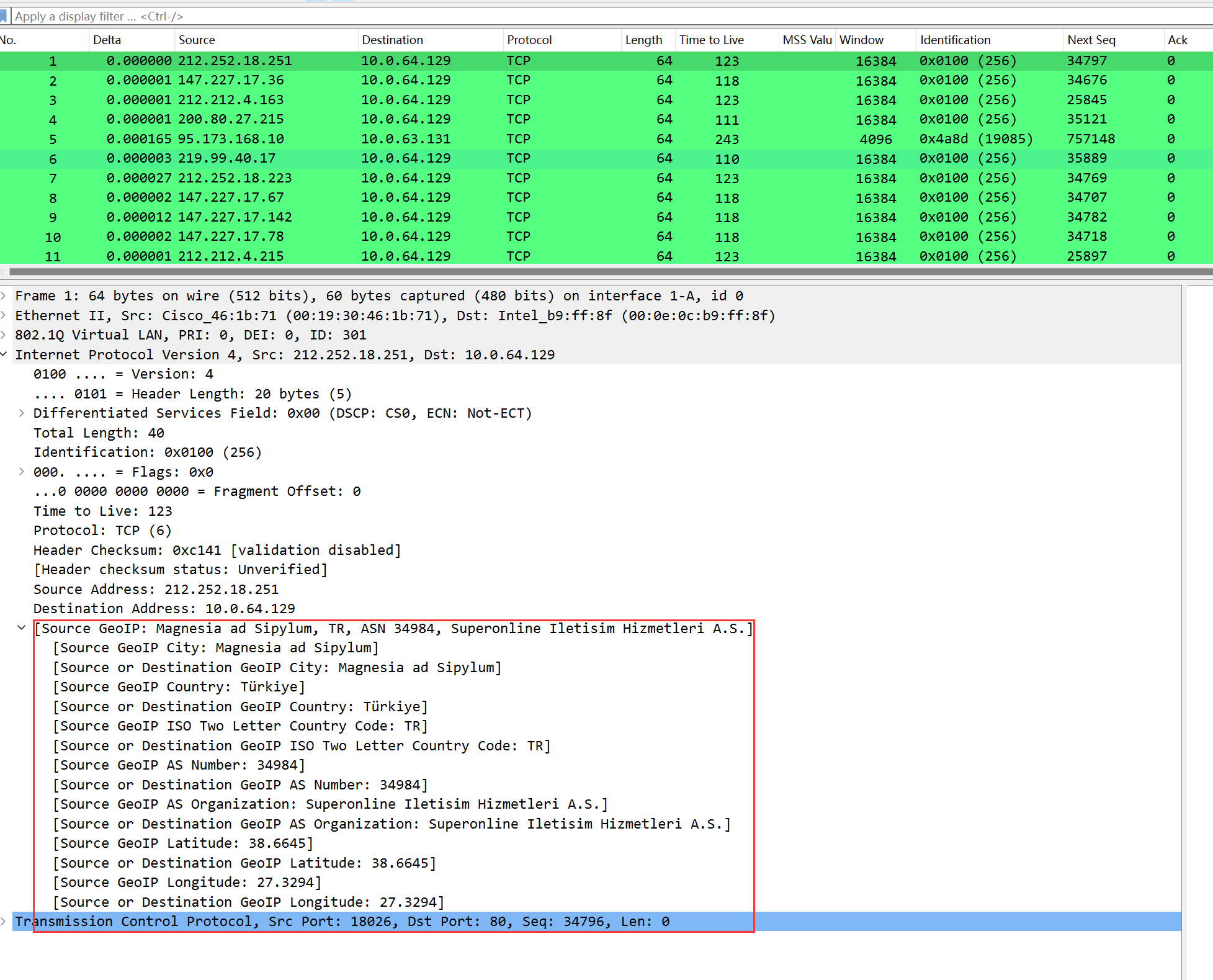
The field meanings are as follows:
| Field | Meaning |
|---|---|
| GeoIP City | City |
| GeoIP Country | Country |
| GeoIP ISO Two Letter Country Code | Defined two-letter country code |
| GeoIP AS Number | AS number |
| GeoIP AS Organization | Organization managing the corresponding AS number |
| GeoIP Latitude | Latitude |
| GeoIP Longitude | Longitude |
Private IP address segments do not involve geographical information, so private IP will not be parsed.
3. Applying MaxMind Database as a Column
To visually observe the IP geographical information, the above fields can be set as columns, for instance, we filter the SYN packets from the source:
Then set the source IP country as a column (right-click the country field–>apply as column):
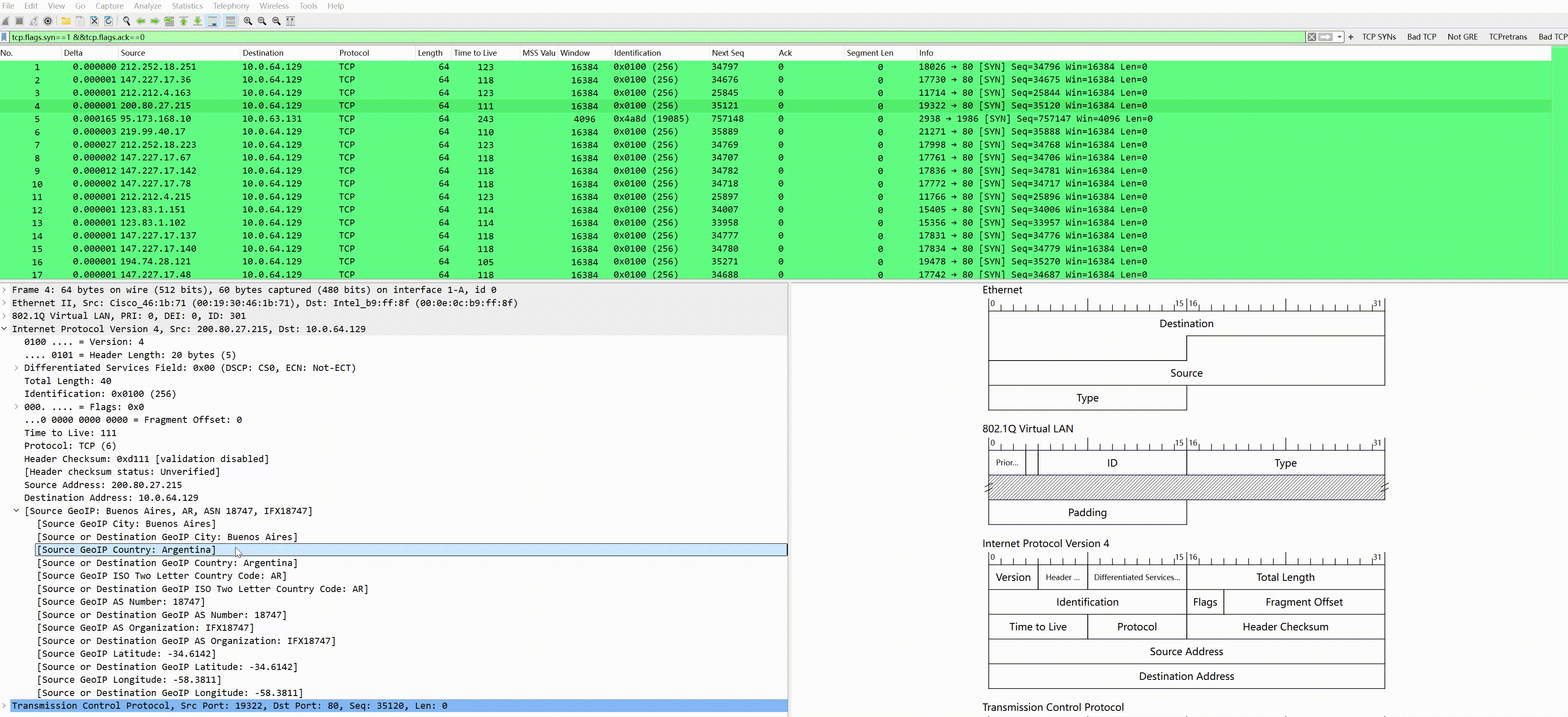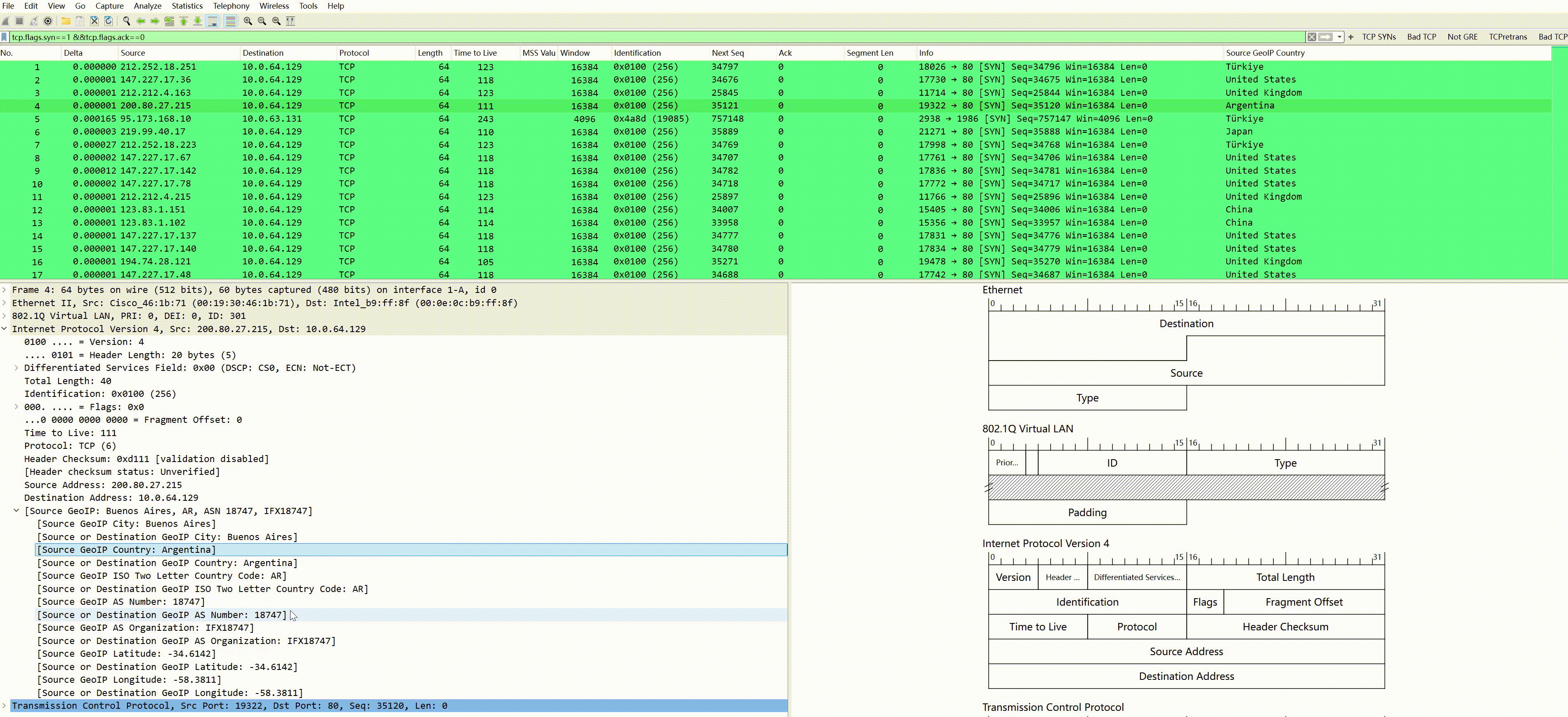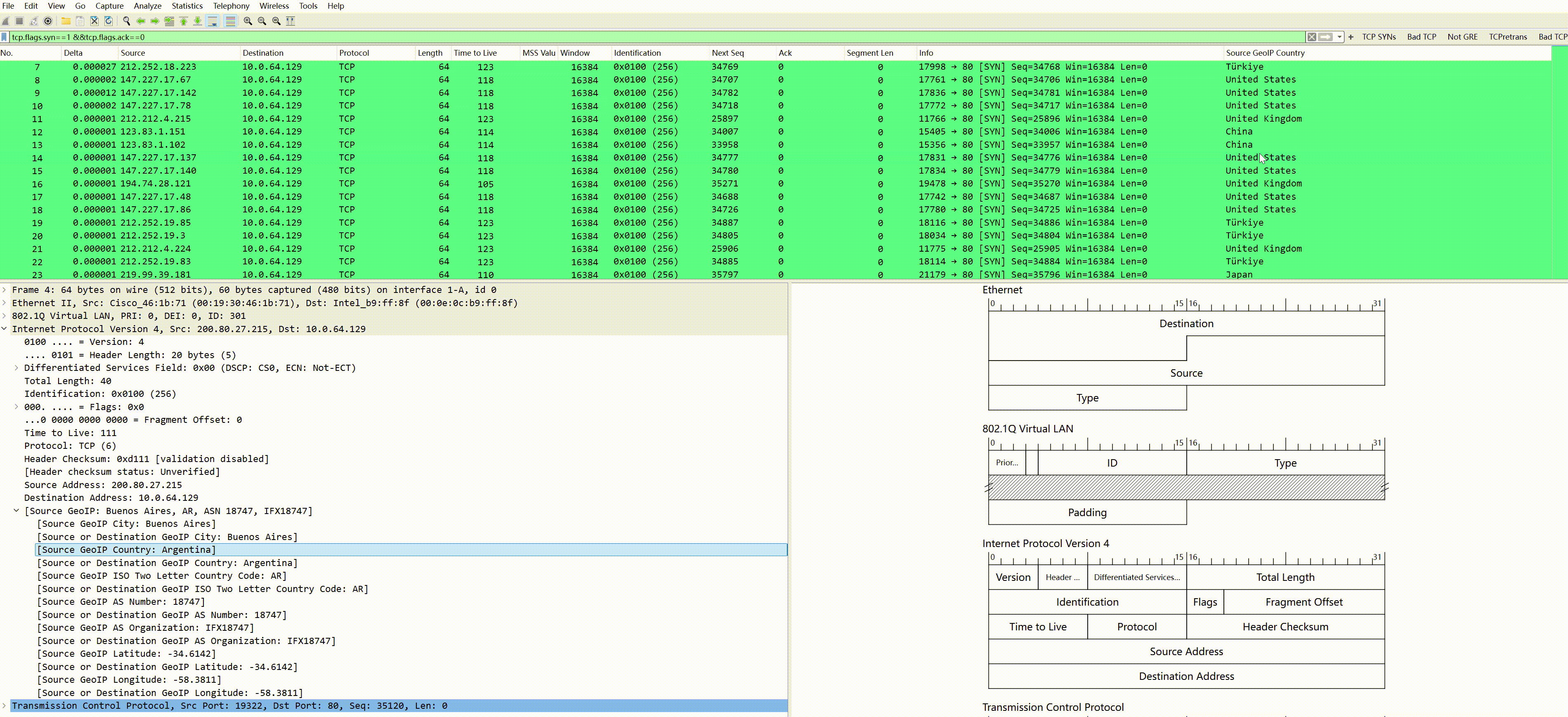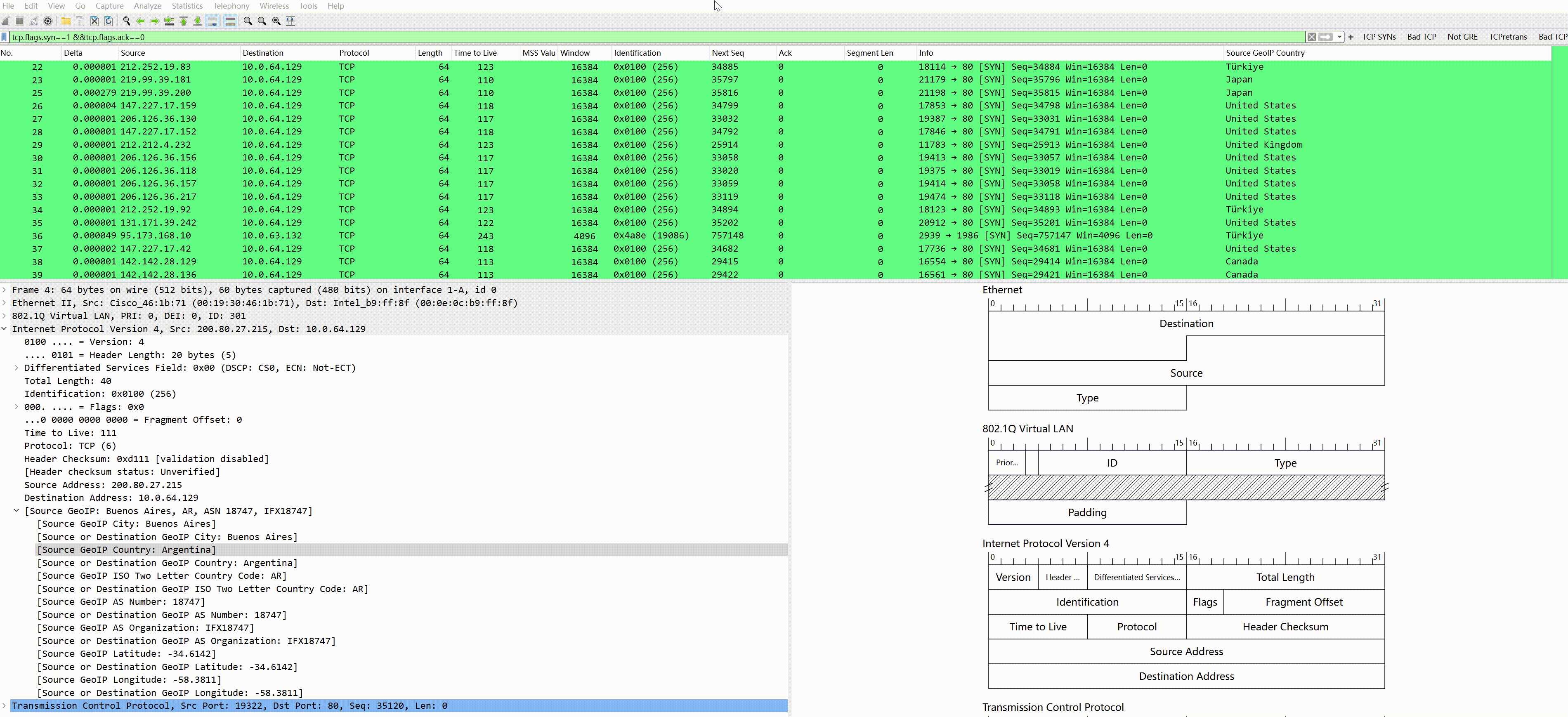
After applying as a column, you can see the source IP country displayed on the far right; other fields can be set similarly.
Viewing the Map Distribution Visualization: MaxMind Database
1. Viewing Map Distribution of MaxMind Database
In –> you can see that IP endpoints by default show the aforementioned 6 fields, namely country, city, latitude, longitude, AS number, AS number organization:

It can also generate a map distribution data, click the upper left corner -> :
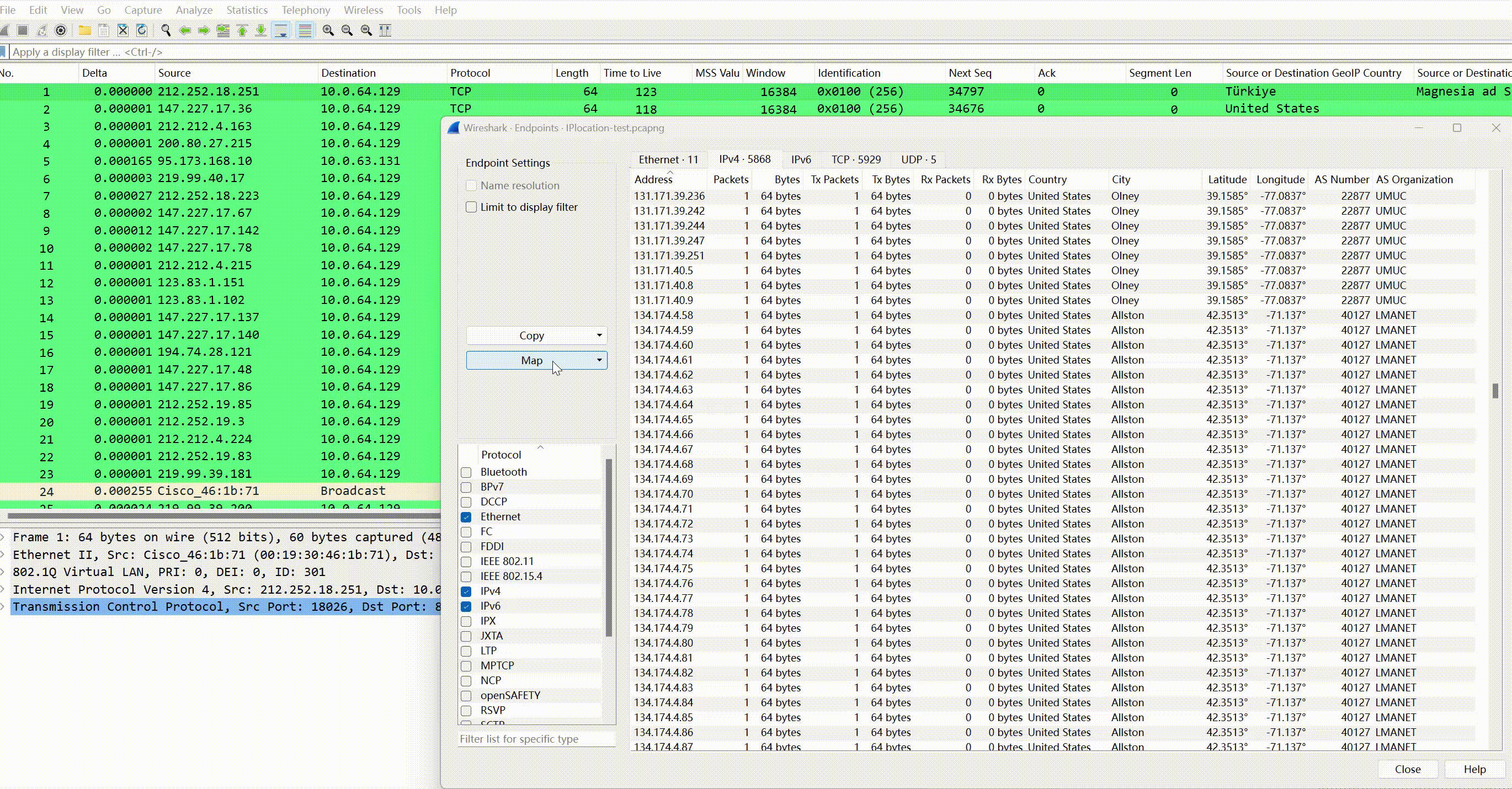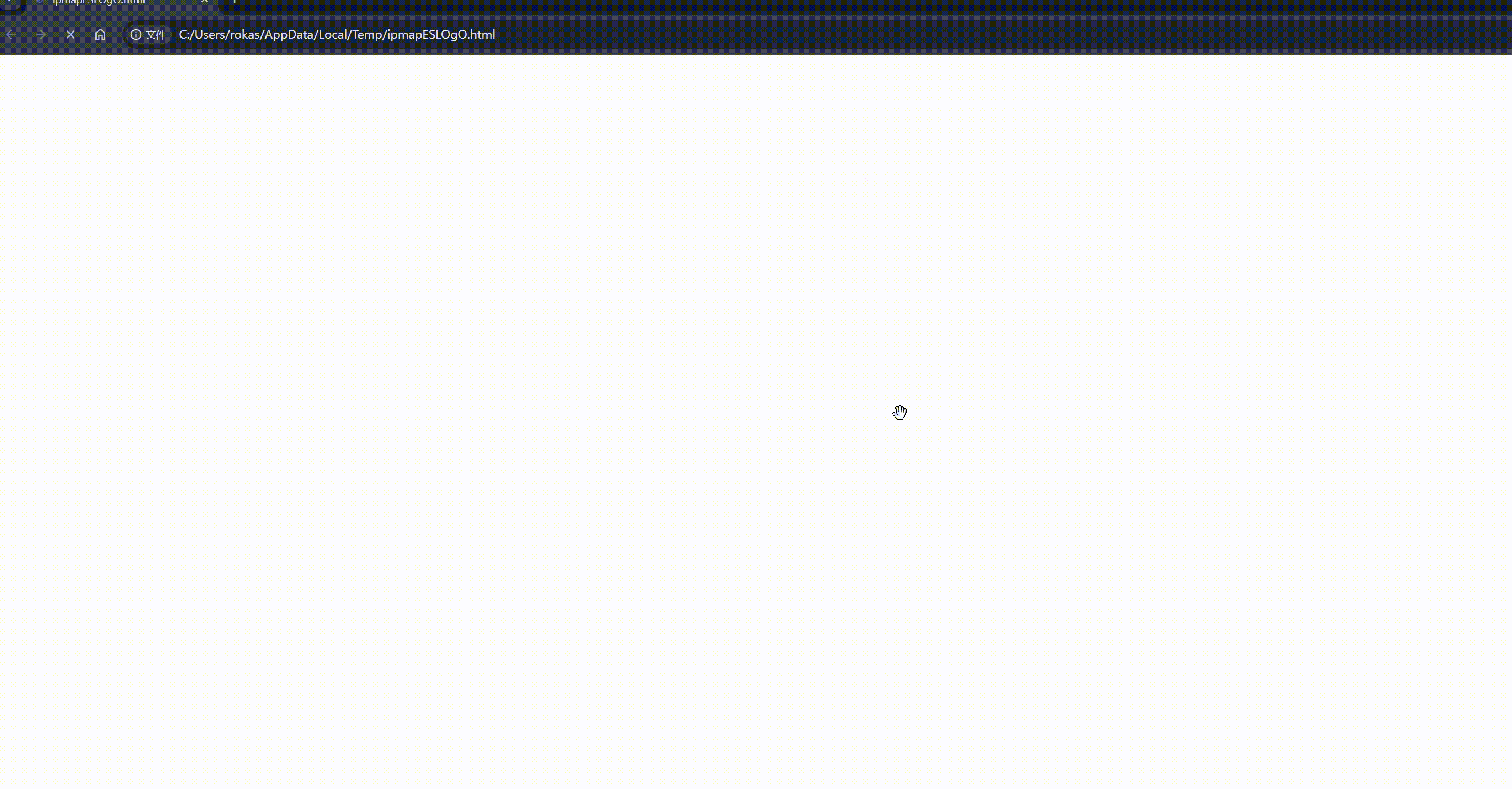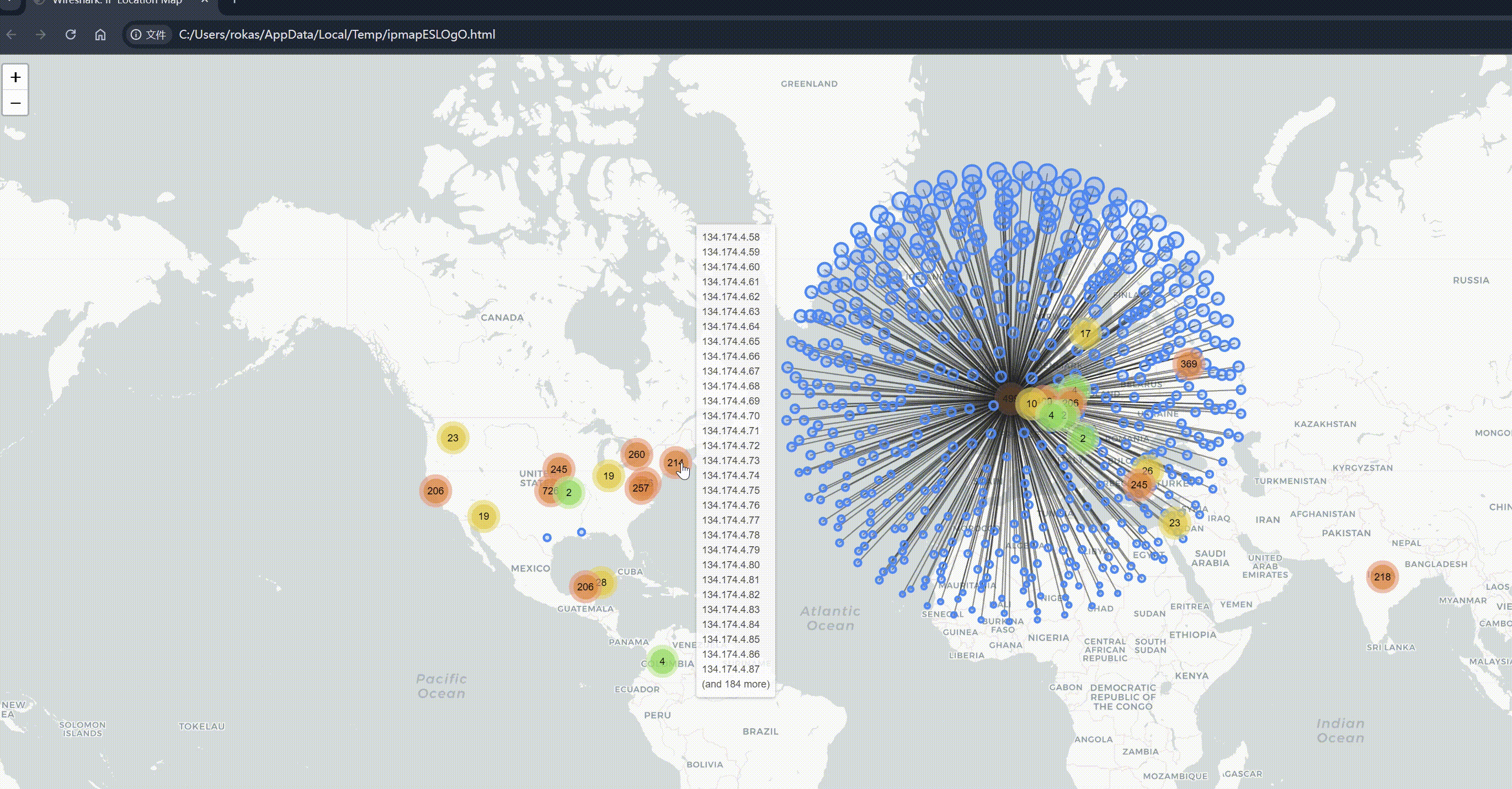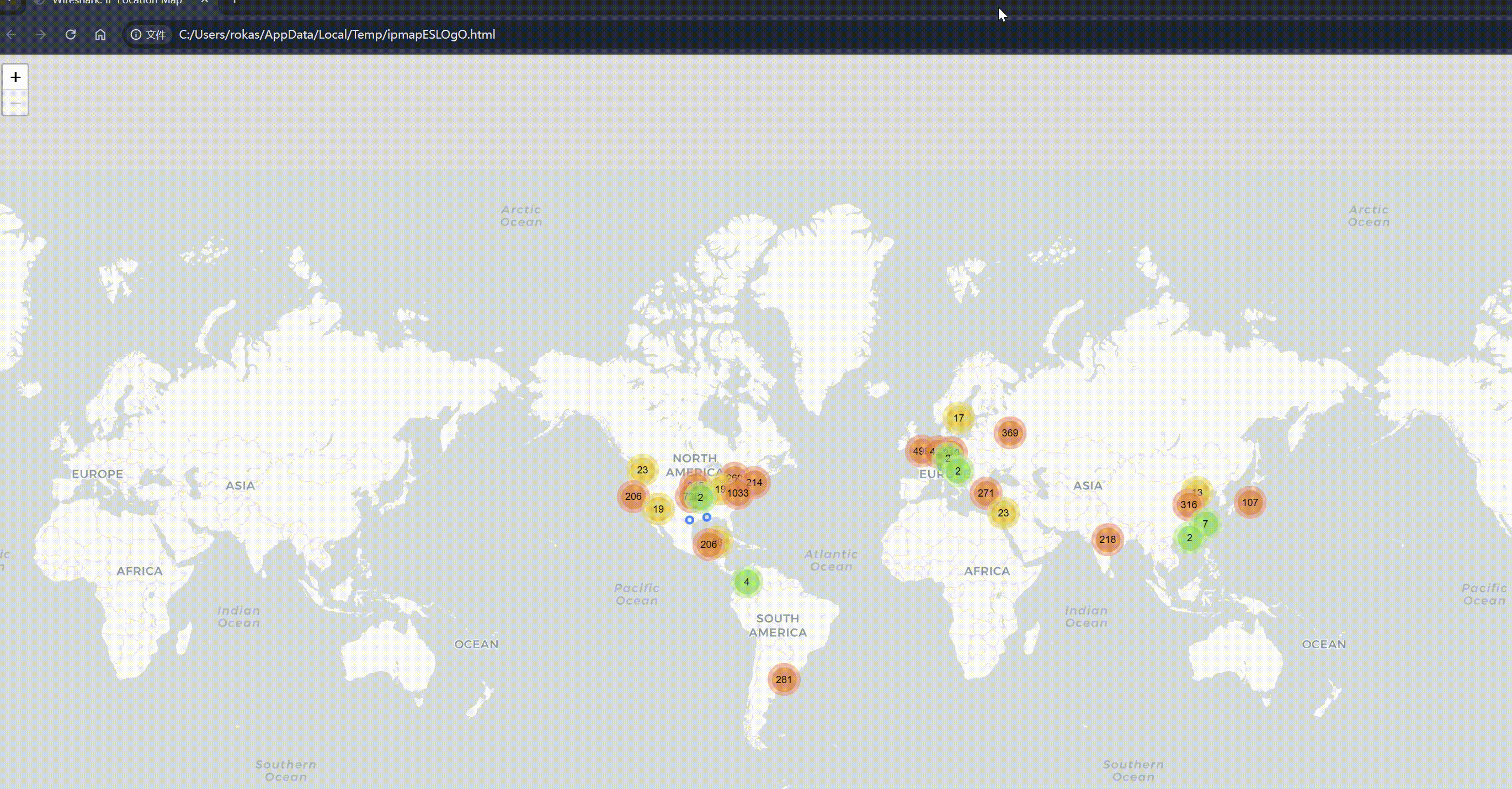
And click on each IP individually to view detailed attribute information, AS number, the organization where AS is located, country, packet count, transmitted byte count:

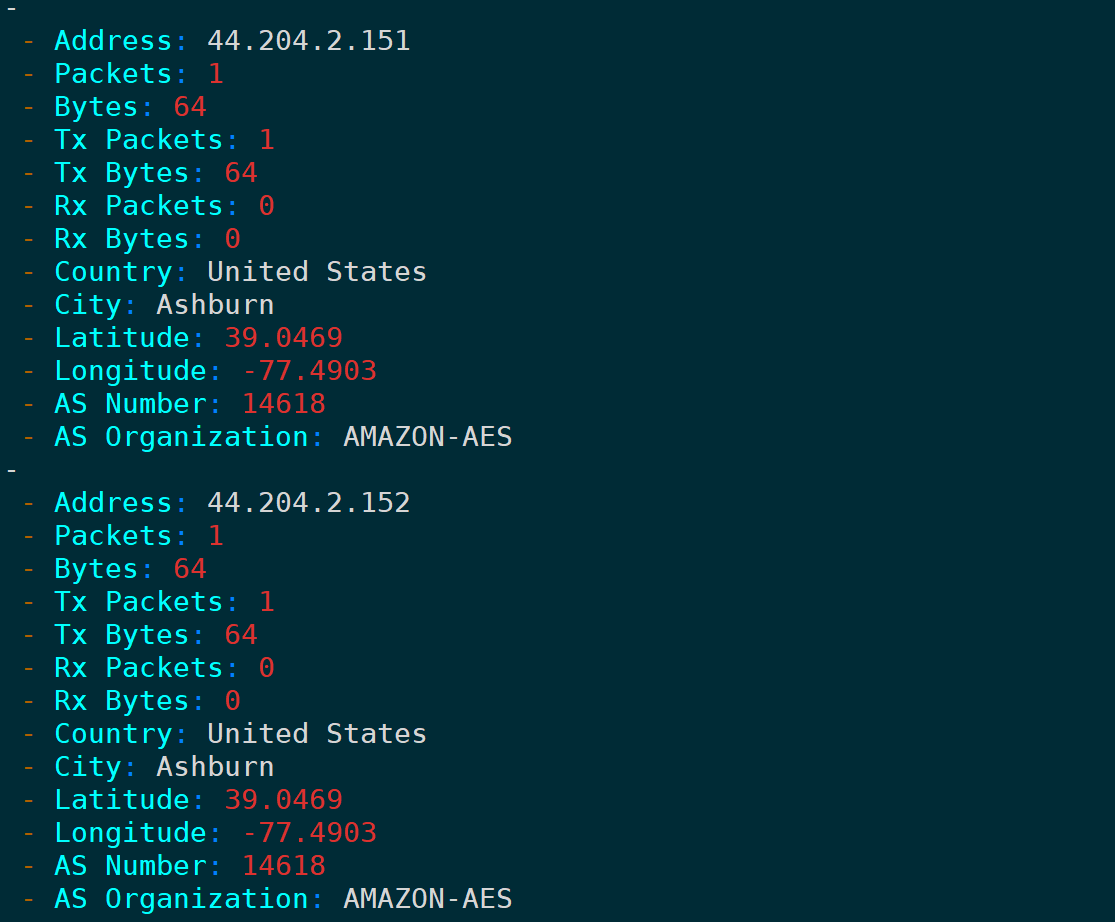
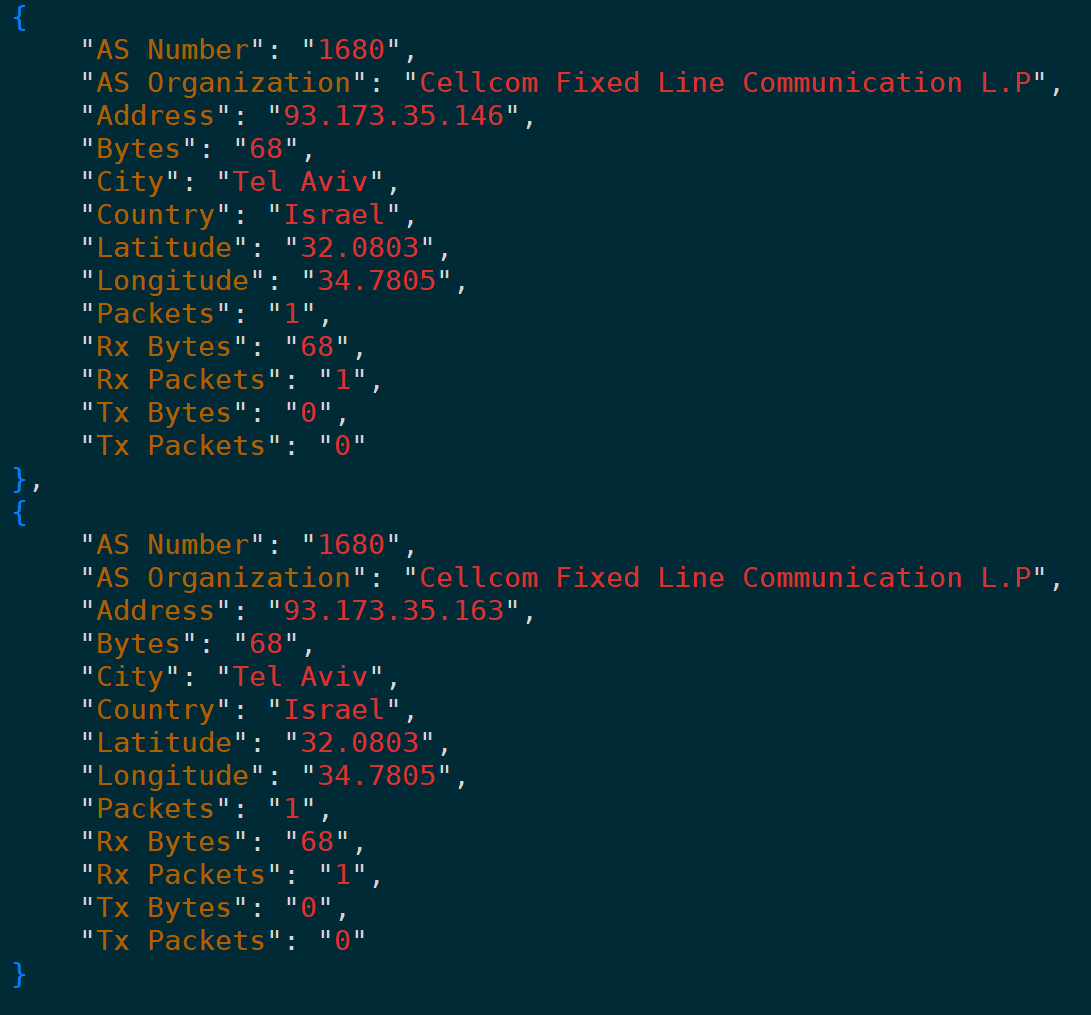
2. Copy as CSV/YAML/JSON Format
Similarly, here supports copying these data as CSV, YAML, three formats:


Filtering Packets through Database Fields
Wireshark provides 26 fields for the geoip function as filter conditions or applied as columns:
| Filter Field | Meaning |
|---|---|
| ip.geoip.asnum | Source/Destination IP AS number |
| ip.geoip.city | Source/Destination IP city |
| ip.geoip.country | Source/Destination IP country |
| ip.geoip.country_iso | Source/Destination IP country ISO two-letter code |
| ip.geoip.dst_asnum | Destination IP AS number |
| ip.geoip.dst_city | Destination IP city |
| ip.geoip.dst_country | Destination IP country |
| ip.geoip.dst_country_iso | Destination IP country ISO two-letter code |
| ip.geoip.dst_lat | Destination IP latitude |
| ip.geoip.dst_lon | Destination IP longitude |
| ip.geoip.dst_org | Destination IP AS organization |
| ip.geoip.dst_summary | Destination IP Geo summary |
| ip.geoip.lat | Source/Destination IP latitude |
| ip.geoip.lon | Source/Destination IP longitude |
| ip.geoip.org | Source/Destination IP AS organization |
| ip.geoip.src_asnum | Source IP AS number |
| ip.geoip.src_city | Source IP city |
| ip.geoip.src_country | Source IP country |
| ip.geoip.src_country_iso | Source IP country ISO two-letter code |
| ip.geoip.src_lat | Source IP latitude |
| ip.geoip.src_lon | Source IP longitude |
| ip.geoip.src_org | Source IP AS organization |
| ip.geoip.src_summary | Source IP Geo summary |
It is not difficult to find, in fixed format, fields starting with indicate source IP, those starting with indicate destination IP, and those that do not start with either indicate source or destination, followed by geographical attribute information of IP: latitude, longitude, AS number, country, city, organization, ISO two-letter code, etc.
For example, applying the country, city, and AS number of the source/destination IP as columns:
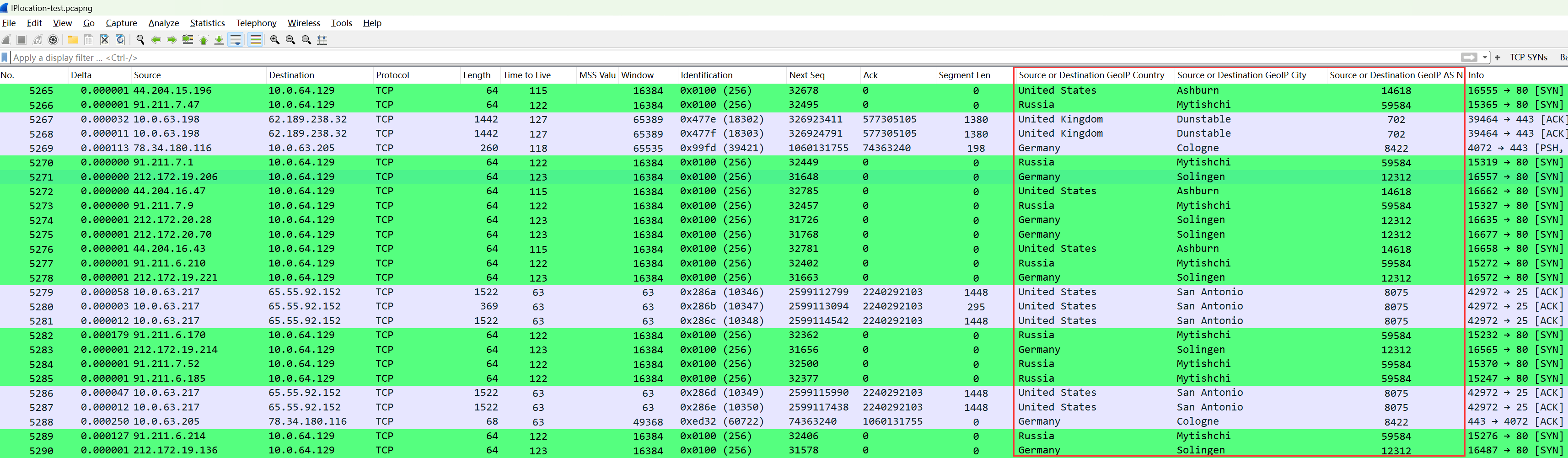
The values of these three columns use three of the above 26 filtering fields:

Since the 26 fields can be used arbitrarily, accurate filtering of packets with matching conditional features can be achieved, for example, the following scenarios.
1. Filtering Packets from Specific Countries
For example, packets from the U.S. can be filtered as:

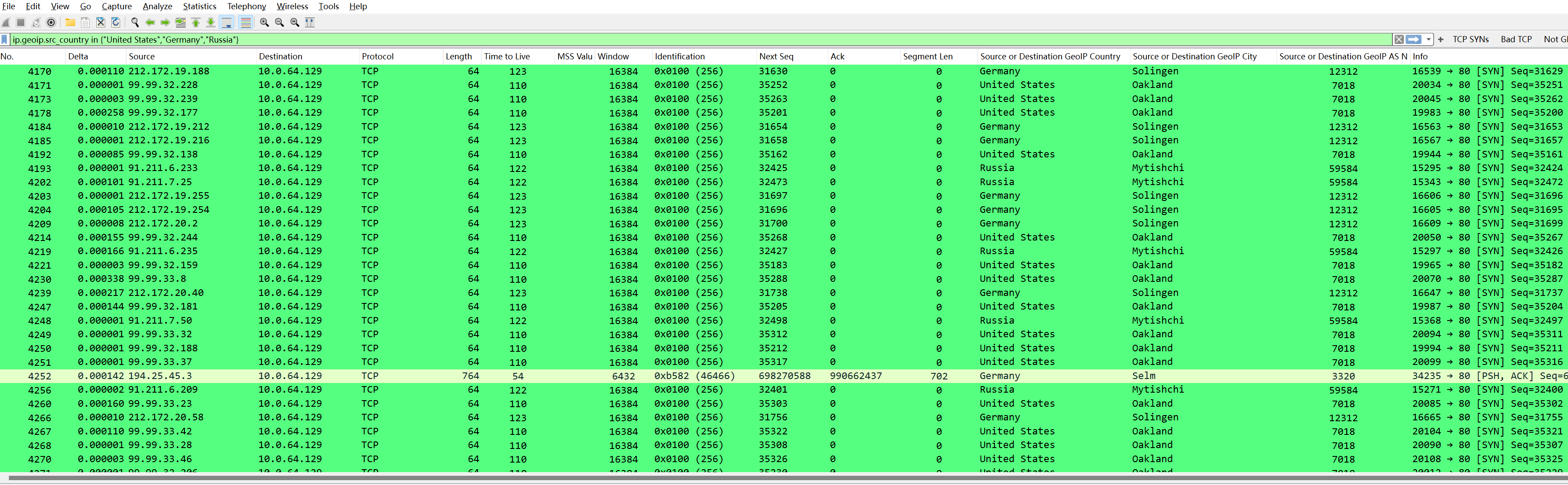
Filtering packets from the U.S., Germany, or Russia:
Of course, you can also use or statements; the effect is the same:
2. Filtering Packets from Specific Cities
Filtering packets from Ashburn can be:

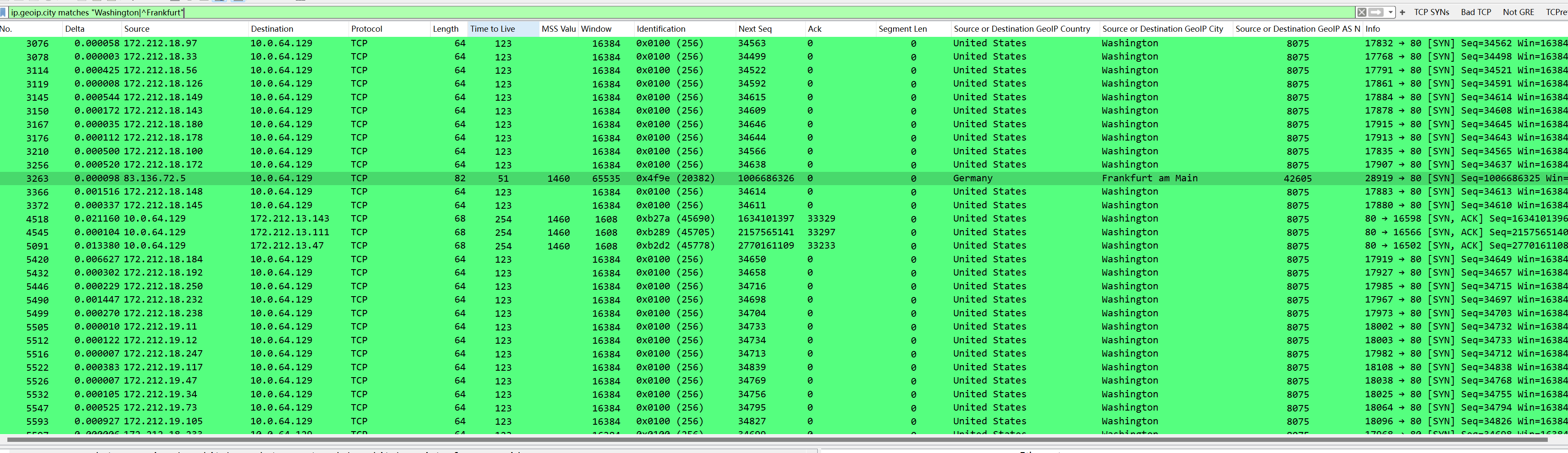
Filtering packets from Washington or Frankfurt:
Filtering packets with unresolved cities:
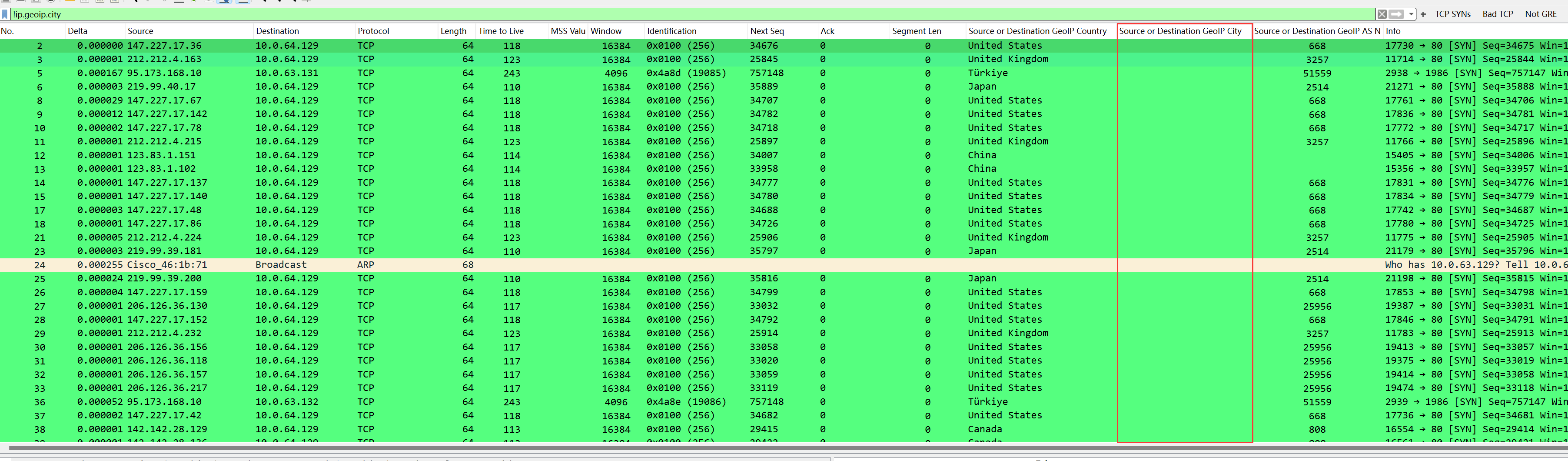
It can be seen that the city field is empty because these IPs do not have corresponding city data in the database, and the reverse filtering method for other fields is similar.
3. Filtering Packets with Specific AS Numbers
Similarly, filter packets with specific AS numbers and only select packets with SYN flag set to 1:

By searching the AS number, we can see which network segments belong to this AS; for example, 212.172.0.0/16 is included, supporting the accuracy of the database:

Conclusion
This article detailed how to combine MaxMind databases (including GeoLite2 ASN, GeoLite2 City, and GeoLite2 Country) with Wireshark for in-depth analysis of the IP geographical location information in packet capture files.
Additionally, it explained how to apply fields of interest as columns to view IP geographical information more intuitively. Furthermore, it demonstrated how to use the 26 built-in Geo-related fields of Wireshark for precise packet filtering, thereby identifying packets matching specific geographical traits.
Finally, it provided examples of viewing IP address map distribution and exporting data as CSV, YAML, and JSON formats for further data analysis and processing, significantly improving the efficiency and accuracy of analysis when dealing with network scans, DDoS attacks, and other security threats.



