Hello everyone, nice to meet you again. I am your friend, Full Stack Master. This time, we will discuss WinPcap rules.
Wireshark provides two types of filters:
Capture filter: Set the filtering conditions before capturing packets and then only capture the packets that meet the criteria.
Display filter: Set filtering conditions in the captured packet set, hide the packets you don’t want to see, and only show the packets that meet the criteria.
It is important to note that the syntax used by these two types of filters is completely different. As you might expect, capturing NIC data is not actually done by Wireshark but by WinPcap, so you need to follow WinPcap’s rules. Display filters are the way Wireshark filters the data that has already been captured.
The primary reason for using capture filters is performance. If you know you don’t need to analyze certain types of traffic, you can easily use a capture filter to filter it out, thus saving the processor resources that would be used to capture these packets. Using capture filters is particularly useful when handling large amounts of data.
The initial interface of the new version of Wireshark is very concise, primarily offering two functionalities: first set the capture filter, then select the network card responsible for capturing packets. This shows the importance of capture filters.
Wireshark intercepts all data accessed through the network card without setting any proxy
Wireshark cannot intercept requests for local loopback access, i.e., 127.0.0.1 or localhost
Display filter:
Below is the interception of HTTP requests in Wireshark, note it does not include HTTPS
http.request.uri contains “product”
Requests containing “product” in the URL address, not counting the domain name
http.host==shanghai.rongzi.com
Filter domain names
http.host contains rongzi.com
More ambiguous filtering, can have multiple subdomains
http.content_type ==”text/html”
content_type type filtering
http.request.uri==”/product/”
Complete address filtering, not suitable if there are parameters
http.request.method==”GET”
tcp.port==80
http && tcp.port==8613 or tcp.port==8090 or tcp.port==8091
ip.dst==42.159.245.203
Collection:
http.host==magentonotes.com
http.host contains magentonotes.com// Filters HTTP packets passing through the specified domain name, the host value here does not necessarily mean the domain name in the request
http.response.code==302
// Filters HTTP response packets with status code 302
http.response==1
// Filters all HTTP response packets
http.request==1
// Filters all HTTP requests, seems that http.request can also be used
http.request.method==POST//wireshark filters all HTTP request packets with the POST method, note POST is uppercase
http.cookie contains guid// Filters HTTP packets that contain a specified cookie
http.request.uri==”/online/setpoint”// Filters the requested URI, the value is the part after the domain name
http.request.full_uri==” http://task.browser.360.cn/online/setpoint”// To filter the entire URL including the domain name, use http.request.full_uri
http.server contains “nginx”// Filters packets with HTTP header field server containing the string nginx
http.content_type== “text/html”// Filters HTTP response or post packets where content_type is text/html, i.e., filters HTTP packets by file type
http.content_encoding==“gzip”// Filters HTTP packets with content_encoding as gzip
http.transfer_encoding==“chunked”// Filters based on transfer_encoding
http.content_length== 279http.content_length_header== “279″// Filters by content_length value
http.server// Filters all packets containing the server field in the HTTP header
http.request.version== “HTTP/1.1″// Filters HTTP packets of version HTTP/1.1, including requests and responses
http.response.phrase==“OK”// Filters phrases in the HTTP response
Capture Filter:
Capture–》Capture Filters
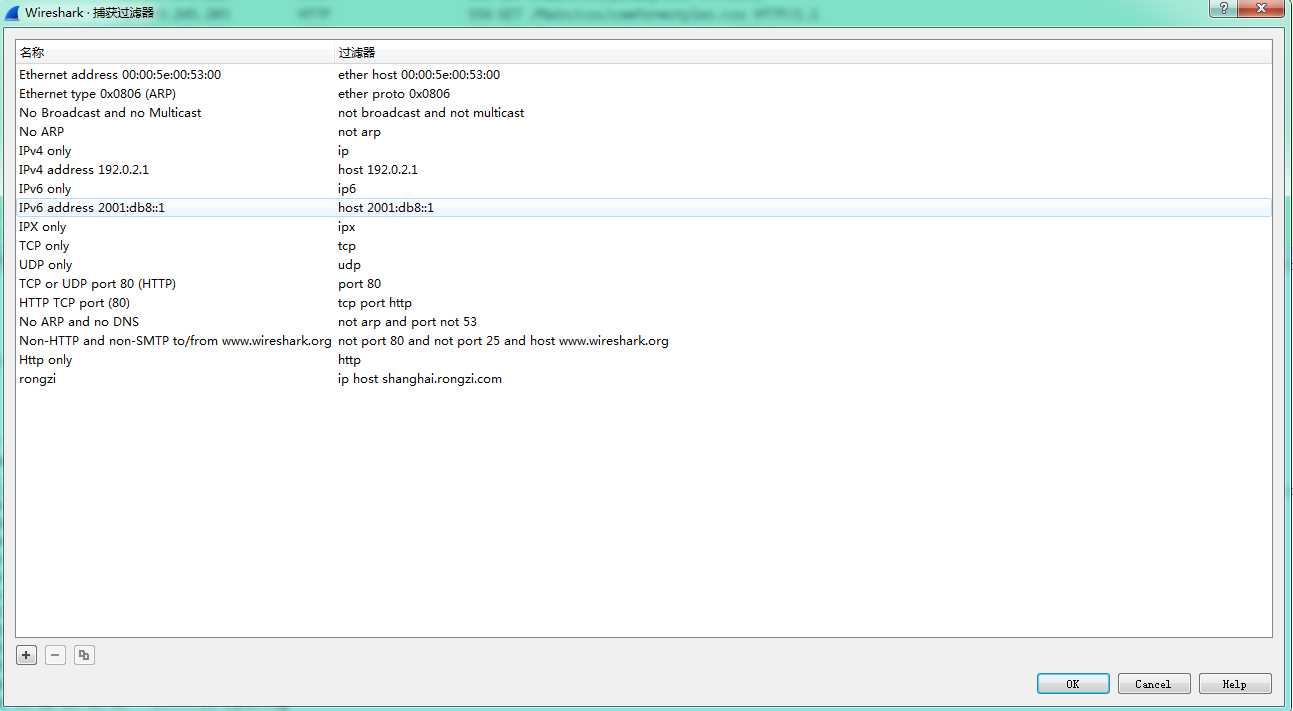
Capture–》Options–》
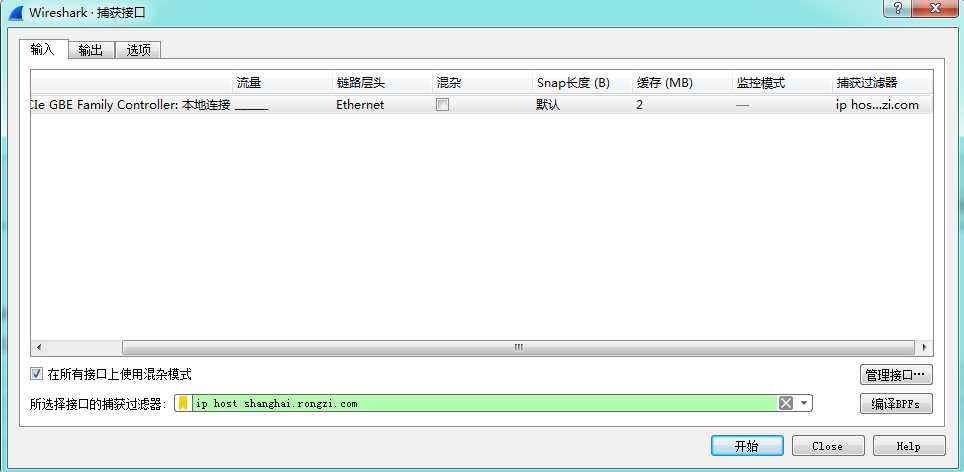
Click Start to begin capturing data.
Testing revealed that the above example uses a domain name, but in reality, it uses an IP because many different domain names with the same IP can also be captured!
You can see more specific rules in the link below, which contains many examples.
Wireshark capturing MySQL statements:
mysql.query contains “SELECT”
Filter all MySQL statement contents:
mysql contains “FD171290339530899459”
Filter data in TCP
tcp.payload contains “sendAppPushMsg”
Publisher: Full Stack Programmer Stack Leader, please indicate the source for reposting: https://javaforall.cn/158474.html Original link: https://javaforall.cn



